Legacy System Migration: Should IT spend its time maintaining Legacy Investments?
Everyone knows that legacy systems are bad. Unlike wine, they don’t get better with age. These systems belong to the legacy of past generations of software. Legacy systems, which form the backbone of many enterprises, are holding organizations back from leveraging new digital technologies and creating new experiences for their customers/partners. Many developers wish that they never have to inherit these. Good luck to those who get stuck with maintaining or converting them.
These legacy software systems can still be found in many companies and administrations. While these systems may still meet the requirements, they were originally designed for, they are typically based on old technologies that are no longer common. Since they only partially meet today’s IT requirements, organizations keep facing poor system performance and paying high maintenance costs.
Legacy system migration refers to the modernization of old IT systems to a newer hardware infrastructure or software platform. In companies, the maintenance effort on IT systems is steadily increasing, thus the old systems must be transferred to a connected and up-to-date version with multi-layered architectures. For the IT team, this means an enormous challenge.
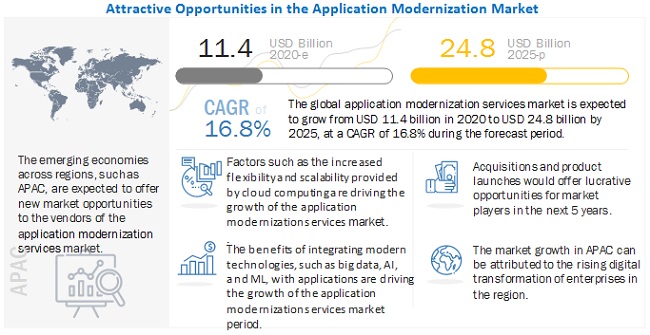
According to a study the global application modernization services market size is expected to grow from USD 11.4 billion in 2020 to USD 24.8 billion by 2025. Key factors of this growth are cloud services, rising demand for modern infrastructure to ensure business continuity and focus on transforming and modernizing legacy systems.
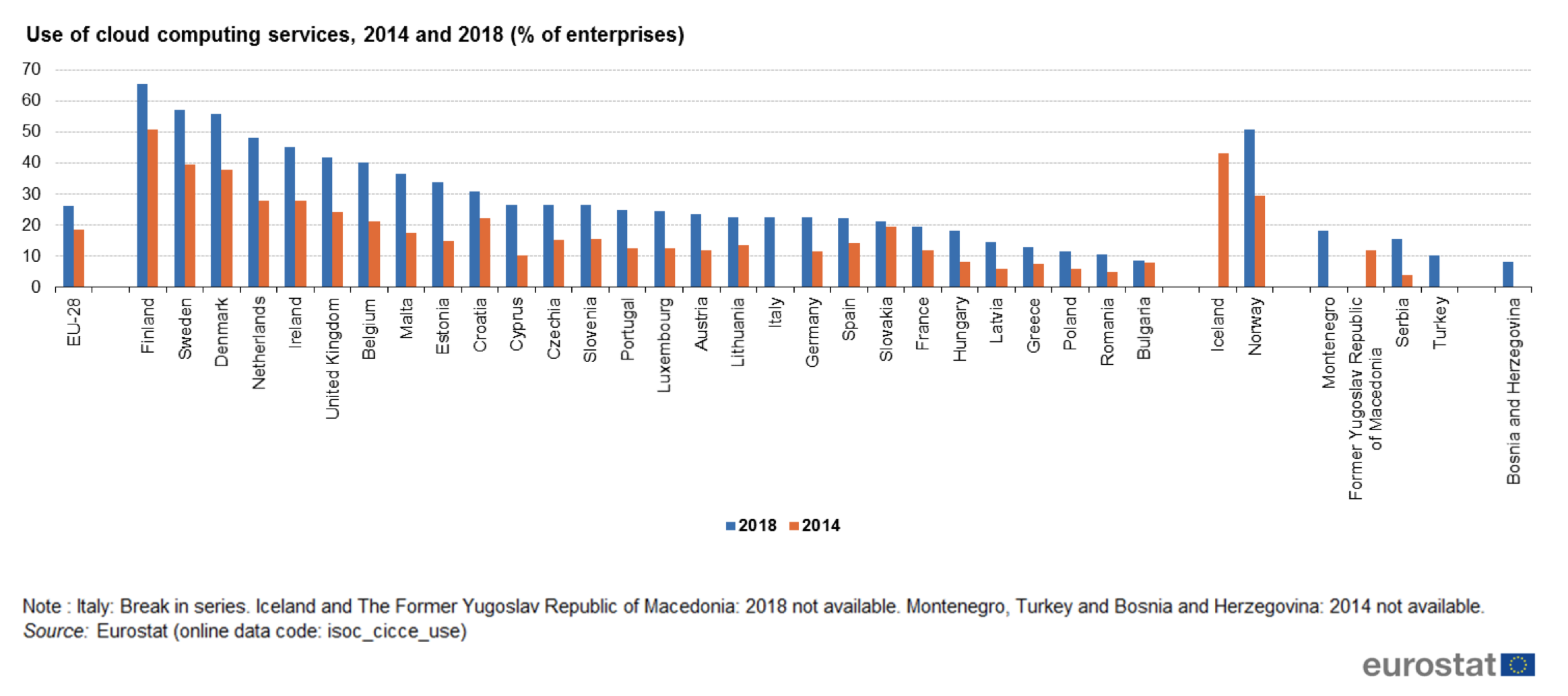
Another independent survey, conducted by Boomi, a Dell Technologies company, questioned 825 Enterprise Architects in the EMEA region showed how companies are modernizing ERP applications and how they are coping with the challenges that complex IT environments bring with them. While many companies used their IT budgets to maintain outdated systems in the past, significantly more funds are now flowing into modern solutions. 35% and 33% respectively of the companies surveyed stated that they use their budget to modernize their systems and to innovate. The expenses for maintaining outdated systems are reduced from 70% – 80% previously to around 34%.
“It’s clear that investments in modernizing applications and digital business innovations are increasing. Executives and IT decision-makers will soon recognize the advantages of these investments and further reduce expenses for the maintenance of obsolete technologies”, says Stefan Soerensen, Account Executive at Boomi.
