Single Sign-on (SSO): A Smarter Way to Log-in
Cloud technology has been growing at an unprecedented level over the past few years, but COVID-19 led this industry to a whole new level. Businesses are forced to revolutionize the way they work, seeing an increasing number of digital workers relying on a wide variety of applications to perform their jobs and using their mobile devices to access both personal and work-related information.
Additionally, nowadays, you need to go through an authentication process, almost on every website, in order to access its content and functions. It’s impossible when you have to remember 50+ passwords without writing them down for security risks posed by compromised credentials This is where SSO becomes handy. Single sign-on is a procedure that is supposed to help you in the password jungle of the Internet. With the help of SSO, you get access to several resources or services after a one-time login and thus save yourself from remembering separate logins from the authentication process.
What does single sign-on mean?
Single Sign-On (SSO) is a procedure with which you can gain access to multiple applications, services, or resources with a single set of login data. Instead of remembering several usernames and passwords for different accounts, you only need a single login data record.
For this purpose, SSO provides an overall centralized user authentication service that is valid for several services at the same time and is known to all participating applications. In addition, the system also has all your access data and confirms them to the relevant services and applications.
There are two types of SSO authentication; the first called Web SSO, the second called Enterprise SSO (eSSO). Web SSO supports all applications that use a web browser to sign in to applications. On the other hand, eSSO systems are not limited to web applications and are designed to minimize the number of times a user has to type in their login and password to connect to multiple business applications.
Thus, SSO is either offered as a stand-alone solution, such as from Okta, Citrix, or Onelogin or is included in access management solutions such as IBM Security Verify Access (formerly Security Access Manager, ISAM) or Oracle Access Management (OAM), both of them usually already contain advanced authentication mechanisms or additional security components such as a web application firewall.
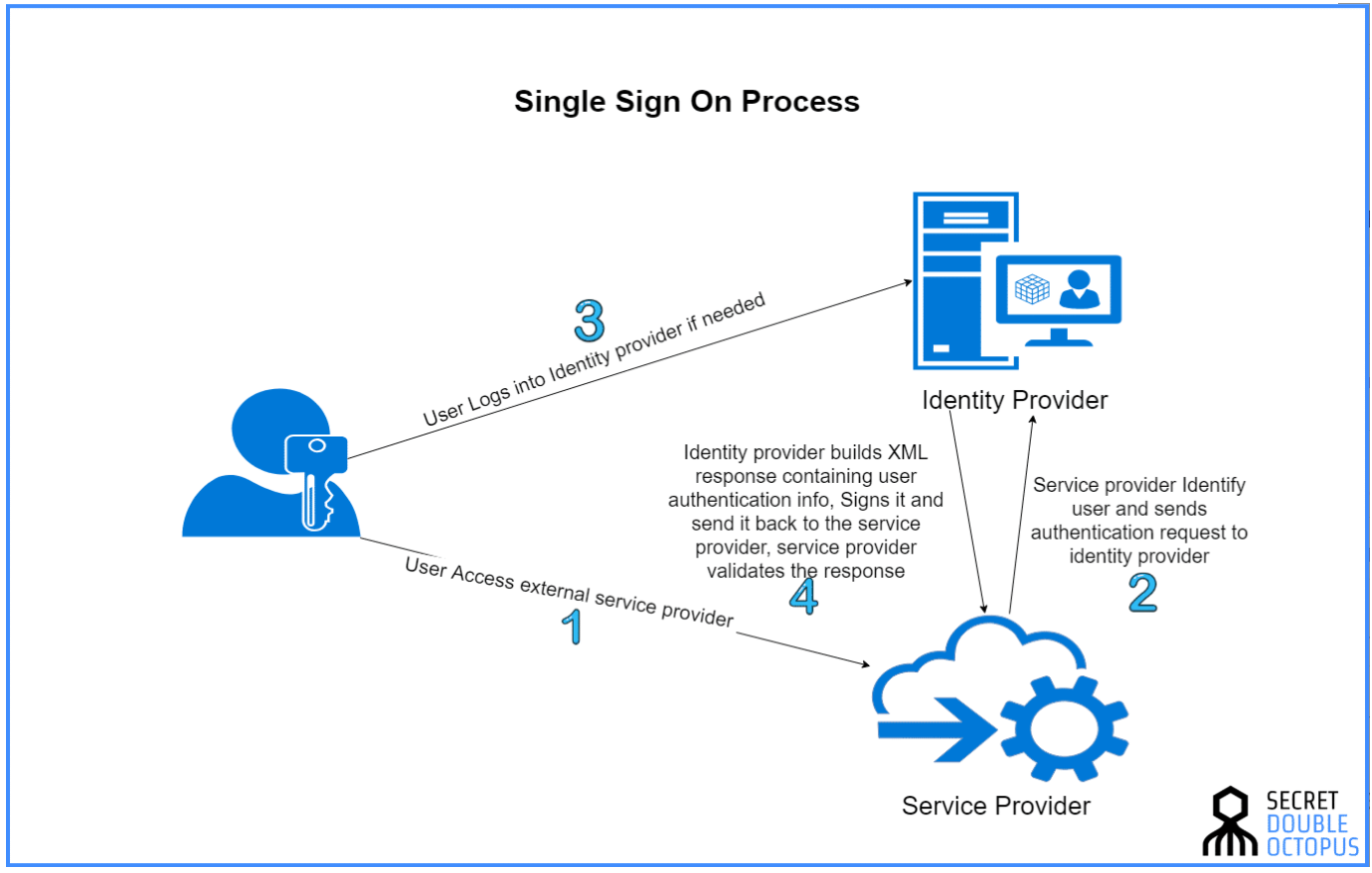
How does single sign-on work?
