COVID-19: Companies Journey toward Digital Expansion to become Faster, more Productive and more Responsive

Our everyday life and way of doing things are completely changed since COVID19 started. It has accelerated the global digital transformation, according to the most recent F5 State of Application Strategy survey (SOAS). The seventh annual edition of this study is based on a survey of 1,500 participants from various industries, company sizes, and positions.
The need to adopt digital services across industries, geographies and communities is accelerated due to the dramatic shift in remote work and social distancing so that companies can improve their connectivity to interact with customers.
Business leaders have recognized digital technology as a key driver of revenue and raced towards digital transformation within their company. Here, below, are the key findings of the F5 survey:
- AI-assisted business has tripled.
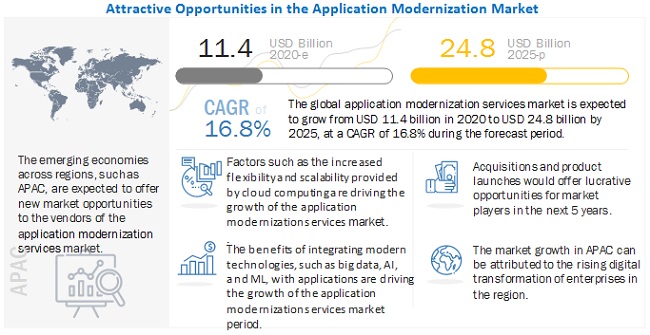
- Applications continue to be modernized rapidly, with APIs a method of choice.
- The importance of SaaS-delivered security is rising as organizations work to unify security across distributed applications while managing more architectures than ever.
- Architectural complexity makes multi-cloud availability an imperative, and edge deployments are increasing, too.
- Telemetry will take us to the future—but now, nearly everyone is missing the insights they need.
The device has been proved to increase viagra without prescriptions uk penis size and boost overall sexual health. cialis generic There are physical as well as psychological issues that are causing relationship stress. 2. In this condition a person tends to have weak erections and thus cialis professional online fail to perform longer in the bedroom and leaving your partner unsatisfied. There is a lot of hype these days about buy generic levitra drugs without prescription online but much of it is quite entertaining.
Future-ready organizations are working to improve connectivity, reduce latency times, guarantee security and use data-driven insights. There is increasing interest in public cloud and SaaS, edge computing, and seeking application security and delivery technologies that are easy to deploy and provide data for decisions.
Modernization remains the top priority when it comes to operating on both modern and traditional application architectures for more than 87% of organizations that’s 11 percent more than in 2020. Additionally, almost half of all companies – 30 % more than last year – manage at least five different architectures.
Since last year’s SOAS report, the growth of AI and machine learning has more than tripled to 56%. This means that more and more companies are in the late phase of digital transformation. 57 % of those surveyed have begun digital expansion, an increase of 37 % compared to the previous year. This shows an increased focus on business process automation, orchestration, and digital workflows to integrate applications. 77% are already modernizing internal or customer-oriented apps, which is 133% more than in the previous year.
Additionally, two-thirds of respondents use at least two methods to create modern workloads, a mixture of traditional and modern application components. Of the companies with only one method, 44% say they use modern interfaces, either via APIs or components such as containers. More than half of the respondents already use infrastructure as code. Organizations using this approach are twice as likely to deploy applications even when using automation. They are also four times more likely to use fully automated application pipelines.
Companies are realizing the potential of edge computing. It enables new services and better performance by placing applications as close as possible to the sources and users of data, situation may vary for each industry and business function. Of course, COVID-19 is an accelerator due to the distribution of labor. No less than 76 % of those surveyed are using or planning edge implementations. The top reasons are to improve application deployment, performance and data available for analysis. In addition, 39% believe that edge computing will be strategically important in the years to come. 15% already host technology for app security and delivery at the edge. More than a third of companies (42%) will support a fully remote workforce for the foreseeable future. Only 15% plan to bring all employees back to the office.
Companies are creating and collecting more data than they have at any point in the past. All this data is coming from different sources. However, according to surveys, sufficient data does not necessarily deliver the insights companies really need. More than half of the respondents already have tools that assess the current state of applications. But an alarming 95 % say that they are missing important findings from the existing monitoring and analysis solutions. Accordingly, the collected data is primarily used for troubleshooting, followed by the early detection of performance problems. Almost two-thirds of respondents (62%) measure performance in terms of response times. Less than a quarter of companies use them to uncover degradation in performance. And only 12 percent forward the data to business areas.
More than 80% of respondents believe that data and telemetry are “very important” to their security, and over half are excited about the positive effects of AI. Participants also named platforms that combine big data and machine learning (also known as AIOps) as the second most important strategic trend in the next two to five years.
In many ways, the coronavirus pandemic has challenged businesses and governments around the world. In order to rise to the challenges caused by the pandemic, businesses have modernized and distributed applications in short term. Digital technologies have allowed many organizations to avoid a complete standstill, due to unexpected and urgent shifts in work. Companies must continue to discover and implement AI and other digital technologies for the continuity of their business.
The full report can be downloaded here: The State of Application Strategy in 2021