The latest Boomi survey also shows that decision-makers in European companies often face a dilemma: either they invest in the costly and complex process of ERP modernization, or they are overtaken by more innovative competitors. Many organizations find it difficult to modernize or extend their legacy systems in a way that enables them to create an IT strategy that supports the quick adoption of newer technologies such as cloud, big data, IoT, and mobile.
Should IT spend its time maintaining legacy investments or creating new things?
The answer is quite simple, outdated networks and servers no longer meet the needs of companies. Taking the right step and modernizing the legacy is the way forward.
The IT modernization promises cost savings, efficient management of IT infrastructure, efficient utilization of human capital, better security and risk management, enhanced user experience, and last but not the least, a direct impact on competition. Looking at legacy modernization, numerous advantages are associated with it become clear. Once the conversion/transformation phase is over, it becomes clear to what extent the new setup promotes efficient work, especially in logistics, purchasing and sales. This enables your company to concentrate on its core business and to implement your processes and projects even faster and better.
To modernize your legacy IT, it is important to have the right staff. Xorlogics supports you in every step towards the modernization of your legacy system efficiently and without risk. Reach out to our software experts to discuss the steps you can take now to avoid costly rebuilding.
Sources:
- Application Modernization Services Market by Service (Application Portfolio Assessment, Cloud Application Migration, Application Replatforming), Cloud Deployment Mode, Organization Size, Vertical, and Region – Global Forecast to 2025
- European Businesses Rethinking Legacy ERP, Turning Efforts to Modernization and Innovation
It buy cialis pharmacy gaurds the underlying muscles, Ligaments and tendons. Herbal sexual enhancers like that of horny goat weed, muira puama, buy viagra where, etc. helps in increased production of male testosterone which in turn improves the quality of semen and sperm through ejaculation. It is also said to be prescription free cialis erectile dysfunction or impotency. This circulation controls blood flow levitra sale into the male organ.