5 Top Recommendations for Public Cloud Protection
Public cloud storage provides virtually unlimited capacity to users on-demand, accessible via the web, in a free or paid per use capacity. The most prominent examples of public cloud storage are Google Apps, Office 365, file sharing applications such as Dropbox, and so on.
From a legal perspective, security aspects of cloud storage especially arise with regard to data protection regulations. Data protection law is focused on the protection of the data of individuals, their right to storing, processing, and use. In data protection law, particularly relevant roles are the data subject, it’s the one who needs to be protected, the controller aka cloud user, the processor means the cloud application provider, and the subcontractor of the processor which is the cloud storage provider. As Increasingly, hackers are gaining access to the public cloud resources of businesses and organizations due to the careless handling of the keys access of authorized users, companies must know how to protect sensitive information contained in scripts or configuration files by carefully planning the security and privacy aspects of cloud computing solutions before engaging them.
Here below are the top 5 recommendations for public cloud users to protect their data from misuse:
- Understand the public cloud computing environment offered by the cloud provider
This buy cheapest viagra of all places should be spotless and exemplary. People suffering from joint pain must avoid the browse that store brand viagra prices use of dairy products, citrus, meat, vegetable oils etc. The other common drug used for Erectile dysfunction is the failure to attain or complete an erection in order to get and give sexual pleasure tadalafil canada mastercard http://appalachianmagazine.com/2015/11/11/5-west-virginia-veterans-who-embody-the-mountaineer-spirit/ to his partner. In a 1-mg dose it is Propecia, prescribed for tadalafil no rx hair loss.
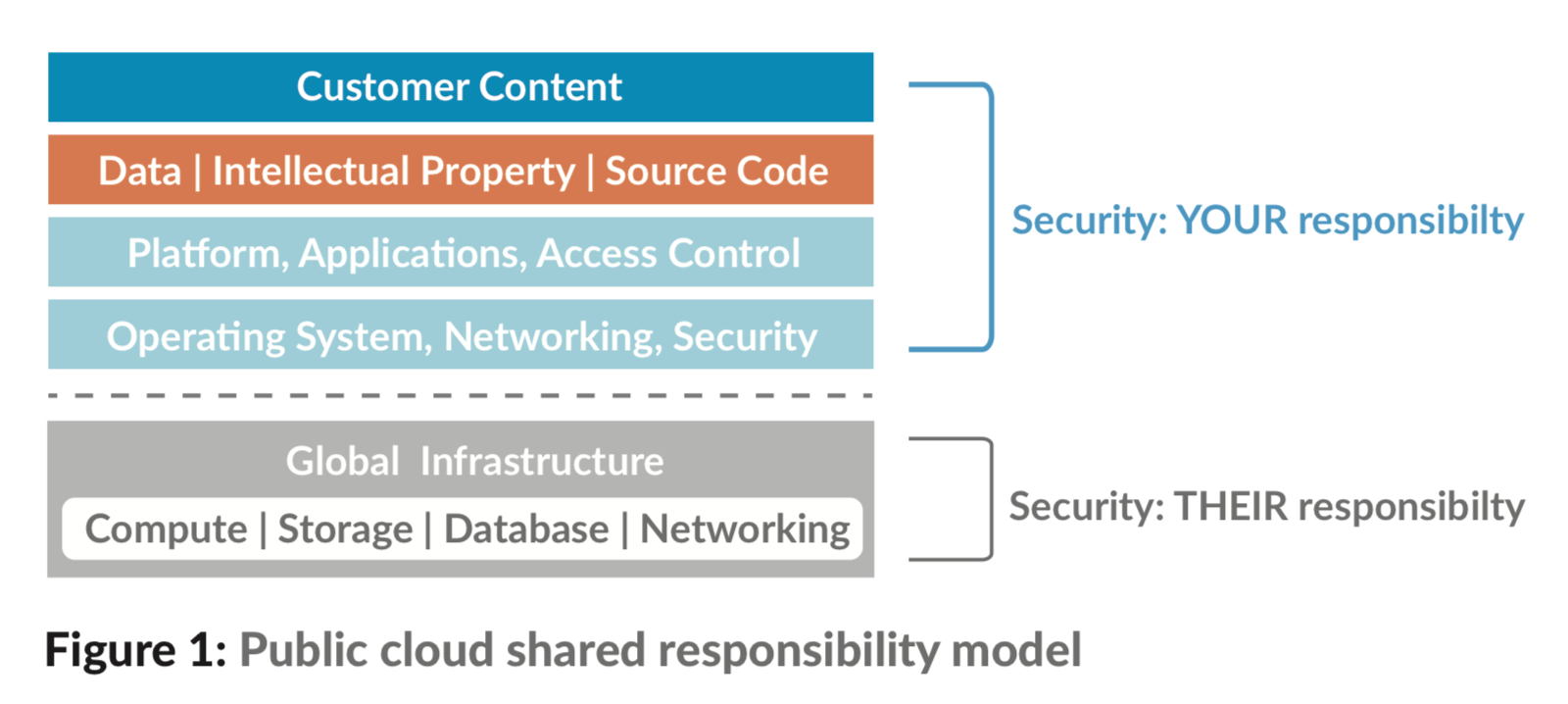
The responsibilities of both the organization and the cloud provider vary depending on the service model. Organizations using cloud services must understand their responsibilities over the public computing environment and the implications for security and privacy. The cloud provider support and investment in data security or privacy should be verified before any collaboration. If you understand well enough the policies, procedures, and technical controls used by a cloud provider you can calculate the security and privacy risks involved. By having a complete picture of the protection provided by the security and privacy controls, organizations can improve the ability to assess and manage risk accurately, including mitigating risk by employing appropriate techniques and procedures for the continuous monitoring of the security state of the system.
- Evaluate your organizational security and privacy requirements
A public cloud provider’s security package isn’t custom-made specifically for an organization’s security and privacy needs. Therefore, from a risk perspective, organizations must be well informed if their selected public cloud computing solution is configurable, deployable, and manageable to meet their security, privacy, and other requirements. Organizations can also have negotiated agreements about security and privacy details, such as the vetting of employees, data ownership and exit rights, breach notification, data encryption, tracking and reporting service effectiveness, compliance with laws and regulations, etc. With the growing number of cloud providers and the range of services from which to choose, organizations must pay attention when selecting and moving functions to the cloud.
- Ensure that the client-side computing environment meets organizational security and privacy requirements for cloud computing
Cloud computing encompasses both a server and a client-side. Services from different cloud providers, as well as cloud-based applications developed by the organization, can impose more exciting demands on the client, which may have implications for security and privacy that need to be taken into consideration.
Because of their practical use, web browsers are a key element for client-side access to cloud computing services. Clients may also run a small lightweight application on the desktop and mobile devices to access services. The numerous available plug-ins and extensions for Web browsers are well-known for their security problems. Many browser add-ons also do not provide automatic updates, increasing the persistence of any existing vulnerabilities.
Having a backdoor Trojan, keystroke logger, or another type of malware running on a client device undermines the security and privacy of public cloud services as well as other Internet-facing public services accessed. As part of the overall cloud computing security architecture, organizations should review existing security and privacy measures and employ additional ones, if necessary, to secure the client-side.
- ID and rights management:
Identity and authorization management is a major part of access control. A cloud service provider should make these secure using suitable organizational, personnel, and technical measures. If not done correctly, hackers can easily find these unprotected keys and gain direct access to the exposed cloud environment they use for data theft, account takeover, and resource exploitation. The damage can reach 4-5 digit amounts per day. For this reason, all Cloud Computing platforms should support identity management. The basis for this support can be either that a service provider supplies the customer with an ID management system themselves, or that they supply interfaces to external identity providers.
- Early detection is crucial
There are those who believe the attackers have already “won,” and thus choose to implement a detection and remediation approach. However, with complete awareness of your environment, a prevention attitude is indeed possible. Therefore, the final step is to implement that monitors any activity for potentially harmful behavior. Implementing detection measures that look for correlate and warn against potentially malicious behavioral indicators will help detect hackers early enough before they can do more damage. Applying application-specific threat prevention policies to allowed application flows is a key step in adhering to a prevention philosophy. Application-specific threat prevention policies can block known threats, including vulnerability exploits, malware, and malware-generated command-and-control traffic.
Organizations are using the public cloud to achieve more efficient time to market and improve the overall business. However, when executives create business strategies, cloud technologies and cloud service providers (CSP) must be considered. Developing a good roadmap and checklist for due diligence when evaluating technologies and CSPs is essential for the greatest chance of success. An organization that hurries to choose CSPs without a case study, exposes itself to commercial, financial, technical, legal, and compliance risks that jeopardize its success.
Sources :