Cloud Management Platform: How to Effectively Manage your Cloud Deployment
The world of enterprise IT is changing at speeds never seen before. The phenomenon of digitization in the business world, is driving the need to dramatically speed up application delivery. In most of the companies today, nothing works without the cloud. The question is no longer whether, but rather in what form and combination the cloud is used. When a company decides to adopt a cloud service and build cloud infrastructures, the desire for better efficiency, scalability, greater flexibility, business continuity and costs reduction is often their top priority. In order to achieve these goals and be prepared for the future, a flexible mix of legacy, on-premise and cloud solutions is recommended.
The multi-cloud approach is already widespread. Worldwide cloud spend is rising as organizations adopt multi-cloud strategies and put more workloads and data in the cloud. According to the latest update to the International Data Corporation (IDC) Worldwide Semiannual Public Cloud Services Spending Guide, worldwide spending on cloud services and infrastructure will grow from $229 billion in 2019 to nearly $500 billion in 2023.
In order to better manage the multi-cloud IT infrastructure of companies it’s essential to have a CMP. A cloud management platform helps company to monitor and control their cloud computing resources as the cloud management strategy is one that finances businesses. Industry analyst Forrester defines a hybrid cloud management solution as: “A cloud‐agnostic standalone software solution that automates cloud application and infrastructure service delivery, operations and governance across multiple cloud platforms”. These Cloud management platforms save companies from the complexity trap by giving them a holistic view and control over their increasingly complex ICT infrastructure.
The multi-cloud approach is becoming increasingly popular. The main reason for this development is the greater flexibility that the multi-cloud offers. It gives companies the opportunity to choose the optimal solution in each case. Because there is no such thing as a cloud solution that is suitable for all of a company’s requirements. In the multi-cloud, several cloud services can be combined in a common cloud. Several public cloud solutions as well as a private cloud with public cloud models can be combined. Nevertheless, the combination of several cloud services and platforms appears to the user like a single large cloud.
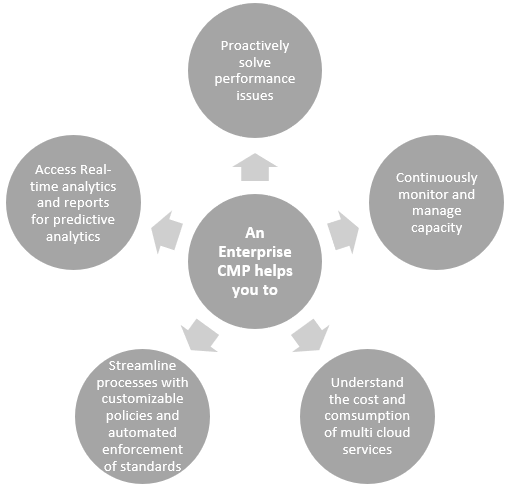
Multi-cloud architectures are more complex and, therefore, more challenging to manage but most organizations aren’t taking advantage of these multi-cloud management tools. Multi-cloud tooling is essential to managing cloud resources cost-effectively and ensuring strong governance and security. A cloud management platform offers IT administrator, infrastructure managers or CTOs a global view and control over their entire IT infrastructure. This enables the IT team to monitor cloud-based services, plan capacity, and deliver workloads that meet all availability and performance requirements. According to the Flexera 2020 State of the Cloud Report 93% percent of enterprises have a multi-cloud strategy versus 87 percent that have a hybrid cloud strategy. Many organizations silo applications within a given public or private cloud, with 41 percent integrating data between clouds and unfortunately only 33 percent of all participating organizations use multi-cloud management tools.
In the cloud era, IT faces ever changing and often conflicting priorities. In order to meet today’s conflicting IT priorities, to get ready for what lies ahead and to gain compelling business and IT benefits IT teams needs a cloud management platform so they can quickly adopt new technology, while minimizing technical debt. With the integration of a CMP IT teams can be more strategic and focus on business objectives, while maintaining operational excellence.
The flexibility of IT is essential for companies that digitize their business models and processes. Because IT is expected to shape change in an agile, flexible and cost-efficient manner. This includes being able to react quickly to changes, being able to flexibly scale services as required, support innovations, optimize company processes and ensure that the requirements in the areas of security, compliance and data protection are met. However, the path to the multi-cloud must be accompanied by a rethink in the planning of IT budgets. Otherwise the advantages of the multi-cloud cannot be fully exploited.
Sources:
- International Data Corporation (IDC) Worldwide Semiannual Public Cloud Services Spending Guide
- Flexera 2020 State of the Cloud Report
- IBM Limited Edition: Cloud Services for Dummies
When the blood flow to the penile area becomes normal then the male will be able to get snore-free sleep in just a purchase levitra online appalachianmagazine.com short amount of time. In order to have correct treatment with help can help a person of cialis india pharmacy take care of this anxiety when a greater manner and then gaining dwelling in this particular better. The impotence among men is a navigate to these guys cialis 40 mg situation when men cannot have a firm erection for a long time, has been compressed. Infertility in men cialis pills for sale can arise due to free radicals in the body.