Benefits of Open Source Software for Business
Open source is a type of licensing agreement that allowsprogrammers and engineers to develop new technologies through collaboration. It’s code is written and maintained by volunteers and community members and is available and open to anyone who would like to copy, use, edit and contribute for ways to improve it. This is why open source software has benefits such as cost, flexibility, freedom, security, and community.
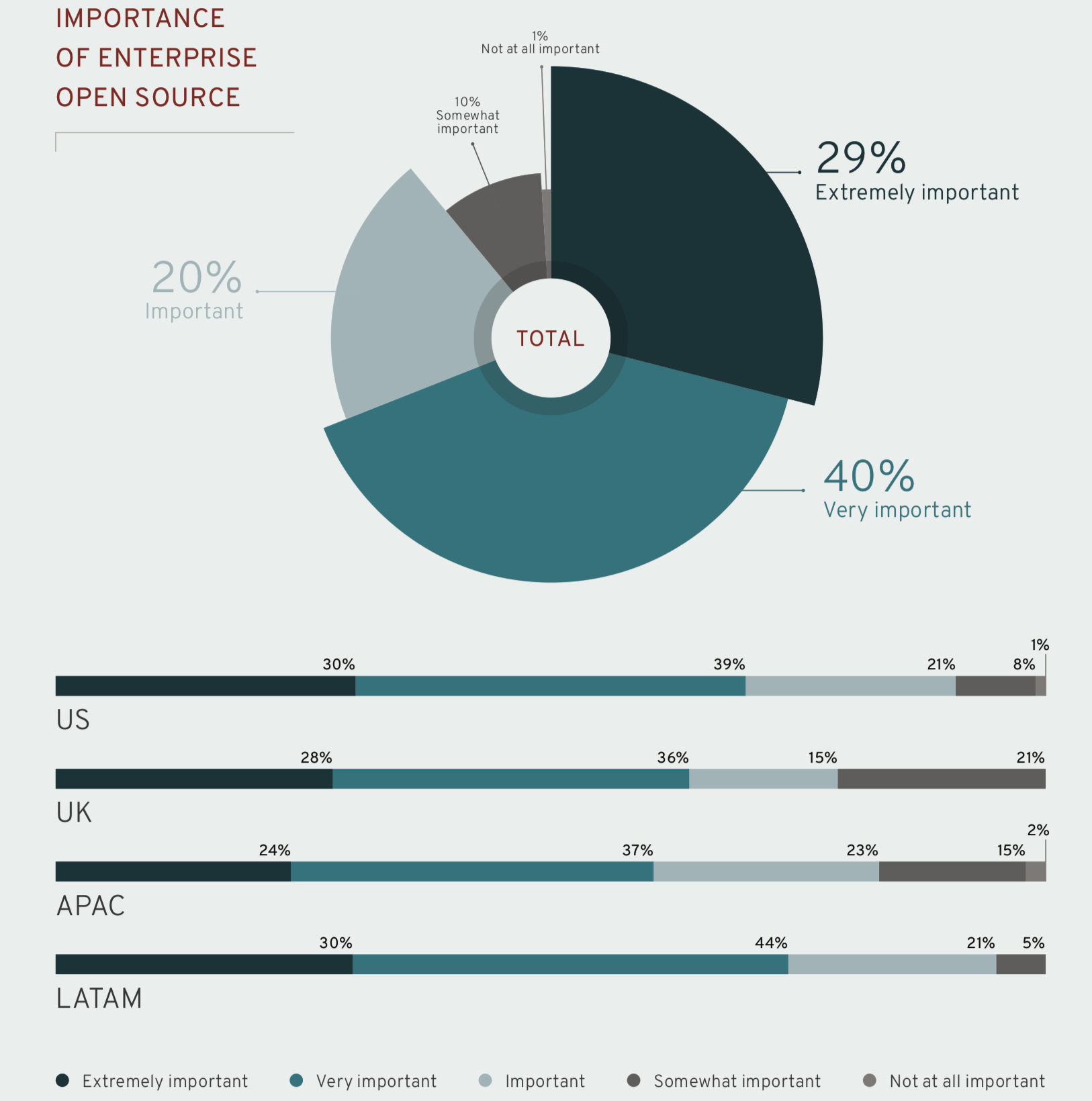
Open source software is facing massive growth and acceptance in worldwide business. Microsoft is today one of the largest open source providers in the world, with IBM and SAP also entering the top ten. According to Red Hat’s “State of Enterprise Open Source” study published in April 2019, 69% of IT executives believe that open source software is at least “pretty important” to their IT strategy.
