IT security trends in 2024
As much as we would like it, the number of cyber attacks will not be going down any time soon, on the contrary, companies must prepare for the fact that it can affect them anytime! As change is constant in the technology market, the cybersecurity landscape is also dynamic and subject to rapid changes. Therefore, it’s required for companies to undertake and review their security action as a top priority along with focusing on their ability to check and secure their blind spots and strengthen their IT security. Below is the list of some general areas that have been important in recent years, and are continuing to be relevant in 2024:

Zero Trust Security Model: The Zero Trust approach, which assumes no trust within or outside the network, is likely to gain more prominence as organizations strive to enhance their security posture. At its core, Zero Trust is founded on the principle of never trusting and always verifying. Unlike traditional security models that rely on perimeter defenses, Zero Trust assumes that threats can originate from both external and internal sources. Every user, device, and application is treated as potentially untrusted, requiring continuous authentication and authorization. Zero Trust addresses the shortcomings of perimeter-based security, offering a more resilient and adaptive approach to protect sensitive data and systems. Several major companies have successfully implemented Zero Trust, showcasing its effectiveness in diverse industries.
Artificial Intelligence and Machine Learning in Security: AI and ML are being used to enhance threat detection and response capabilities. As attacks become more sophisticated, these technologies can help in identifying patterns and anomalies. and help improve the efficiency and effectiveness of cybersecurity efforts by automating tasks, detecting threats in real time, and providing proactive defense mechanisms against a wide range of security challenges.
IoT Security: Securing these devices requires a holistic approach that addresses both technical and operational aspects. As the number of connected devices continues to grow, ensuring robust IoT security measures is essential to protect users’ privacy and prevent potential disruptions caused by security breaches.
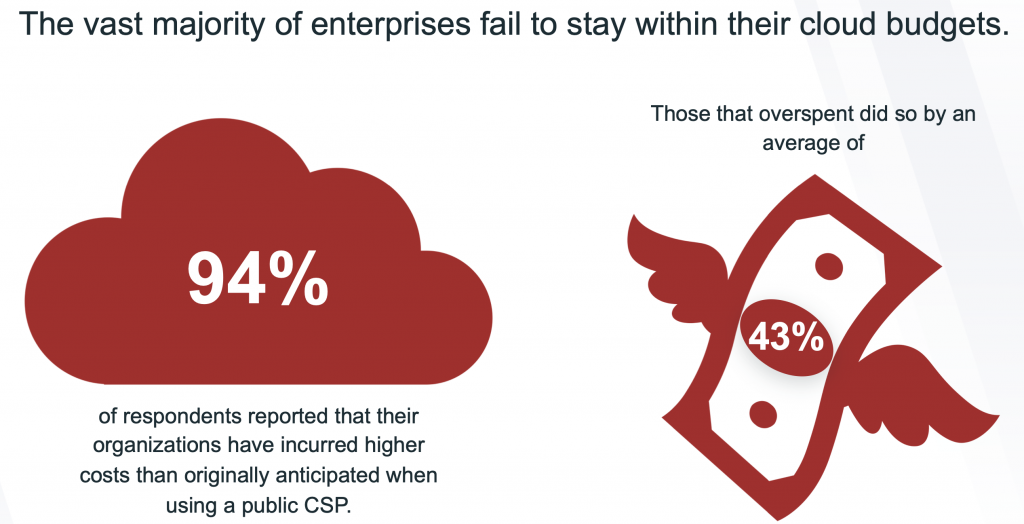
Ransomware Protection: Ransomware attacks have been a significant threat, and organizations will likely continue to invest in advanced measures to protect against and recover from ransomware incidents.
Identity and Access Management (IAM): Strengthening IAM controls will remain a focus area to ensure that only authorized individuals have access to sensitive data and systems.
Endpoint Security: As remote work becomes more common, securing endpoints (devices like laptops, smartphones, etc.) will be crucial to prevent security breaches.
Regulatory Compliance: As data protection regulations evolve, organizations will need to stay compliant with existing and new regulations, which may influence security strategies.
Remember that the field of cybersecurity is rapidly evolving,and new trends and technologies may emerge. Staying informed, adopting a proactive security posture, and continuously improving security measures are key components of an effective ransomware protection strategy.