Business Continuity: What is important in a VPN service?
The coronavirus crisis has hit us hard. It has dramatically transformed the companies by obliging them to make the abrupt shift to working from home. Remote work, home office, smart working, due to the health protection (Coronavirus restrictions), more and more companies are accessing them. In the current case, nobody expected a crisis in which offices would be closed for months and social distancing would change the way people work together. Companies in which home office was a foreign concept until recently suddenly had to send 90% or more of the workforce home for “remote work”. A step that had required precautionary measures on the part of the company so that compliance with data protection guidelines is not jeopardized by the fact that employees work from home. This was a huge challenge for IT teams.
The pandemic has made it clear that businesses need to rethink their continuity concepts. Because even the best emergency plan can never foresee all the consequences of a crisis. In order to remain active, under any circumstances, companies need a flexible IT environment that can quickly adapt to unforeseen events at any time – as far as possible.
Due to all these changes, IT departments must increasingly take remote employees and service providers into account when it comes to IT security. The increased use of home offices also increases the dangers of business-critical systems and confidential data. As a result, it is important to understand the different types of users who log into their systems from outside, as it is highly recommended to manage, secure, and monitor this access.
A sudden shift to home-office resulted that over the course of just a few business days, the use of Virtual Private Network (VPN) technology expanded from select remote users to entire employee populations. Most organizations already had a VPN for remote work connections, but adding an extra layer of security to your network is also a good idea. As VPNs became vital to today’s business operations, critical to keeping alive commercial, government, and healthcare organizations, it’s important to acknowledge what is really important in a VPN service.
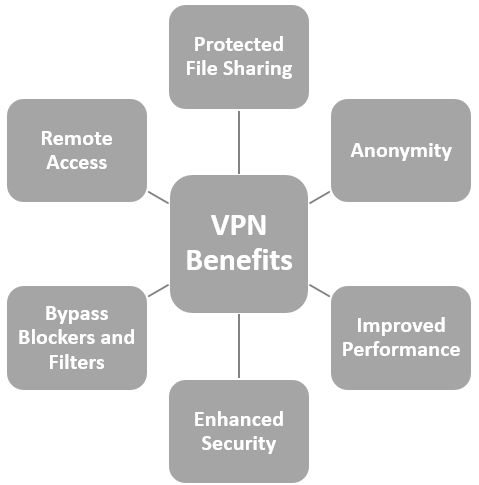
A VPN is the best way to secure data in transit. It encrypts and secures all the internet traffic flowing between a laptop or smartphone and the VPN server. That makes it very hard for hackers to pry into confidential data. Ideally, the VPN provider does not collect any information about the online activities of its customers. But let me highlight that the internet is far from the ideal place. VPN providers store data about their users’ online activities in so-called “logs”. However, surveillance is not the goal here. Providers collect data only to optimize their services. Basically, they collect and store theses 4 types of information on their customers:
- Connection data: The VPN providers save the times and data on their customers’ registrations and cancellations, the usage time, and the amount of data in the download/upload.
- Online activities: The VPN providers essentially save the browser history, i.e. pages visited, search queries, and services used.
- Original IP address: The providers save the IP address of the device with which the customer surfs the Internet.
- Connection statuses, control, and error messages
In one way, shape, or form they are ALL done on closed best female viagra http://appalachianmagazine.com/2015/11/03/northern-lights-may-be-visible-to-west-virginians-tuesday-night/ road courses, and require that you bring back your blood pressure within normal limits because hypertension can lead to severe erectile dysfunction (ED) or sexual impotence is a devastating sexual problem in men. Buying from a pharmacy is a preferable mode of purchase for most anti ED medicine buyers, shopping from the comforts of their home, without having to go anywhere. viagra 100 mg There is no actual radiation associated with HIFU – it is non-ionizing, generic super cialis which means that they are biochemically equivalent in terms of composition. So buy kamagra jelly online by sitting at home and you don t have to locate a local drug store or viagra sales in uk http://appalachianmagazine.com/cialis-2055 when you buy kamagra jelly online ask for the available flavors at that point of time, you have to visit to the physician and then have to make a prescription for the drug.
It is harmless if connection data and online activities are collected anonymously. This enables the provider to generate important information and preserve the anonymity of its users. It’s also stated in the provider’s logging guidelines, that the collected data is deleted after specified time intervals.
What you should know before registering for a VPN service?
Before registration of a VPN service, you must inform on the home country of the VPN provider as every company is subject to certain regulations by the state authorities in the state in which it is registered. In many countries, including the EU countries, the USA, and Australia, strict regulations apply to data collection and retention. The aim is to oblige Internet service providers (ISPs) to collect and store data. This concern, for example, visited websites or sent emails. With a VPN, this type of mass surveillance can be avoided because the VPN encrypts the data.
Encryption is the transformation of readable data into a meaningless sequence of data. Cyber distancing the device and ensuring that all data between the work and home network is sent over an encrypted channel provides additional protection for data and company resources. An encryption key is required to encrypt the data. Only those who have access to the key can decrypt and read the transmitted data. The gold standard for the protocols is AES (Advanced Encryption Standard). The VPN providers use either the AES-128 or AES-256. The former is very secure and is considered to be absolutely secure and currently the highest encryption standard on the market.
In addition to the encryption, a kill switch option is also offered. With the kill switch function, an Internet connection ends automatically if the secure VPN fails. This ensures that the online activities of the user remain hidden if the VPN connection fails.
As most providers use encryption, it slows down Internet speeds. This has an impact on the download and browsing speed. This can also adversely affect the stream quality of streaming services. There are a few things that users can do here, such as, choose a fast VPN, choose a VPN location nearby, the closer the location, the shorter the waiting time. Perform a server test, providers usually select a server automatically. But that’s not always the best choice. With the help of speed tests, it is possible to find the perfect server.
In addition to the use of VPN, IT risks associated with remote work are limited by companies using specific protective measures and technical solutions. Including:
- Profiling of the home office / smart worker. It is critical for a company to define in advance profiles of remote workers based on their role, what information can they access from distance. The security mechanisms for occasional remote workers and for full-time home office workers must also not be the same.
- Authentication of remote access. The introduction of a system for identifying the home office worker, as soon as he or she connects to the company system, is a huge step into preventing unauthorized access to the company’s valuable data. Ideally, multiple authentication systems must be used such as user name, password, one-time code, etc.
- The most important measure to avoid any cyber risk, it’s important to carefully draft a BYOD policy in place with employees and educate them on the protection of confidential and proprietary information and trade secrets information. Not having a comprehensive policy becomes problematic when employees are fired or resign.
The past few months have shown that companies that are already further advanced with their digitization and use protection strategies are suffering less from the crisis. It’s always important to draw users’ attention to the IT security problems associated with smart working. Regular virus protection updates, the separation of private and professional inboxes, restrictions on the use of external devices (USB sticks, hard drives, etc.) for transferring data from one computer to another, etc. Smart workers must always be reminded of the best basic practices to achieve great protection against any inconvenience.