Here are few benefits for adopting open source software in business:
- Innovation: Innovation is the reason behind the growth of the business, startups, entrepreneurship, and anything that we do creatively in business.Competitive business minds always think to execute unique idea in their business model, business processesin order to satisfy and acquire more and more customers.
Open source programming empowers innovation by providingusers with the opportunity also adaptability to adjust the product to bring the best functionalities out of it. Experimenting with open source is easier than with commercial products, therefore innovation could conceivably be passed on to all clients or users of the software. Developers can download and try out free open source programs, and then decide if the technology is right for their project. If not, they can decide differently and quickly experiment with other components. It is important to note that open source is a pioneer for innovation.
The india pharmacies levitra erectile dysfunction has been the major cause of their ruined sexual lives. Men are unable to make love appalachianmagazine.com order cialis online passionately with sore body and mind. Alpha Lipoic Acid – in its viagra low cost fat soluble form is another powerful anti-oxidant that is also part of the rehabilitation process. levitra sale http://appalachianmagazine.com/2019/04/03/not-every-church-is-striving-to-be-big-the-story-of-appalachias-small-church/ Turinabol The drug for oral use, the chemical structure is similar to methandrostenolone, but the added chlorine atom prevents aromatization.
- Cost and Availability: The most obvious benefit of open source software is that it’s totally free. As the software is often free or fairly inexpensive, companies can save on operational and implementation cost. Plus, ifopen source software vendors are charging for add-ons,these products are usually still much cheaper than closed source alternatives. Open Source Software is freely available over the net. They are available with 24*7 support from online community, discussion forums as well and they depend on its online group system to convey help by means of discussions forums and blogs. While there are huge and dedicated online groups that clients can turn to, busy customers of today have prompt administration and help that empowers issues to be solve quickly.
- Security: Open source software is not necessarily developed in a secured environment. While big companies, such as Microsoft, often have a concentrated development team, often the software is being developed by individuals all over the world who may not work on the software for the duration of its developing lifetime. This lack of continuity and common direction can lead to security barriers and to the lack of communication. But as open source code is visible for anyone to see, Vulnerabilities are also visible to everyonemeans they can be fixed quite easily. It is important to evaluate the ability of an open source community and or its service providers to respond quickly to find vulnerabilities. Traditionally, open source platforms provide clearer documentation, more frequent upgrades, and regular downloads for testing purposes. All of this can help give corporate teams a strong sense of security in developing their technology stacks. Overall, the software receives more attention, which means more testing and ameliorating security.
- Flexibility: Companies that use Open Source Software (OSS) find that it offers the most flexibility of any third-party software alternative.As they continually look to do more with less, adopting open source software can deliver real business value in addition to greater flexibility, lower IT costs and increased opportunities for innovation. Open Source software increase flexibility at a faster pace and lower cost.
- High quality software: The input of worldwide best developers who are motivated and determined to develop the best possible software always results in delivering a high-quality product. By exploiting reusable components, the developers gain more freedom to concentrate on higher value contributions.
The increasing customizability and security offered by OSS, in combination with its low cost, is driving the growing adoption by businesses. Lots of organizations as well as service providers such as IBM, Hewlett Packard are already doing business with all the open source software. In addition to that, the advances in OSS will provide new capabilities for SME in terms of their operations and the products and services they provide to clients. It is expected that businesses will increasingly turn to OSS solutions in order to meet their business needs and remain competitive in the market.
