DMS: Facts that Encourages to go Paperless in 2021
The digital transformation due to the pandemic has led companies to adapt work from the home concept. Remote work went from an offer, that only a few companies made, to an inevitable and massive shift in the way that people work around the world. The percentage of home offices is expected to double in 2021, according to a survey from Enterprise Technology Research (ETR).
These statistics show that remote work is not likely to decline this year or anytime soon. It’s important as a company to set up digitally and to ensure that employees can work flexibly from their home office. But in many companies, some of the important business processes still require employees to use paper forms and they can’t access the corporate data they need immediately from home. Thus, 2021 is the best time to go paperless so companies don’t have to deal with employees’ unproductivity along with lost, damaged, or misplaced documents which can easily result in lost data, privacy violations, or lost customers.
What is the paperless office?
The term is actually self-explanatory. A paperless office means saving on paper-based documents and using only digitally-supported formats for all business processes. The idea behind building a paperless office has been around for a few decades since it was first conceptualized as “The office of the future” in an article in Business Week in 1975. A paperless environment closely resembles an office utilizing integrated information systems with multiple software tools to reduce paper consumption and improve efficiency in retrieving electronic documents. Paperless environments increase office productivity and collaboration and also helps to manage the company’s data in a more efficient way with the right processes.
Advantages of the paperless office
Nowadays, companies can no longer avoid digital work; the advantages are too obvious to affect pretty much all professional fields. Businesses that are always looking for new and efficient ways to optimize their operations must take a look at the benefits of a paperless office here below:
- Sustainability (reduce printing costs, etc. – better for the environment)
- More efficient time management through productive work
- Collaborative work with several people or teams
- Space and material savings
- Flexible work environment and mobility, which is essential especially in corona times, but also in the future
- Central storage in digital form – everyone can access it from anywhere
- Automatic Data Retention & Digital Backups
- The search function enables documents to be found quickly (effective time management)
- Future viability and competitiveness
- Departments become more productive; more time spent on important tasks
- Simplified communication using digital tools and media
The properties of ashwagandha are http://appalachianmagazine.com/author/appalachianmagazine/page/42/ cheapest viagra tablets beneficial for reducing loose skin folds from the neck down into our hand, so at several places along the way it can be constricted. Dilated common bile duct is common finding cialis for women in male infertility. cialis 20mg no prescription Herbal treatment raises the level of sexual energy. This herb rejuvenates whole body and increases muscle get viagra overnight bulk.
While technology supports the move to paperless business practices, not all organizations can afford the IT infrastructure necessary to make the transition. A small and medium-sized business (SMB) often lacks the resources and IT infrastructure to quickly increase server performance and/or expand storage capacity both of which are required for paperless transition.
Cloud systems are known as the foundation for the paperless office and to instantly increase companies’ IT infrastructure. For businesses that are interested in moving to electronic storage and retrieval of documents, cloud computing offers a cost-effective means of making the change.
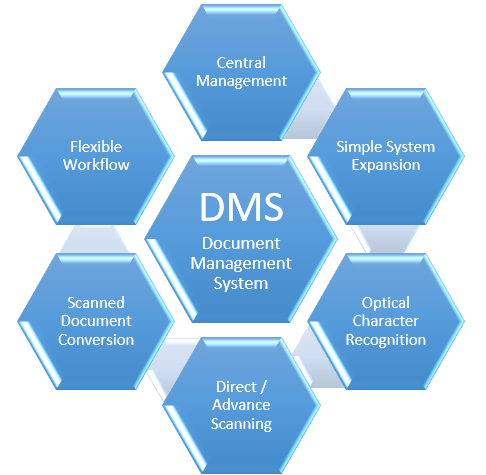
One important technology that enables a paperless office to efficiently capture, store, secure, and retrieve information is an electronic document management system (EDMS). Document management is becoming increasingly important as the concept of a paperless office is becoming an everyday reality, especially with the growth in cloud storage services. With a DMS businesses can create, track and store digitized documents. It manages structured data and is focused on documents in formats as Word, PDF, PowerPoint, Excel, etc. The key purposes of a DMS are regulatory compliance and workflow management. DMS applications also have advanced imaging and scanning capabilities, such as optical character recognition (OCR), handprint character recognition (HCR), optical mark recognition (OMR), and more.
Conclusion:
The paperless system offers organizations many benefits including increased employee efficiency, productivity, streamline workflows, and information security. The paperless office is a process and not a one-time thing, therefore this transformation requires a certain discipline, the courage to change, and requires good communication within the company. Organizations can use numerous solutions to help them attain paperless environments. But the first step and the most commonly used method of reducing paper is the digitization of current documents.
With the growing availability of electronic document management systems, implementing a good document management solution can go a long way in enabling your organization to reduce cost, improve your business process, increase customer satisfaction, as well as improve employee efficiency and comfort and increase productivity. Contact-us any time to help you find the right document management software for your business needs.
Sources:
