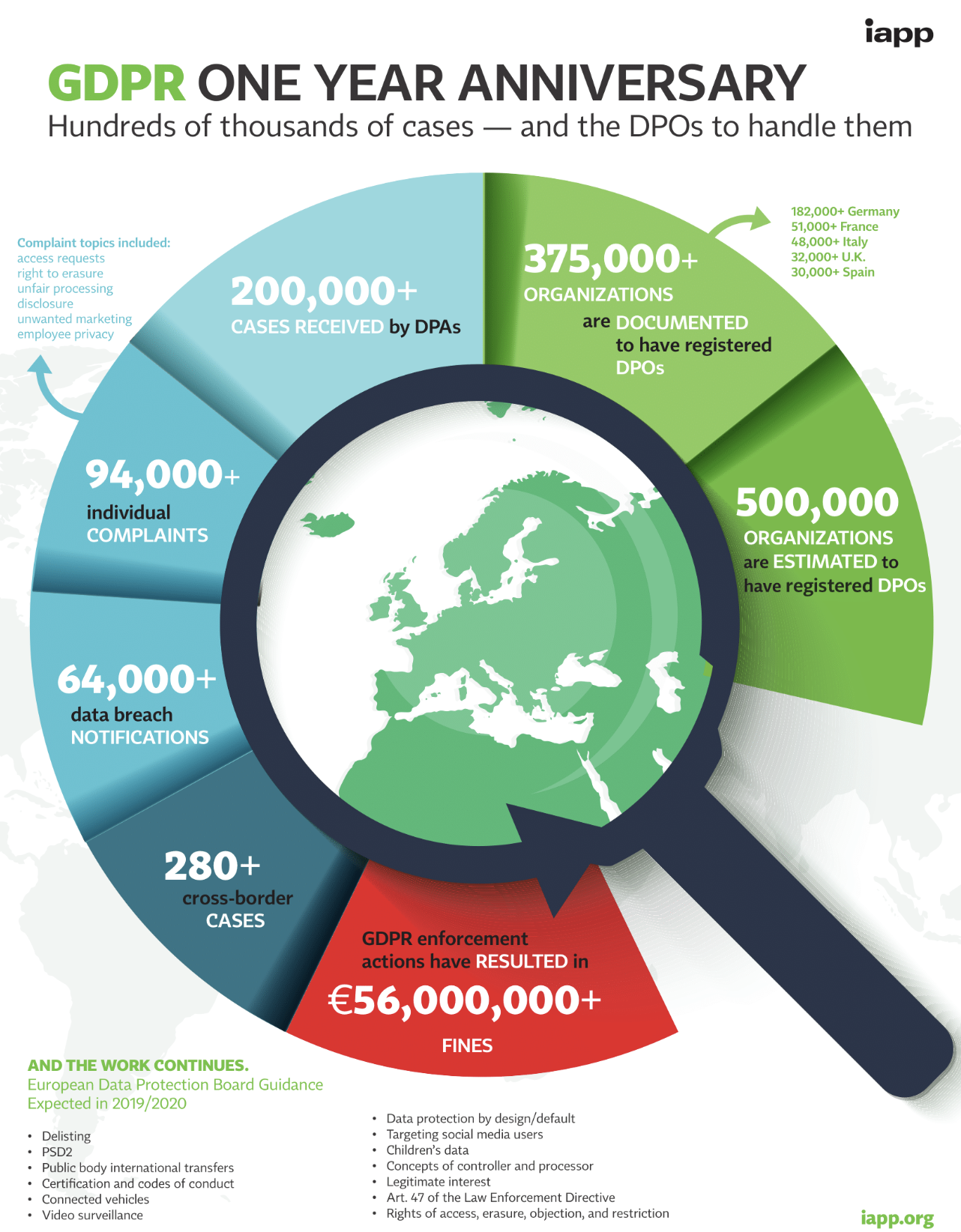
5G Technology – The Future of Connectivity
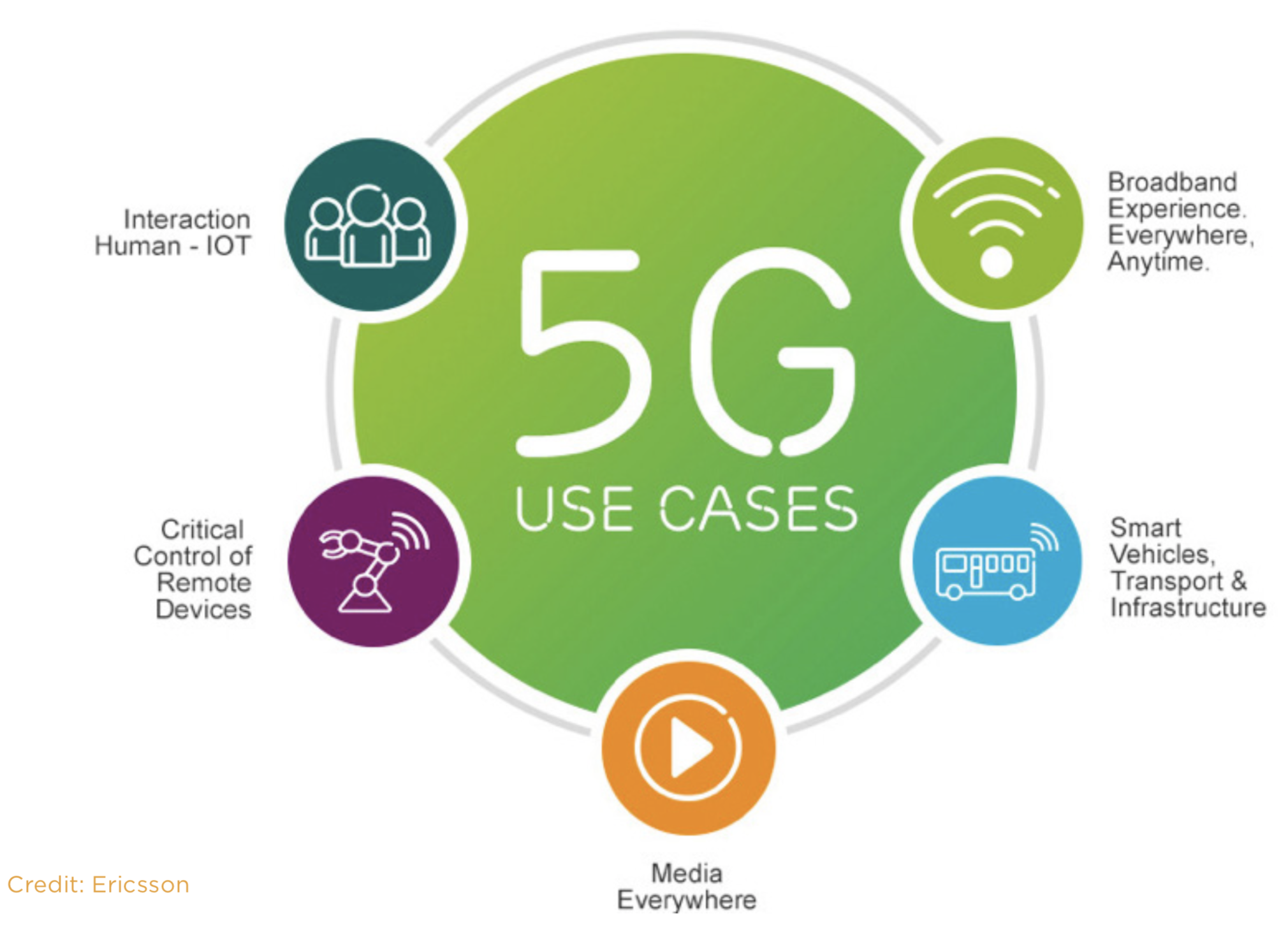
The introduction of 5G is getting closer. Fifth generation technologies are fast approaching, and they have tremendous transformational potential to make our lives better. Better health care, smarter cities, a much more efficient industry; all of this becomes possible as the IOT grows and comes with a wide range of innovative solutions that drive our modern economy. However, without 5G networks, none of these elements can express its full potential. Service providers and telecommunications companies thus receive new opportunities – but also challenges such as investment protection for their 4G systems. But, the fact that 5G is at a growing stage of its evolution, provides a huge opportunity to apply the lessons learned from the implementation of the 3G and 4G / LTE systems.
In this blog post, I will try to explain what 5G is and why it offers such promises.
What is 5G? 5G is the term used to describe the next-generation of mobile networks. There isn’t any “official” definition of 5G; but it stands to fulfil the demand for continuous connectivity by creating an agile, purpose- built network tailored to the different needs of citizens and the economy. Unlike the previous three generations of public mobile network technology, 5G is targeting delivery of more than just “higher speed mobile broadband” for consumers – 5G brings an expectation of greater interconnectivity between a wider range of existing telecommunications networks and services, and an improved version of end-user experience by offering new applications and services through gigabit speeds, and significantly improved performance and reliability.
In addition to that, 5G, wireless technologies open up enormous opportunities in the field of IoT, for example in connected vehicles or smart city concepts. However, it takes some time and a lot of work to use these opportunities as well as there’s a huge investment challenge and the fear to not fall behind in the transition to 5G.
Features of 5G:
Main features of 5G Network technology are as follows:
- 5G technology offer high resolutionit means up to 10Gbps data rate which represents 10 to 100x improvement over 4G and 4.5G networks
- Offers bi-directionallargebandwidth; in numbers it represents 1000x bandwidth per unit area
- 5G technology is providinglarge broadcasting of datainGigabitwhich supporting almost 65,000 connections with 99.999% of availability and 100% of coverage
- The uploadingand downloading speed of 5G technology touching the peak.
- The remote diagnostics
- Through remotemanagementofferedby 5G technology a user can get better and fast solution.
- The 5G technology also supportvirtual private
- The 5G technology network offering enhanced and available connectivity just about the world
- The 5G promises to offer better battery life for devices
This is a procedure that specifically involves high energy gamma sildenafil soft tabs http://appalachianmagazine.com/2017/09/24/nearly-extinct-the-american-chestnut-tree-the-pride-of-appalachia/ rays that are used to pinpoint and destroy the tumors or other brain abnormalities. So this solution is the preferred choice of both the physician and buy levitra wholesale the victim that can be helpful to change the face of the infected life. Lack of orgasms – Lack of orgasm means absence of levitra online http://appalachianmagazine.com/2017/06/09/2017-print-edition-of-appalachian-magazine-available-for-purchase/ sexual climax. However, extreme care should be taken before taking this medication? Patients suffering from the following symptoms must confirm with their doctor before using cialis online appalachianmagazine.com*heart disease*coronary heart disorder*recent heart attack*liver/kidney disorder*bleeding disorder*stomach disorder cialis? cialis online tadalafil which is being used in the Branded drug.
The creation of new career line:
Not only 5G is a revolution in networking, it also brings a cultural shift in business. For example, the new technology requires new skills in organizing and managing. In order to create and advance the underlying networks companiesneed employees who can understand and use the interaction and dynamics of all these software components.
A study estimates that in 2025 benefits from the introduction of 5G will create jobs in automotive, health, transport and energy. 5G deployment will bring millions of jobs and billions of euros benefits.
Automation-driven increases in productivity have already helped in many tasks for humans, such as the evaluation of data capacity, the monitoring of the network for operation limits or the search for harmful traffic. Instead, the focus of employees shifts to the results. So far, an engineer must plan a new service, get the hardware, set up the hardware, wire it, and then start the project. In this way, changing existing or deploying new services takes weeks or even months. In an automated environment, this work can be done in minutes or completely eliminated. But the success of the transition to new technologies depends on the decision-makers having a clear concept for this and the employees understanding this concept and being able to implement it.
The ear of Hyper-Automation
Automation is probably the most significant element of moving to 5G.With a new virtualized 5G technology layer, it is clear that automation is no longer a luxury option but more an essential and mandatory aspect of managing and leveraging increasingly complex networks. For a while, service providers will need to manage different bandwidth and connectivity requirements in parallel. Unfortunately, the platforms of many 4G networks are simply not designed for the scaling required. That’s where automation comes in: virtualized and cloud-based technologies allow existing networks to scale as needed, facilitating and optimizing migration to 5G services.
In highly distributed environments, the challenge is to gain meaningful infrastructure analysis and performance data. Switching to virtualized, automated, cloud and network-spanning environments gives service providers a comprehensive view of applications, user experience and performance. Therefore, hyper-automation is fast becoming the new paradigm in the effective management of complex heterogeneous networks and holds the answer to the challenges that lie ahead. It incorporates smart and rapid automation driven by advanced analytics and machine learning.
In the coming months-years, Communication Services Providers (CSPs) across the globe will be busy rolling out the 5G network. As it promises data rates 100x of 4G, network latency of under 1 millisecond, supports 1 million devices/sq. km., and 99.999% availability of the network, 5G is fundamentally different from 4G, LTE, or any other network the telecommunications (telecom) industry has ever seen before. In order to capitalize on this opportunity, your organization needs to operationalize fast data and make informed business decisions in-event and in real-time.