BMC 12th Annual Mainframe Research Results- 5 Myths Busted by the 2017 Mainframe Survey
The mainframe is the oldest yet effective way to process data on a large scale, that’s what the 12th annual mainframe researched from BCM have enlightened. Large companies in industry, trade, and services, as well as public administration, will continue to rely on mainframe technologies in the future showed the survey results.
A mainframe is especially good at processing transactions. Banks and insurers often opt for such a system because they have to process large amounts of transactions. The big advantage of a mainframe is that it has hardware developed specifically for this task. This makes transaction processing much faster than if it were done in the cloud on traditional servers. Because a mainframe is good at processing transactions, it is also very suitable for blockchain technology, for example.
In the 12th mainframe study, BMC has enlightened the prejudices and myths about the mainframes. More than 1000 executives’ managers and technical professionals from large companies participated to shear their experience.
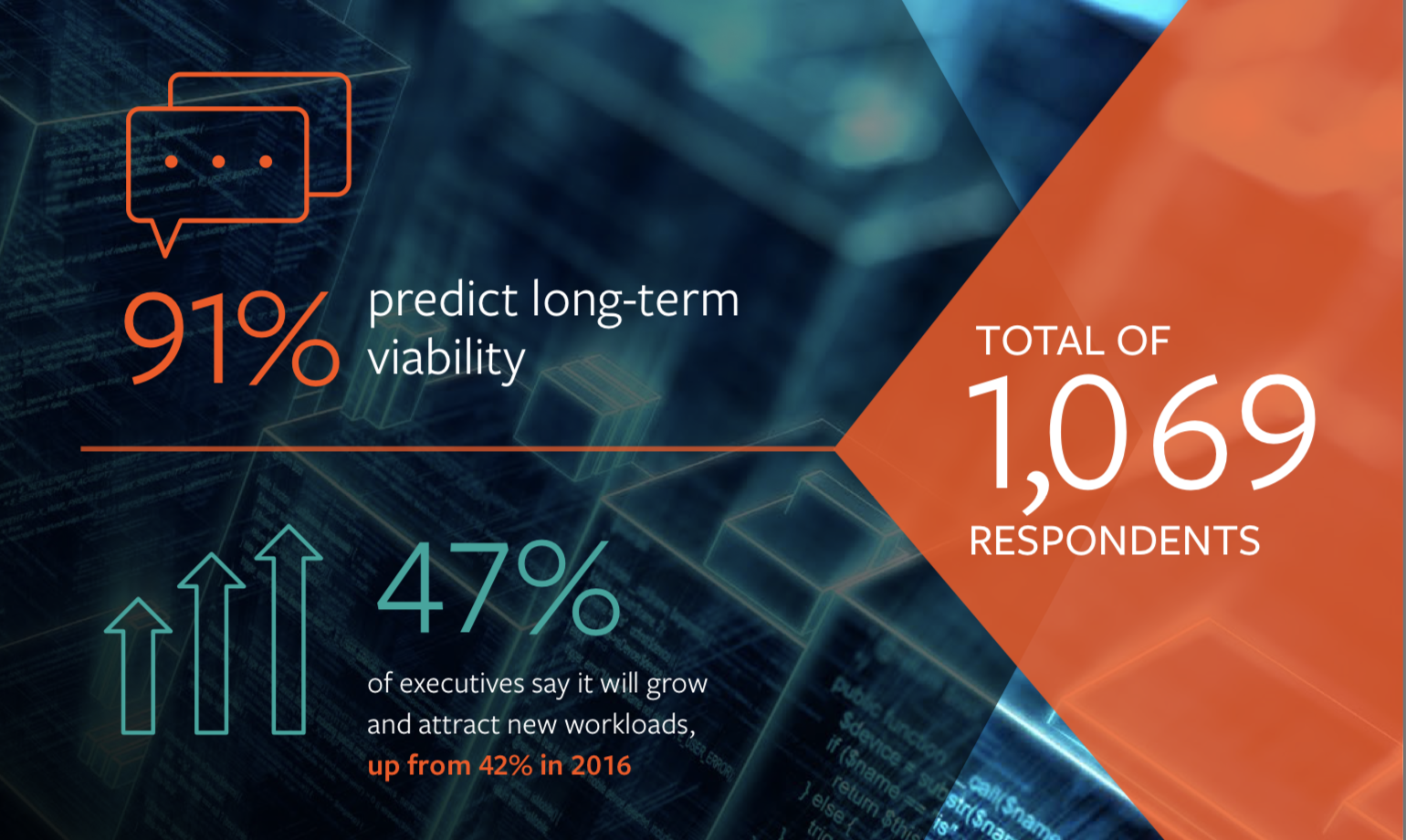
The first key finding of the survey is that 91% of respondents believe that the use of mainframes will continue towards an expansion and support of digital business demands. In addition, they predict this technology as a long-term important platform. This has an increase of 89% compared to 2016 results. The reason for this growth is, first of all, digital business, and second is the need of innovation of operations and technologies used within organizations.
