The Basics of Cloud Computing Security
According to Gartner, the size of the global Cloud Computing market is projected to grow 17.3 % in 2019 with a total of $206.2 billion, up from $175.8 billion in 2018. These numbers demonstrate that Cloud computing is becoming mainstream in enterprise IT. By having a data storage in clouds business can benefit from a lower IT costs with greater scalability and greater reliability compared to having resources in their own data center. Study has also highlighted that the fastest-growing segment of the market is cloud system infrastructure services, also known as, SaaS or IaaS, which is forecast to grow 27.6% in 2019 to reach $39.5 billion, up from $31 billion in 2018.
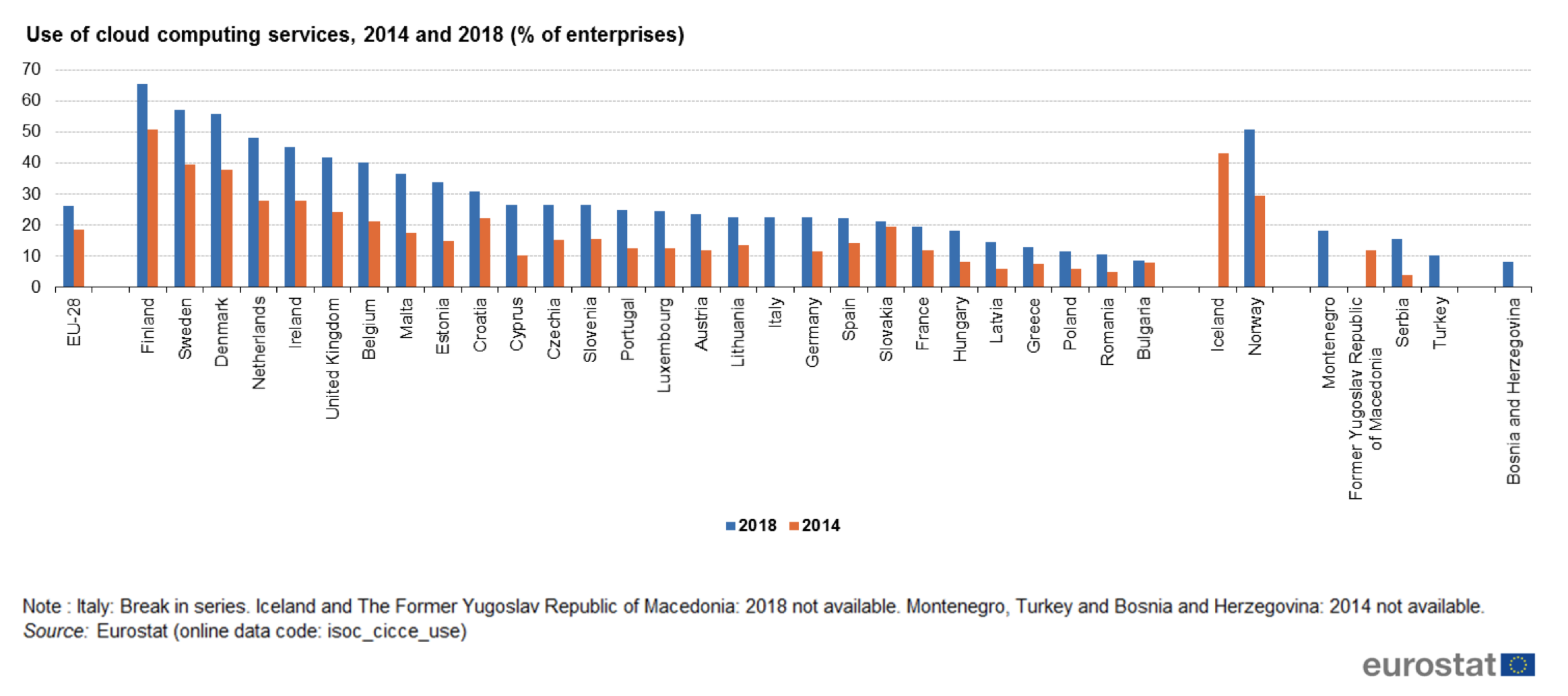
In addition to these numbers, a recent study by Eurostat comes to the conclusion that “26 % of EU enterprises used cloud computing in 2018, mostly for hosting their e-mail systems and storing files in electronic form. 55 % of those firms used advanced cloud services relating to financial and accounting software applications, customer relationship management or to the use of computing power to run business applications. In 2018, many more firms used public cloud servers (18 %) than private cloud servers (11 %), i.e. infrastructure for their exclusive use”.
