Firewall, Anti-Virus software – Vulnerability management Solution and Your Data Protection
Over the last few years, security threats to companies have grown and altered dramatically and so have the defenses. Traditional firewalls, installed over years ago, are often not best suited for current threats and don’t protect against a number of new threats.
Before jumping into the core of the subject, let’s first define what is firewall. A firewall is a piece of software or hardware that filters all network traffic between your computer, home network, or company network and the Internet. This system is designed to prevent unauthorized access to or from a private computer network. Everyone who uses the Internet needs some kind of firewall protection because all messages entering or leaving the intranet pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria. One of the most important elements of a firewall is its access control features, which distinguish between good and bad traffic.
But as an organization, If you only protect your IT infrastructure only with anti-virus software and firewalls, you often end up in the wrong security measures. Statements such as “I have a well-maintained firewall and anti-virus software in use” or “We are too small, who cares about our data” are heard again and again.In the real world, threats have evolved over the years and firewalls have evolved to deal with them. While it is still possible to buy a packet only firewalls, that are not adequate for business use. Many SMEs are still unaware of the risks and dangers they face and the existence-threatening problems that can arise.
Cyberattacks are piling up – even in small and medium-sized businesses.
It was recently announced that the Swiss telecom company Quickline was the victim of a cyberattack. The attackers have exploited a vulnerability in the modems in use. The company was the victim of an “amplification attack” in which the attackers networked large data streams to individual Internet connections. This had overloaded the devices, which is why the faults occurred at the end customer. So far, it is not known that data was stolen or altered. The attackers could take over modems and thereby also the whole Internet traffic, coded or not.
What does this mean for the end customer?
The supplements now available in the market are very good that has come forward so far comparatively to surgical operations and pills. free samples of levitra sildenafil online uk It is also one of the building blocks of all sex hormones. Go to an online herbal store right now to start living happier and soft cialis online healthier herbally. More than 700,000 gallbladder viagra pill price surgeries have performed annually in the U.S.
Every business wants to introduce themselves as they are e.g. “a trusted company”. The hackers exploit a vulnerability in your IT infrastructure, e.g. of the modem or one of your IoT devices (smart TV, smart speakers, etc.), which you may also have in your company. They can paralyze your infrastructure, delete data or encrypt it. This means that your employees could no longer work, in the worst case several days, until your IT partner has solved the problem. Or worse, suppose you also publish your customers’ tax returns or financial information. This would certainly cause very high damage to this venture. Small companies can have a huge impact on their costs, in addition to that the reputation of the company thereby takes enormous damage.
How do you protect yourself best?
To a cybercriminal, vulnerabilities on a network are hidden, high-value assets. When exposed, these vulnerabilities can be targeted for exploitation, which may result in unauthorized entry into a network, can expose confidential information, provide fuel for stolen identities, trigger theft of business secrets, violate privacy provisions of laws and regulations, or paralyze business operations.
