Top Tech trends for 2023: What can companies expect in 2023 and position themselves better?
The year 2022 was marked by supply chain disruptions, inflation, debt, labor market gaps, geopolitical uncertainties, fears of recession and increasing ransomware attacks. These developments continue to pose a critical threat to the companies. But it is also important to look into the future at the end of the year to be better prepared for the challenges and opportunities to come & heal covid19 scars.
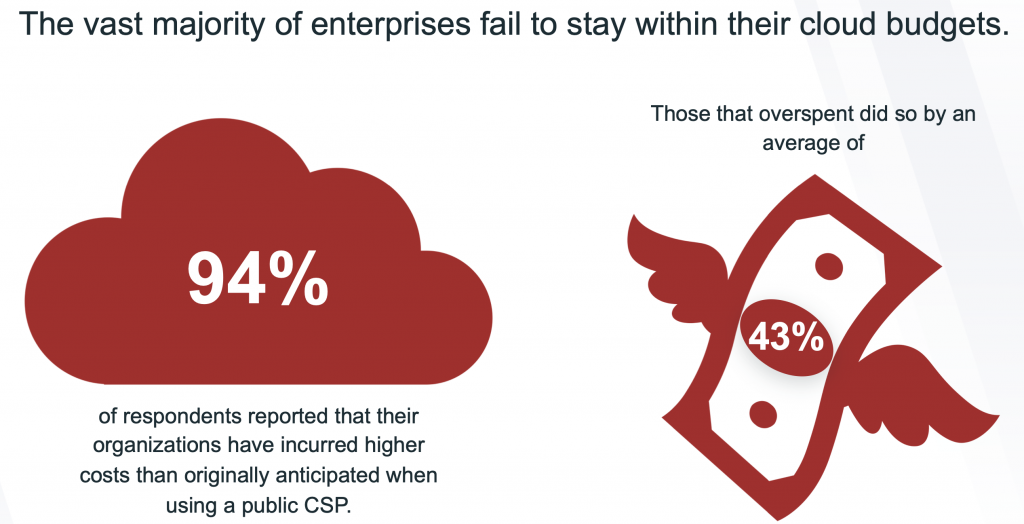
Cloud budgets are being analysed more closely
According to a recent report by Veritas, misunderstanding about cloud security, scalability and storage has led most enterprises spending much more than anticipated. 93% of companies overspend on the cloud, exceeding budgets by an average of 43%. As the amount of data increases every year, the cost of storing it in the cloud also increases. For IT teams, this is becoming increasingly difficult to justify. Exceeding budget is mainly due to the misunderstanding nearly all organizations had that CSPs are responsible for protecting their assets in the clous. Although cloud adoption has enabled most companies to implement advanced business strategies, future CEOs and boards of directors will demand more transparency into the return on investment (ROI) of cloud spending. IT managers are under great pressure to justify their cloud budgets while finding new solutions to reduce data volume as Veritas expect IT spending to be reviewed even more closely in 2023.
Low-code and no-code make compliance difficult
As the demand for hyper-automation and IT modernization is growing at an exponential rate, low-code and no-code applications are contributing significantly to the democratization of application development in companies. In 2023 they will become even more established. The global low-code platform market is forecasted to generate a revenue of $187.0 billion by 2030, increasing from $10.3 billion in 2019, and is expected to reach 31.1% CAGR in the forecast period (2020-2030).
Employees without a technical background (citizen developers) can develop their own applications. Almost 60% of the custom apps are now built outside the IT department. Of those, 30% are built by employees with limited or no technical skills, creating huge compliance issues for businesses. Because citizen developers are less experienced in implementing security and privacy systems. Creating new vulnerabilities that can be exploited by cyber criminals.
Edge device vulnerability
Gartner analysts predict that by 2025, around 70% of of the data managed by organizations will be created and processed outside of the data center or cloud vs 10% now. Adoption of edge devices are considered as the solutions that facilitate data processing & generation. But this increasing shift of data processing to the edge complicates the IT architecture and increases the attack surface. Because of the lack of IT specialists, it is often not possible to provide the same level of protection at the network edge as in the data center or the cloud. Nevertheless, to fully protect the enterprise, every single edge device must be secured.
IOT & hyper-connectivity
We live in a hyperconnected world where worldwide companies are under huge pressure of shearing and integrating data in a smart way. It’s predicted that there will be more than 43 billion connected devices by 2023 with the goal of generating, collecting, shearing and helping companies to make use to data in the smartest way possible. 5G technologies are also boosting the full potential of IoT & hyper-connectivity. It’s true that IoT devices make our lives easier and more convenient but also comes with huge security issues if not well protected.
As the number of devices explodes during 2023 and beyond, device manufacturers and security experts will have to strengthen their strategies to fight against cyberattacks and minimize the chances of losing valuable data.