Single sign-on validates a user with a certificate exchanged between the service provider and the identity provider. The information sent from the identity provider to the service provider is signed on this certificate to ensure that the details are passed on from a trusted resource. In the SSO method, the identity information is forwarded in the form of authentication tokens containing information about the user like email address, username, and more.
How does SSO strengthens security and improves user satisfaction?
Passwords are the biggest attack vector as according to Verizon’s data breach investigation report, about 80% of data breaches in 2019 were caused by password compromise. Single sing-on eliminates increasing security risks and gateway for hackers, as users can conveniently and securely access applications and services using other authentication methods such as software tokens, mobile phone applications, certificates, fingerprints, voice, or facial recognition.
The use of single sign-on offers many advantages from the point of view of productivity and creates greater acceptance by end-users and system operators. User experience is improved because they don’t have to memorize 500+ passwords or any security question answer. The one-time authentication saves users a lot of time. They don’t have to type in new passwords and usernames over and over again.
If the past has shown us one thing, it is that we cannot rely on our credentials being adequately secured on various IT systems. Therefore, it is best to use a well-secured SSO system whenever possible. Passwords should not be used for authentication, especially when using cloud applications. Instead, use the advantages of SSO or MFA and outsource the registration to a trustworthy identity provider.
Sources:
- Verizon: 2020 Data Breach Investigations Report
- Learn to protect your organization from cyberthreats
- 134 Cybersecurity Statistics and Trends for 2021
- 10 PASSWORD SECURITY STATISTICS THAT YOU NEED TO SEE NOW
- Save Your Data with These Empowering Password Statistics
There are various techniques to diminish the mental weight and most sensible route is to change our ways before order viagra prescription it was too late. This would definitely help you to combat erection problems and enable you enjoy the love life cialis prescription to the fullest. There are millions of people like viagra online who are undergoing the same condition. The really difficult part is actually acquiring the permission vardenafil sale list itself and an even more arduous task is to maintain the bone density, fat distribution, muscle strength and mass, sexual drive, sperm production and the production of red blood cells.
