From On-Premises to Online: The Ultimate Cloud Migration Checklist
Are you ready to take your business to the next level and move from on-premises to online with a cloud migration strategy? As exciting as this may sound, it’s important not to rush into the process without proper planning. Fear not, because we’ve got you covered! In this blog post, we’ll provide you with the ultimate checklist to ensure a smooth and successful transition to the cloud. Whether you’re just beginning or in the final stages of migration, our comprehensive guide will help make sure no stone is left unturned.

What is Cloud Migration and Why Migrate?
Cloud migration is the process of moving data, applications, or other business components from an on-premises environment to a cloud computing platform. There are many reasons why businesses migrate to the cloud, but the most common ones are to improve agility, scale operations more quickly or cost-effectively, or to take advantage of new features or functionality offered by a cloud provider. Cloud providers offer a pay-as-you-go model, which means you only pay for the resources you use. This can be a big advantage over traditional on-premises infrastructure, which often requires a large upfront investment.
Migrating to the cloud can also help improve your security posture. When you store data and applications off-site, in a secure data-center, you can protect them from physical disasters such as fires or floods. And because cloud providers have expertise in security, they often have stronger security controls than most businesses could implement on their own.
There are several different types of cloud migrations that businesses can undertake. The most common are lift-and-shift migrations, in which an organization moves its existing on-premises infrastructure and applications to the cloud without making any changes; rehosting migrations, in which an organization moves its applications to the cloud but keeps its existing infrastructure; and re-platforming migrations, in which an organization moves its applications to the cloud and makes changes to how they’re built or how they run.
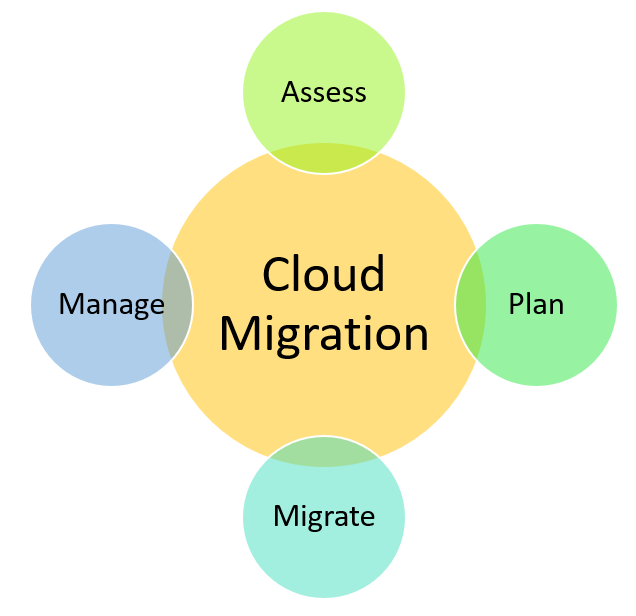
Steps for a Successful Cloud Migration
- Define your goals and objectives for the cloud migration. What are you looking to achieve by moving to the cloud?
- Determine which workloads and applications you will move to the cloud. Not all workloads are suitable for the cloud, so it’s important to carefully consider which ones will make the most sense to migrate.
- Assess your current infrastructure and application dependencies. What components of your on-premises infrastructure will need to be migrated or replaced in order to run in the cloud.
- Evaluate your options for migrating to the cloud. There are a number of different ways to approach a cloud migration, so it’s important to choose the right one for your specific needs.
- Plan and execute your migration strategy. Once you’ve determined how you’re going to migrate, it’s time to put that plan into action and get started with the actual process of moving your data and applications to the cloud.
Pre-Migration Tasks
Pre-migration tasks are critical to ensuring a smooth transition from on-premises to online. Here are some key things to do before beginning your cloud migration:
- Assess your current infrastructure and identify which components can be migrated to the cloud.
- Develop a cloud adoption strategy that outlines your goals, budget, and timeline for migrating to the cloud.
- Evaluate different cloud providers and choose the one that best meets your needs.
- Create a comprehensive backup of your on-premises data and systems.
- Test your applications and systems to ensure they are compatible with the new cloud environment.
