Use of RPA and AI-based Predictive Models in Workforce Automation and Performance Management
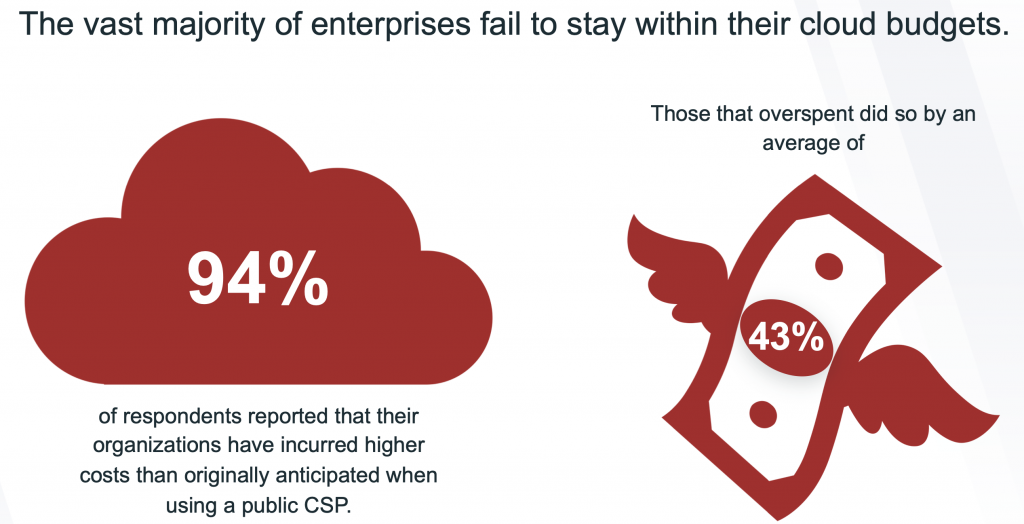
Robots taking over the world? Well, not exactly. But they are definitely revolutionizing the way we work and increasing efficiency across industries. RPA is a game-changing technology that is streamlining repetitive tasks and freeing up human resources for more meaningful work. From accurate data processing to consistent task execution, automating half of workforce planning, and performance management, leading to various benefits such as increased efficiency, cost reduction, and improved workforce resilience through targeted performance management, RPA offers a wide range of benefits that can transform your business operations.
Let’s explore the exciting use cases of robotics process automation and how this non-invasive technology can help achieve your goals:
Workforce Planning Automation:
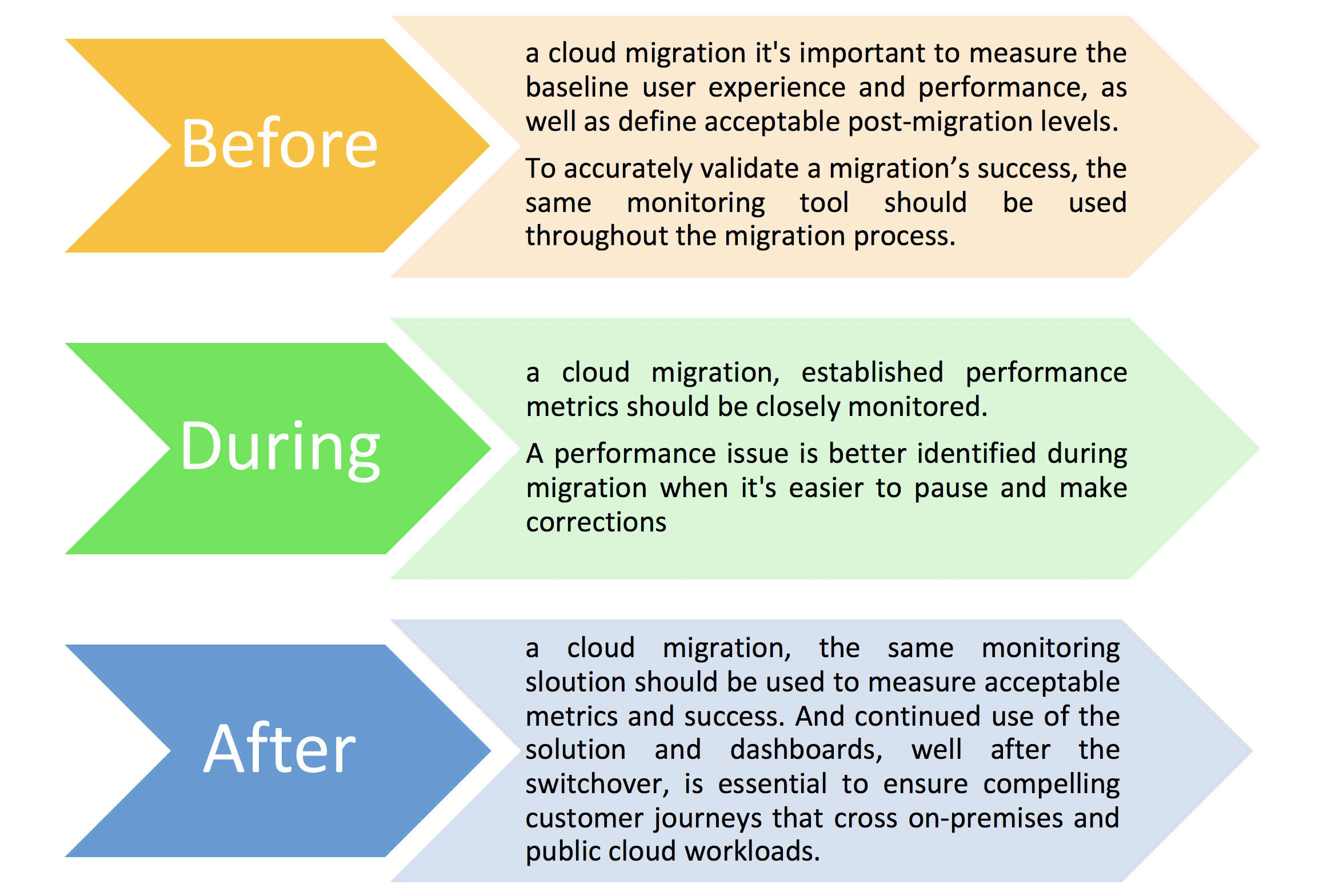
- RPA can automate repetitive and rule-based tasks involved in workforce planning, such as data gathering, analysis, and reporting. For example, it can extract employee data from multiple systems, compile it into a centralized database, and generate reports automatically. One of the key benefits of RPA is its accuracy. Bots follow predefined rules and instructions meticulously, ensuring precise execution every time. This eliminates costly errors caused by human fatigue or oversight. With RPA in place, you can trust that your data will be processed accurately without any discrepancies.
- AI-based predictive models can analyze historical data and external factors to forecast workforce demand and supply. This enables organizations to optimize workforce size, identify skill gaps, and plan for future needs more accurately. Plus with its low technical barrier you don’t need to have extensive programming knowledge or coding skills to implement it within your organization. The intuitive design interfaces make it accessible for non-technical users as well, allowing them to create automated workflows easily.
Performance Management Automation:
- RPA can automate administrative tasks related to performance management, such as performance appraisal forms generation, data consolidation, and feedback distribution. This reduces manual effort, improves accuracy, and saves time for HR professionals and managers. Additionally, in terms of productivity gains, RPA enables faster task completion times compared to manual efforts alone. With bots handling repetitive tasks efficiently round-the-clock, employees are freed up from mundane activities and can focus on strategic initiatives that require creativity and critical thinking.
