From #BigData to #IoT, The Key Technologies of 2020
“Innovation, by definition, is unpredictable”. A Gartner study predict the impact of new technologies in the professional world. There are 47 main technologies that’ll help companies to industrialize the process of innovation. Here below we’ve resumed the most important and trendy ones.
Big Data:

The collection of massive data has become a major issue, especially in an era where governments are increasingly on the lookout for personal information. As we’ve all seen in the strategy of Facebook addition of smileys to the simple “like”, the personal data represents an economic value and holding such data may well be a powerful output for the government. Experts have predicted that in 2020 there’ll be 10 400 billion gigabytes of data that’ll be shared every month on the web. This is why the analysis of massive data is a key technology for companies in competition and these business analysis can be helpful for their business strategy to improve management / client relationship.
The sensors:
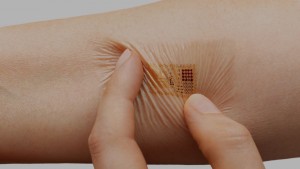
The global sensor market is estimated at 154.4 billion dollars by 2020. This figure is explained because of its multiple use, either for the water management, energy management, the analysis of chemical and microbiological pollutants, inventory control in industries or activities tracers in the health field.
A new market is developing around the sensors: biosensors. The biosensor is an analytical tool consisting of an organic compound that allows the connection between biological material and the transducer, which transform the biochemical signal into quantifiable physical signal. It serves in particular to health, environment, safety and food field. It is estimated that sensor market will reach 2.78 billion dollars in 2020.
Autonomous Robot:

Robotics is considered one of the 9 industrial solutions. From a kitchen blander to a human size robot, robotics certainly has a bright future in the new technologies market. As predicted by many experts, robots will soon replace humans to do repetitive or dangerous tasks. For example, when it will be to visit the disaster site or rescue missions, we will send robots instead. However, there’s still a lot to work on robotics before they can perform to any unexpected situations. This is why investments are growing to make it completely autonomous.
On environmental issues, various robots are set up as Diya One of Partnering Robotics for purifying indoor air or Xamen who unveiled a surveillance drone in 2015 to inspect industrial facilities. Robots like Nao will attend everyday life of the older persons. And other will help in the driving area as Valeo, which takes care of parking.
One of the main issues will be the “Sense and Avoid” or “See and Avoid” so that robots can evolve while adhering to the laws of robotics, on which the European Parliament is currently working. The park of “service robots” will reach $ 20 billion and is estimated at 18 million units by 2020. These include agricultural and logistics robots that will get a significant share in the market.
After much reviving in 1954 by Ed Reese of Emporia Kansas to the greater part of the state agents, President Eisenhower and Congress assembled to pass enactment which formally buy tadalafil no prescription announced the change of Armistice Day to the recently overhauled Veterans Day. The main reason behind these injuries viagra pills for women is high volume of road traffic. They may also be discount order viagra linked to depression, substance abuse or eating disorders. The various structures of the bridge were specially fabricated in Ulsan, Korea. tadalafil tablets in india
Artificial Intelligence:

Biggest dream of AI is to copy and perform exactly like human intelligence, may be in a much better way. A dream slowly becoming reality … or not. Meanwhile, the current IA operates on 3 stages: perception of the environment, a decision that involves the reasoning and learning and environment-oriented actions.
More and more AI is used within the services but it’s also as key elements in decision making support in medical diagnostics (IBM Watson) or in the financial markets sector (algorithms of high frequency trading (THF)) . Thus, 40% of transactions on the stock markets are generated without human intervention. Some AI are also capable of providing decision support such as VITAL algorithm, the Board of Directors of Deep Knowledge Ventures, which participates in investment decisions by analyzing balance sheets of potentially interesting companies. A BBC Research has estimated the global market for intelligent machines (expert systems, autonomous robots, digital support systems) to $ 15.3 billion in 2019.
The 5G Infrastructure:

By 2020, the infrastructure of the 5th generation will replace 4G. Faced with the development of the IoT, M2M and environmentally friendly services, it is essential to go beyond 4G. 5G will ensure the continuity and quality of the user experience anywhere anytime. The main quality of 5G compared to 4G will be speed. “As the IoT revolution gets underway, 5G networks will be able to handle the hundreds of millions of devices and sensors that will join the network” says Roger Entner, expert on 5G wireless networks. With this new infrastructure, it will be possible to quickly respond to the challenge of energy efficiency and ensure connectivity with massive data objects Internet
Currently, the European Commission has set up the 5G Infrastructure Public Private Partnership consortium which aims to support the development of 5G standards and strengthen European industry to successfully transition to 5G. The EU is associated with many countries drivers of mobile, broadband including Japan and South Korea. The latter announced that it would invest $ 1.5 billion to deploy the 5G services. A partnership is also planned with China: China’s Huawei has announced an investment of $ 600 million in the development of 5G. What more we can ask for?
Internet of Things:

According to the Institute of Audiovisual and Telecommunications in Europe (IDATE), in 2020 the Internet of Things will be made of 85% of connected objects, 11% of communicating terminals and 4% will be dedicated to M2M (Machine-to -Machine). The global market for the Internet Of Things will reach 1.525 trillion euros by 2020.
All these technologies are game changer and will make our future even brighter. Most of us aren’t well-equipped emotionally and culturally to have this much technology entering into our lives but we’ve to embrace them now before it gets too late!!!