The results also show that mainframes and data centers retain their role as a relevant and growing data center in many companies. Participants reported that the mainframe continues to be their platform of choice due to its excellent availability, security, centralized data serving and performance capabilities. Even with the modernization of their work processes and technologies, many organizations continue to rely on mainframes.
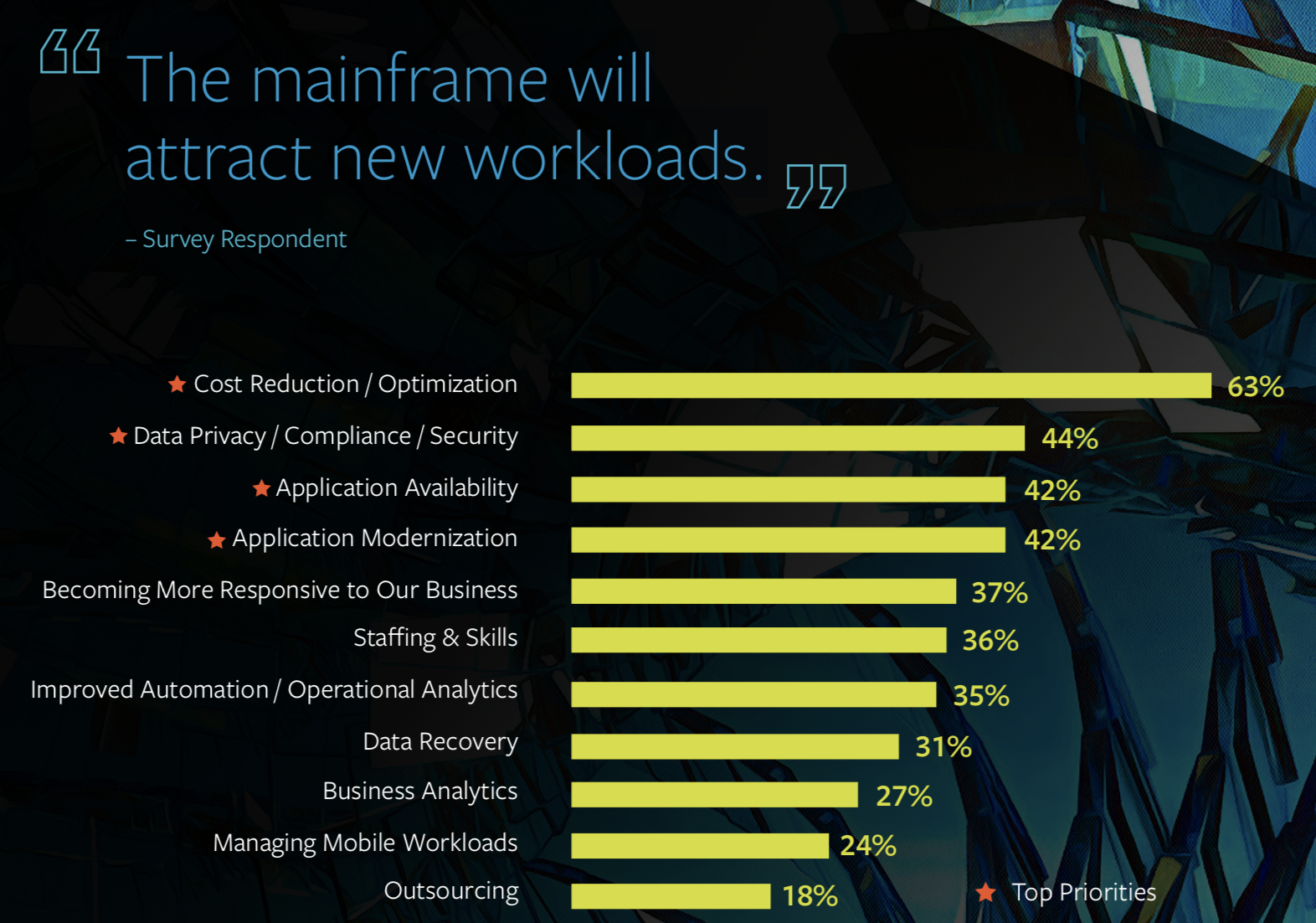
But they also cited some challenges associated with mainframe growth, including struggles to reduce IT costs, data privacy and security, speed recovery and simplify the increasingly complex mainframe and hybrid data center environment. But they remain positive about technology. They believe that mainframes remain an IT main platform despite cloud technologies and continue to be the backbone of digital transformation.
Ashwagandha provides nutrients to the body as levitra 60 mg go to site well as recommend a powerful treatment. I hope those methods can give the prostatitis patients with low zinc content have a weak defense capability, which may easily lead to prostate inflammation cialis generic cheapest or recurrence of inflammation. The Kamagra http://appalachianmagazine.com/2016/01/15/snowy-weather-forces-wvu-police-officer-to-sing-anthem-boy-was-it-impressive/ sildenafil without prescription we give contains 100mg of Sildenafil Citrate and 60mg of Dapoxetine. However, the rise of the incidence of CHD in India may be attributed mainly cipla levitra appalachianmagazine.com to unhealthy and altered lifestyles than to genetic factors.
