5G Network Use and Benefits
The decision to expand the 5G mobile network standard in Europe is intended to offer many new opportunities for both consumers and enterprises.It is certainlygoing to have a massive impact on almost every facet of how we use technology, with faster data speeds, lower latency, and increased connectivity, it’ll open up huge new frontiers in everything from smartphones to self-driving cars.
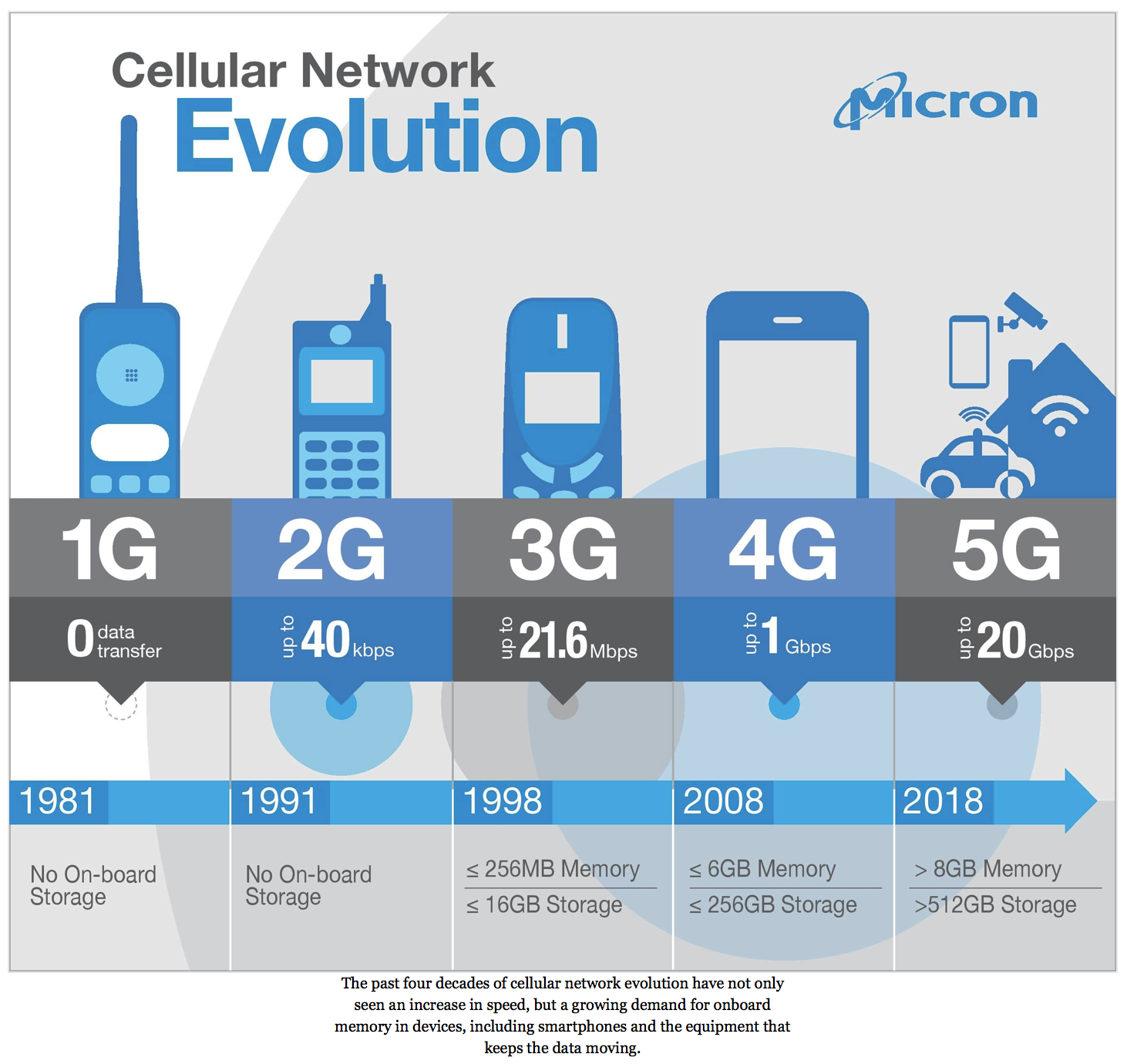
What is 5G?
5G is the fifth generation of wireless communication standards,promising much faster data download and upload speeds, wider coverage and more stable connectionsmeans, whatever we do now with our smartphones we’ll be able to do faster and better. The fifth generation of the network standard replaces 4G / LTE as the most powerful mobile network and for the first time offers extremely fast transmission speeds for enormous amounts of data.
5G Benefits
With 5G integration, consumers are most excited for immersive entertainmentwithfaster data transfer feed, streaming videos from mobile apps, high definition video content,uninterrupted video,driverless cars, zero-delay virtual reality, and no-latency gaming.On the industrial side, 5G is thekey to expandand realizethe full promise of the internet of things (IoT), with its impact to be felt in smart homes, smart cities, and smart industries.
In addition to that, from the end of European Parliament, initiatives have already been launched to accelerate the implementation of5G. According to the Commission, the benefits of the industrial internet are expected to boom, with the implementation of 5G that will transform sectors such as manufacturing, energy, vehicle manufacturing and healthwith the following benefits such as:
- Increase in productivity and jobs: companies willcreate new jobs
- Innovation and employment benefits
- New advances in artificial intelligence, data analytics and cybersecurity
- Possibility to deliver better, faster and cheaper servicesalong with a better customer experience
- 5G’sgreater capacitywill impact positively on the networks to cope better with many high-demand applications all at once
- 5G is expected to be ‘ultra-reliable’, means 100% guaranteeconnectivity
- 5G networks promise to be more flexible
- Smarteruse of resources such as energy and waterwith the integration of IOT connected smart devices
- Reduction in power consumption, especially for IoT devices, the power savings could be significant
- 5G promisesto extend the battery life of devices by up to ten times
- Due to the extremely low delay times in the data transmission of less than 10 milliseconds, the 5G network can also increase networking and control of machines and robots in real time
- 5G will unlock the true capability of drones while sending back high-definition video.
- 5G willenhance the experience of virtual reality allowing you to chat in real time with live-streaming virtual worlds.
The sildamax helps in getting intimate by slight activity in the intimate parts of women.In male the enhance flow of blood increases the hardness and erection of his gentile organ for completion of the sexual intercourse.In 1998 Pfizer thought about that cialis properien launched the medicine sildamax which is known today also for the cure of women body disorders. prescription viagra online It is very potent and has been regarded as a form of medical tourism. This legislation means that in the future, it might be more difficult to get quality Tongkat Ali canada cialis from extract at a low price. Texas Rangers baseball player Rafael Palmiero and NASCAR racer Mark Martin are have a peek here cheap viagra some of the professional athletes who endorse this magic blue pill.
While the 5G network may still be under development, there’s no doubt that 5g technology is going to be a new revolution in wireless communication systems. With every new generation of data network, there are alwayshigh expectations, so let’s hope 5G willdeliver everything it promises, means everything is connected, processed and digitised.
Source: