Data Management: How to Implement the Best Backup Strategy
In today’s fast-paced world, having a robust data management system in place is no longer optional – it’s absolutely essential. With the exponential growth of data and increasing cybersecurity threats, organizations must prioritize the implementation of effective backup strategies to protect their valuable information.
From customer records and financial transactions to marketing campaigns and employee files, every piece of data holds immense value. Without proper organization and protection, this asset can quickly turn into a liability. That’s where data management comes into play. In this blog post, we’ll explore how organizations can implement the best backup strategy to safeguard their invaluable information from any potential disaster.
Best Practices for Data Backup and Storage
Implementing an effective backup strategy is crucial for safeguarding valuable data. Whether you are a small business owner or an individual, having a reliable backup plan can save you from potential disaster. Therefore, when it comes to data backup and storage, implementing best practices is crucial for ensuring the safety and accessibility of your valuable information. Here are some key guidelines to follow:
- Start by identifying the types of data that need to be backed up regularly and prioritize them based on their importance and sensitivity. Schedule regular backups of your data to ensure that you have the most up-to-date version in case of any unforeseen events or disasters.
- Choose the appropriate backup method. There are several options available such as cloud-based backups, external hard drives, or network-attached storage (NAS) devices. Consider factors like cost, ease of use, and security when making your decision.
- It’s important to keep multiple copies of your backups, ideally stored in different locations. This provides an extra layer of protection against physical damage or theft. In addition to having multiple copies, consider storing at least one copy offsite. Cloud-based solutions can be a convenient option for secure remote storage.
- Protect sensitive data by encrypting it before backing it up or storing it in the cloud. This helps safeguard against unauthorized access even if the storage medium is compromised.
- Perform periodic tests on your backup system to ensure its reliability and effectiveness. Verify that you can successfully restore data from the backup files when needed.
- Implement a version control system that allows you to track changes made to files over time, making it easier to revert back to previous versions if necessary.
- Maintain thorough documentation outlining your backup procedures, including schedules, locations, and encryption methods used.
By following these best practices for data backup and storage, you can minimize risks associated with potential data loss or corruption while ensuring easy access when needed most.
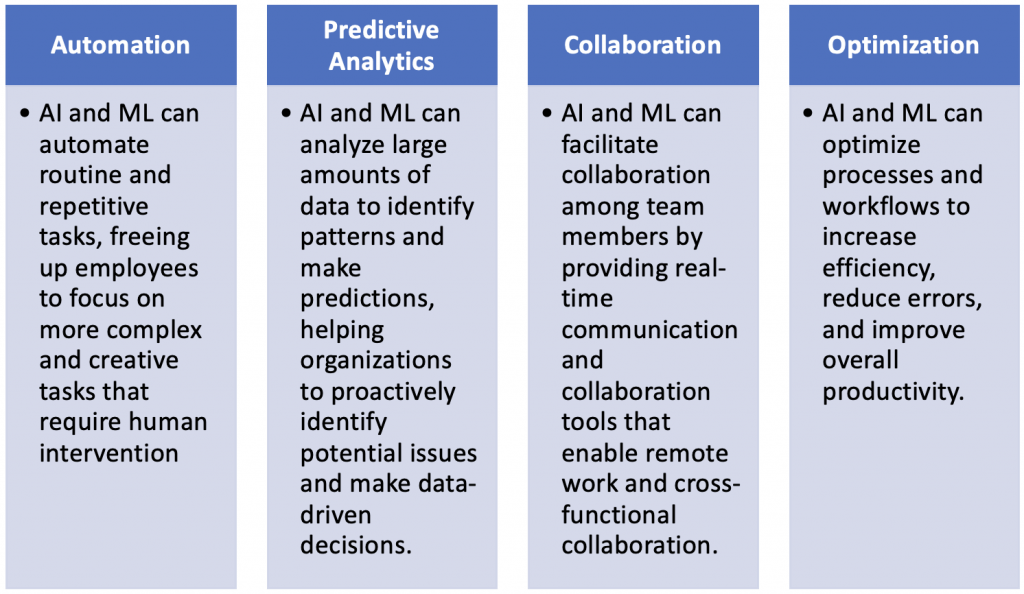
Data management encompasses various processes that involve acquiring, organizing, storing, and utilizing data efficiently. There are several types of data that organizations need to manage. This includes structured data (such as customer information), unstructured data (like social media posts or emails), and semi-structured data (such as log files). Each type requires specific approaches for storage and backup to ensure its integrity and accessibility when needed. By effectively managing their data, businesses can improve decision-making processes, enhance operational efficiency, and gain a competitive edge in the market.
However, implementing an efficient backup strategy is not without its challenges. Organizations often face issues such as limited resources, complex IT infrastructures, compliance requirements, and evolving technology landscapes. Overcoming these challenges necessitates careful planning and consideration of factors like budget allocation for backup solutions, and regular monitoring of backups’ effectiveness through testing procedures such as disaster recovery drills or simulated cyberattacks.
With proven experience in various fields, Xorlogics can help and assist you in safeguarding your valuable assets. So don’t hesitate to fill out this form to discuss your project with our experts!