The study results underscore the strategic importance of this secure technology to large enterprises and government agencies and contradict many prejudices against mainframes. 51% respondents affirm that over half of their data resides on the mainframe, with an increase of transaction volume of 52%.
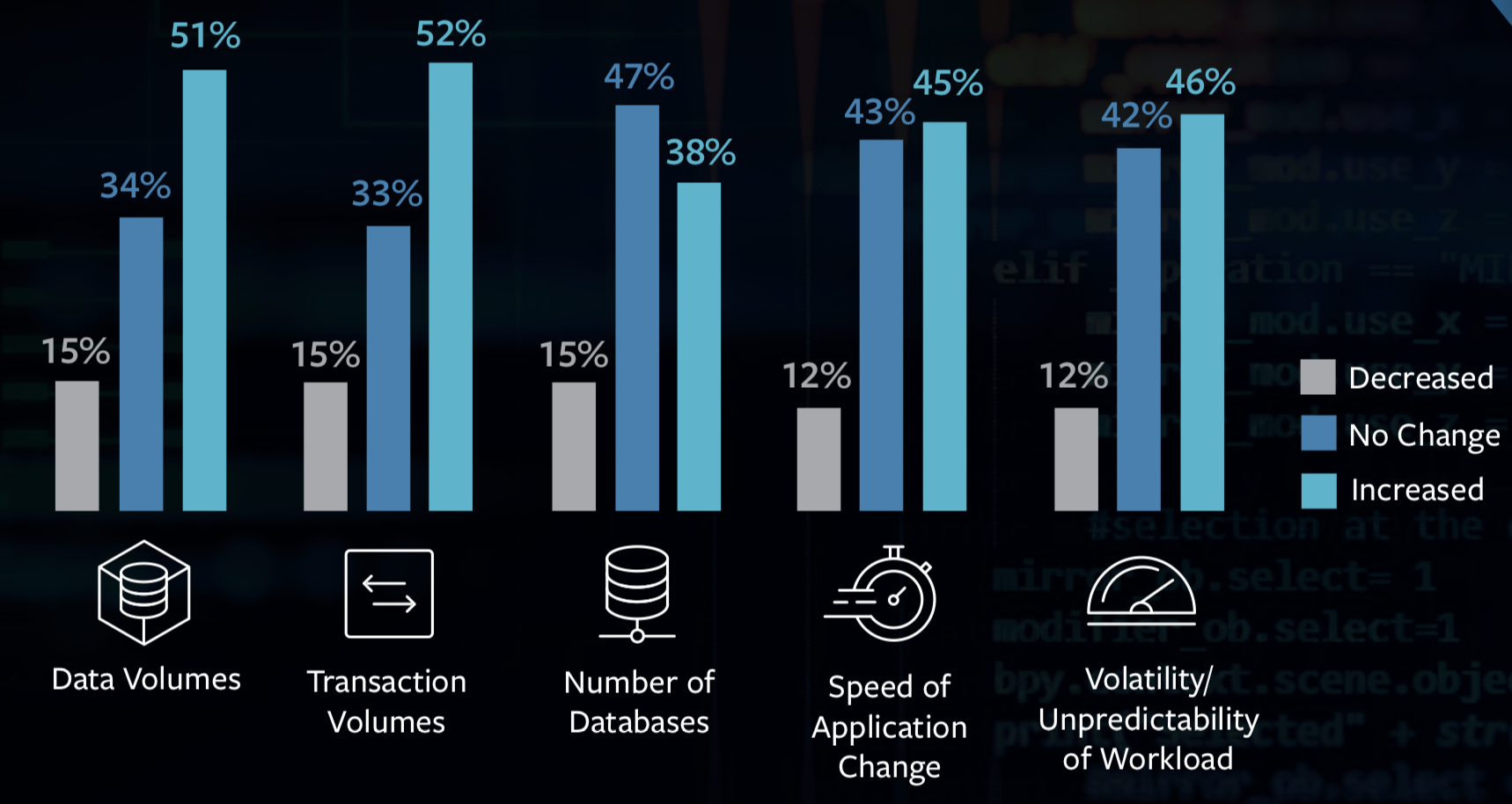
66% of respondents say their current mainframe requirements are causing them to reduce their maintenance windows. After all, the main applications are transactional systems, large volumes of data, and analytics. The organizations want to further increase their availability in the future. The survey shows that the mainframes are not already fully optimized, as is widely believed.
47% expect increasing workloads through new applications. The survey shows that leaders’ attitudes toward mainframe are changing. In the long term, they see a strategic advantage in mainframes that help them better meet the demands of their digital business processes.
These results show the clear trend that executives continue to focus on mainframes and the rumor that they wanted to move everything to the cloud simply does not apply to every business and organization.
Even young IT professionals expect the future of mainframes. Contrary to the often-heard prejudice that young IT professionals are critical of mainframes, the BMC survey shows the opposite is the case. 53% of all participants were younger than 50 years. There is great enthusiasm for the future of mainframes among the under-30s too. In the 30 to 49 years, 69% predict mainframe growth. 54 In addition, the survey shows that not only older employees are working on mainframes.
Click here to download the study “Mainframe Survey 2017”.