- AI-based models can analyze performance data, feedback, and contextual factors to provide valuable insights and recommendations. For instance, they can identify high-performing employees, flag performance issues, and suggest personalized development plans. Moreover, relying on robots ensures reliability in task execution as they consistently follow standard operating procedures (SOPs) without deviation or shortcuts. This leads not only to increased efficiency but also improves customer satisfaction due to quicker response times and accurate deliverables.
Cost Reduction through Efficiency:
- By automating workforce planning and performance management processes, organizations can save time and effort, leading to increased productivity and efficiency. This enables HR professionals and managers to focus on higher-value tasks, such as strategic workforce planning and talent development.
- RPA reduces the need for manual data entry and processing, minimizing errors and rework. This improves data accuracy and reduces the associated costs of correcting mistakes.
- AI-based predictive models help optimize resource allocation, workforce utilization, and talent acquisition, ensuring that organizations have the right people in the right roles at the right time. This reduces unnecessary costs and maximizes operational efficiency.
Improved Workforce Resilience through Targeted Performance Management:
- AI-based models can analyze performance data and identify patterns, enabling organizations to proactively address performance issues and mitigate risks.
- By providing targeted feedback and personalized development plans, AI can help employees enhance their skills, increase job satisfaction, and improve overall performance. This contributes to a more resilient workforce that can adapt to changing business needs.
RPA is also a non-invasive technology that seamlessly integrates with existing systems and applications without disrupting their functionality. This means you don’t have to completely overhaul your IT infrastructure to leverage its benefits. By working alongside your existing tools, RPA enhances operational efficiency without causing any major disruptions or downtime. In summary, the combination of RPA and AI-based predictive models in workforce planning and performance management can automate repetitive tasks, improve efficiency, reduce costs, and enhance workforce resilience through targeted interventions and data-driven insights.