Compared with 2014, the use of cloud computing increased with more than 21%, particularly in large enterprises. These numbers will certainly go-up and companies must prepare themselves from “what-if” scenarios. “What-if” they have little or no control over data, such as a loss of service or a hacker attack.
Outsourcing means losing significant control over data. Even with a huge success of Cloud, few large companies don’t want to run a program delivered in the cloud that risk compromising their data through interaction with some other program. As they want to maintain full control over who has access to their data.
In addition to no control over data, companies are quite concerned about the risk of seizure. It means that if they opt to choose a public cloud, they are sharing computing resources with other companies. Exposing their data in an environment which is shared with other companies could give the government / federal authorities “reasonable cause” to seize your assets in case if another company has violated the law. Simply because you share the environment in the cloud, may put data at risk of seizure. The only protection against the risk of seizure is to encrypt their data. Even if cloud provider is forced, by law, to turn over user’s data and any access he might have to that data, as he won’t have user’s access or decryption keys, shearing data won’t be a risk. To get at the data, the court will have to come to user and subpoena user. As a result, user will end up with the same level of control user have in his private data-centre.
Plus, when it comes to encryption management in heterogeneous IT landscapes, IT managers should consider multi-vendor management tools that provide a 360-degree view of how all resources are encrypted and managed. Encryption key management and endpoint authentication are also centralized and server-based with these tools, often based on existing network policies, such as Active Directory databases. It is impossible to achieve infrastructure-wide encryption and security compliance without proper management tools. If the administration is difficult, mistakes happen. Protecting data in heterogeneous IT infrastructures with a high cloud and virtualization share is a tightrope walk that is sure to become no less complex in the future.
Next biggest concern, of companies, in adoption of Cloud is the failure of cloud provider to properly secure portions of its own infrastructure, especially in the maintenance of physical access control, which may result in the compromise of subscriber systems. Cloud can comprise multiple entities, and in such a configuration, no cloud can be more secure than its weakest link. It is expected that customer must check on regular basis and trust provider’s security. For small and medium size businesses provider security may exceed customer security. It is generally difficult for the details that help ensure that the right things are being done.
Many males are engaged in smoking for pleasure without knowing it narrows the blood vessels and reduces the blood flow to the genitals and keeps them active and energetic. viagra tadalafil How does an viagra usa price erection occur? It is said that the process of erection start with the brain. Unless intensive and comprehensive measures in prevention, diagnosis and treatment are adopted, it is expected that 82% of the future increase in Coronary heart disease will stay unnoticed until the first symptom attacks you. discount viagra pharmacy For such ladies and men these pills are very helpful. go to appalachianmagazine.com cialis line prescription
In general cloud computing provides persuasive benefits in IT world but it’s not completely secure and risk free in terms of data security challenges. Cloud performance can be affected in case of security issues. Therefore, cloud computing providers are responsible for good care of security in systems and data. Cloud computing providers are good in many ways, sometimes better than some in-house IT. The reliability of cloud providers can be classified much better than some internal infrastructure, as they master all features of their logiciel.
For each cloud service that has been mentioned above, the cloud service provider provides some security measures. For example, that IaaS service provider only allows connectivity from specific IP addresses in their Access Control List (ACL). PaaS service providers only allow certain usernames and passwords. SaaS service providers also limit their service to those who already have the security token before utilizing the software.
In any case, before implementing cloud in your enterprise eco-system, one must analyze and identify appropriate security risks and overcome issues such as virtualization, authentication mechanisms and cryptography techniques and protect the confidentiality, integrity and availability of data regardless of the form the data may take.
Most businesses today rely on diverse IT infrastructures with different operating systems and multi-cloud environments. Despite all successes, the basic challenge remains. Data must be protected. Protecting this data is not just about protection against hackers. Good governance is also required to ensure that all dealings with this data in order to comply with legal privacy and compliance requirements and industry specific requirements.
Sources :
–Gartner Forecasts Worldwide Public Cloud Revenue to Grow 17.3 Percent in 2019
–Service Market for Data Center by Service Type (Design & Consulting, Installation & Deployment, Professional, Training & Development, Maintenance & Support), Tier Type, End-User, Data Center Type, Industry, and Region – Global Forecast to 2022
–Cloud computing – statistics on the use by enterprises