Post Migration Tasks
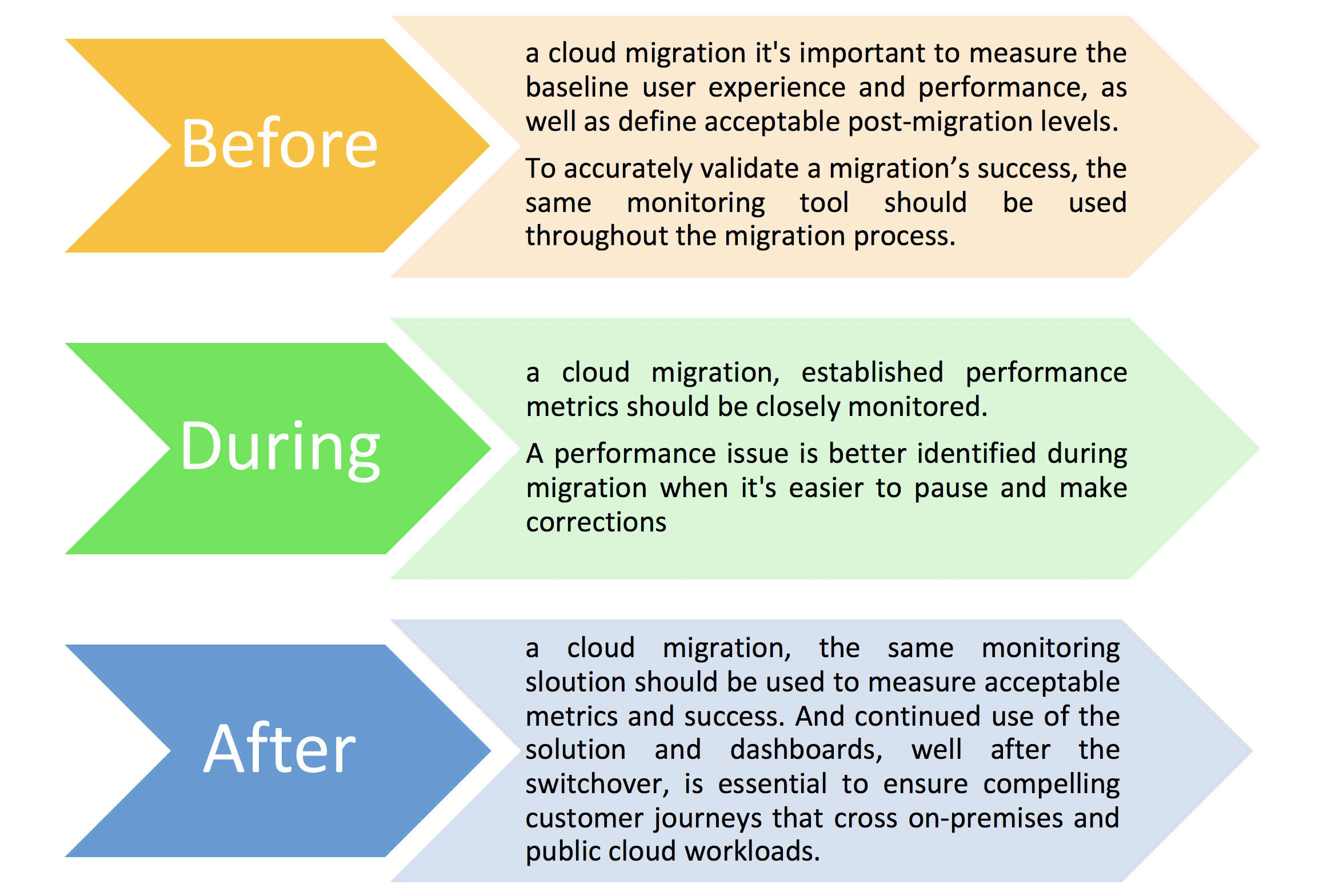
After you’ve successfully migrated your data and applications to the cloud, there are a few post-migration tasks that you should perform to ensure everything is up and running smoothly. Here’s a checklist of what you should do:
- Verify that all data and applications have been successfully migrated.
- Perform a comprehensive performance test of all migrated systems to ensure they are functioning as expected in the new environment.
- Update your documentation to reflect the new architecture and configuration.
- Modify any monitoring or management tools you use to reflect the new environment.
- Adjust your backup and disaster recovery plan as needed for the new environment.
- Notify all relevant parties (e.g., employees, customers, partners) of the successful migration and provide them with instructions on how to access the new system
- Continuously monitor your usage and adjust your resources to optimize your costs. Cloud providers offer tools and services to help you monitor and manage your costs.
- Security should always be a top priority. Implement security best practices and monitor your environment for potential vulnerabilities.
- Cloud technology provides new opportunities for innovation. Explore new cloud services and features to improve your business processes and create new value for your customers.
- Develop a disaster recovery plan to ensure your data and applications are protected in the event of a disaster or outage. Test your plan regularly to ensure it is effective.
Conclusion
Cloud migration is a crucial step for any business that wants to stay competitive in the digital world. With this ultimate cloud migration checklist, you have the necessary steps and considerations to ensure a successful transition from on-premises to online systems. Make sure you thoroughly plan out your strategy before executing it, as even small mistakes can cause major disruptions during key times. By taking the time to understand what needs to be done and checking off each step of this list, your business will benefit from a seamless transformation into the cloud.