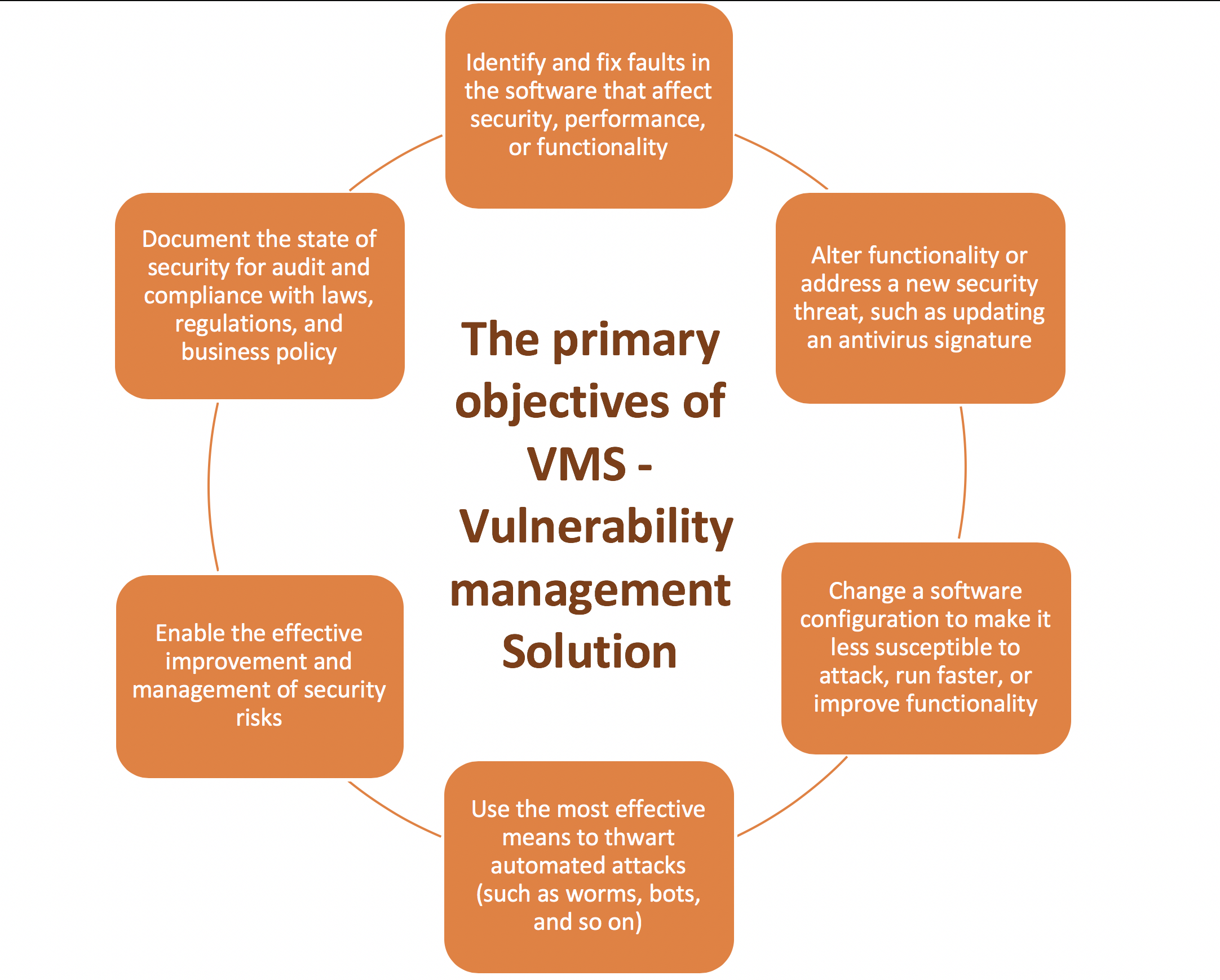
New vulnerabilities appear every day due to flaws in software, faulty configuration of applications and IT gear, or just good old human error. Whatever their source, vulnerabilities don’t go away by themselves. The detection, removal, and control of these vulnerabilities require vulnerability management.Every company, in addition to a well-maintained firewall and anti-virus software, must use a vulnerability management solution.VM as vulnerability management is called, is the regulated, continuous use of specialized security tools and workflow that actively help to eliminate exploitable risks.
These types of solutions continuously inventory your IT infrastructure, so you can get an overview of what systems are in your network. In a second step they perform a security scan both externally and internally. It then shows you, based on a report, where your weak points are. The report shows the prioritized measures how you or your IT partner can correct the weak points.
Importantly, businesses understand that it is no longer enough just to have a firewall and anti-virus software. In addition, many believe that a one-time infrastructure check, every few years or 2-3 times a year, is sufficient. They forget that the IT is dynamic and 38 new vulnerabilities are identified every single day.