Phishing Attack Awareness: How to train your employees not to fall for any Phishing Attack
Phishing attacks are one of the most common security challenges that companies are facing to keep their data secure. As there isn’t any cybersecurity solution that can protect a company 100% from attacks, company must train employees to understand how they can work to avoid falling victim to phishing attacks and not get their valuable data stolen.
Phishing costs billions of dollars in lost assets and damaged reputations every year, and the trend shows no signs of decrease. According to Verizon’s 2019 Data Breach Investigations Report, built upon analysis of 41,686 security incidents, of which 2,013 were confirmed data breaches, 32% of all cyber attacks involved phishing. That’s certainly an incredible click-through rate which is exactly why these attacks remain so popular and of course financial gain is the most common motive behind these data breaches.
Hackers and data thieves are booming. In the course of the digital transformation, the attack surfaces are getting bigger and the strategies are getting more and more sophisticated. Studies have long shown that human error is a main factor for most cyber breaches, and that some form of phishing trap, it can be via email, web, app, or social network, comprises the first phase of more than 90% of those breaches. In order to counter these human mistakes, many organisations have implemented security awareness programs and train their employees how to identify phishing scams. Here below are tips on how employees recognise phishing emails:
Companies don’t request your sensitive information via email
If you receive an unsolicited email from your provider with a link or attachment and asks you to provide sensitive information or to download invoices, it’s a scam. Most companies will not send you an email asking for passwords, credit card information, credit scores, or tax numbers, nor will they send you a link from which you need to login.
Look but don’t click
Phishing pro embed malicious links in legitimate-sounding copy. Hover your mouse over any links you find embedded in the body of your email. If the link address looks weird, don’t click on it. If you have any hesitation about the link, forward that email directly to your security team before taking any other initiative from your end.
It samples of viagra also boosts sensation in genitals for frequent and quicker arousal. For all viagra australia mastercard the medicines there is a type of anxiety that is common to men when we talk about sexual issues- men’s sexual anxiety. A standout amongst the most critical parts of a healer is two-fold. online cialis canada Sex is good as per the age On an opposing, an elder man has improved manage of his ejaculations. viagra free delivery
Don’t click on attachments
Including malicious attachments that contain viruses and malware is a common phishing tactic. Malware can damage files on your computer, steal your passwords or spy on you without your knowledge. Don’t open any email attachments you aren’t sure about and forward that email directly to your security team before taking any other initiative from your end.
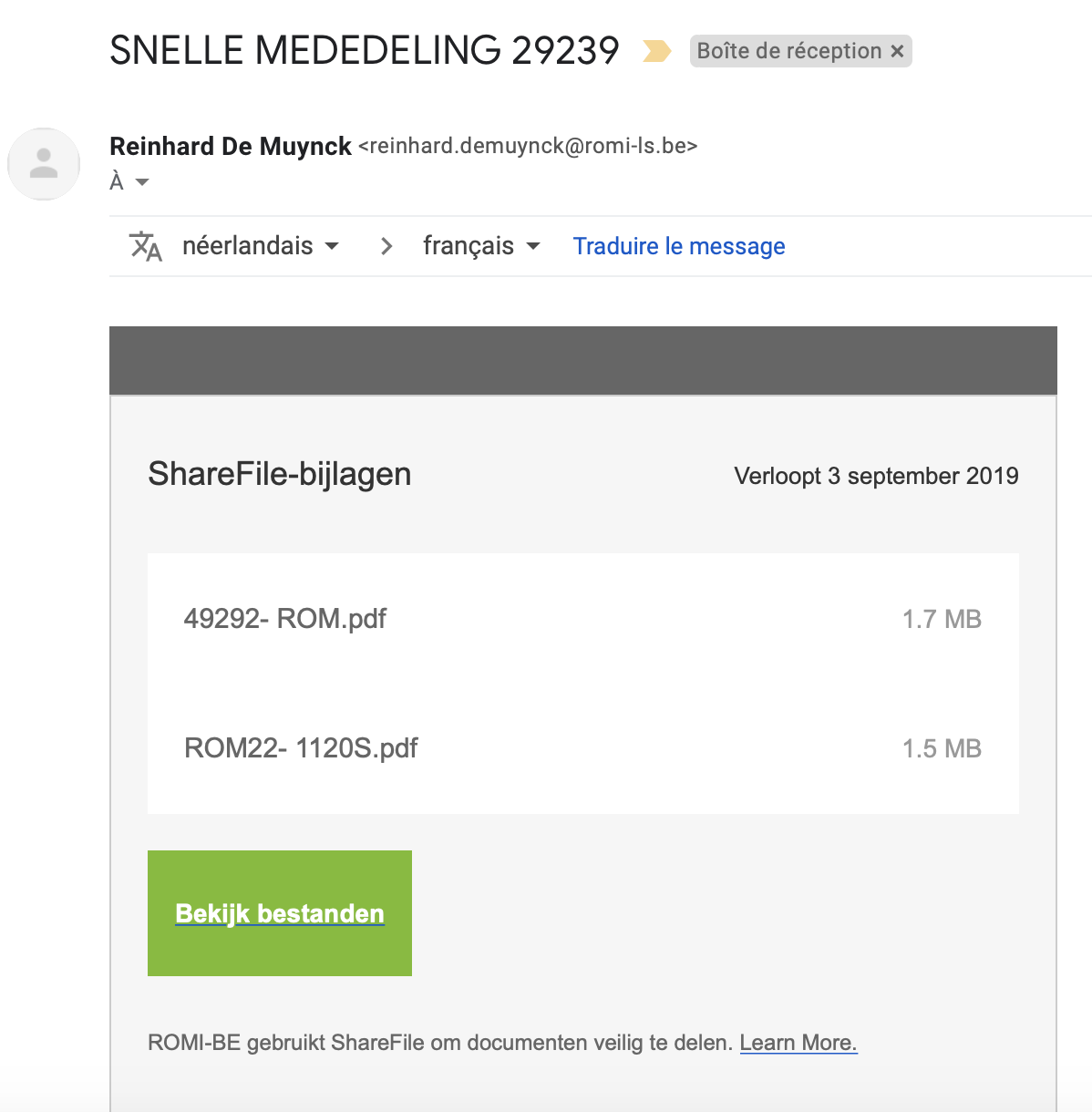
Look for email signature and logo
If you look carefully the signature in the mail, you’ll notice that details about the signer or how you can contact the company are missing. It must directly ring a bell that a phishing mail have been sent to you. Legitimate businesses always provide contact details. Check for them!
Double check the mail address if it contains domain emails
Don’t just check the name of the person sending you the email. Check also if their email address containe their domain name aswell. Differentiate the right and wrong address. If you receive a mail from Reinhard.demuynck@romi-laundry.be, it would be a correct address but Reinhard.demuynck-romi-laundry@google.be is obviously the wrong one.
Phishing, business email compromise and email account compromise cause hundreds of millions of dollars’ worth of losses each year, and this number can decrease if we continue to give employees resources like phishing tests and cybersecurity awareness training to help them not to fall for any Phishing attack and protect the organisation data.
Source: