Covid19: Things We’ve Learned About #CloudComputing, So Far
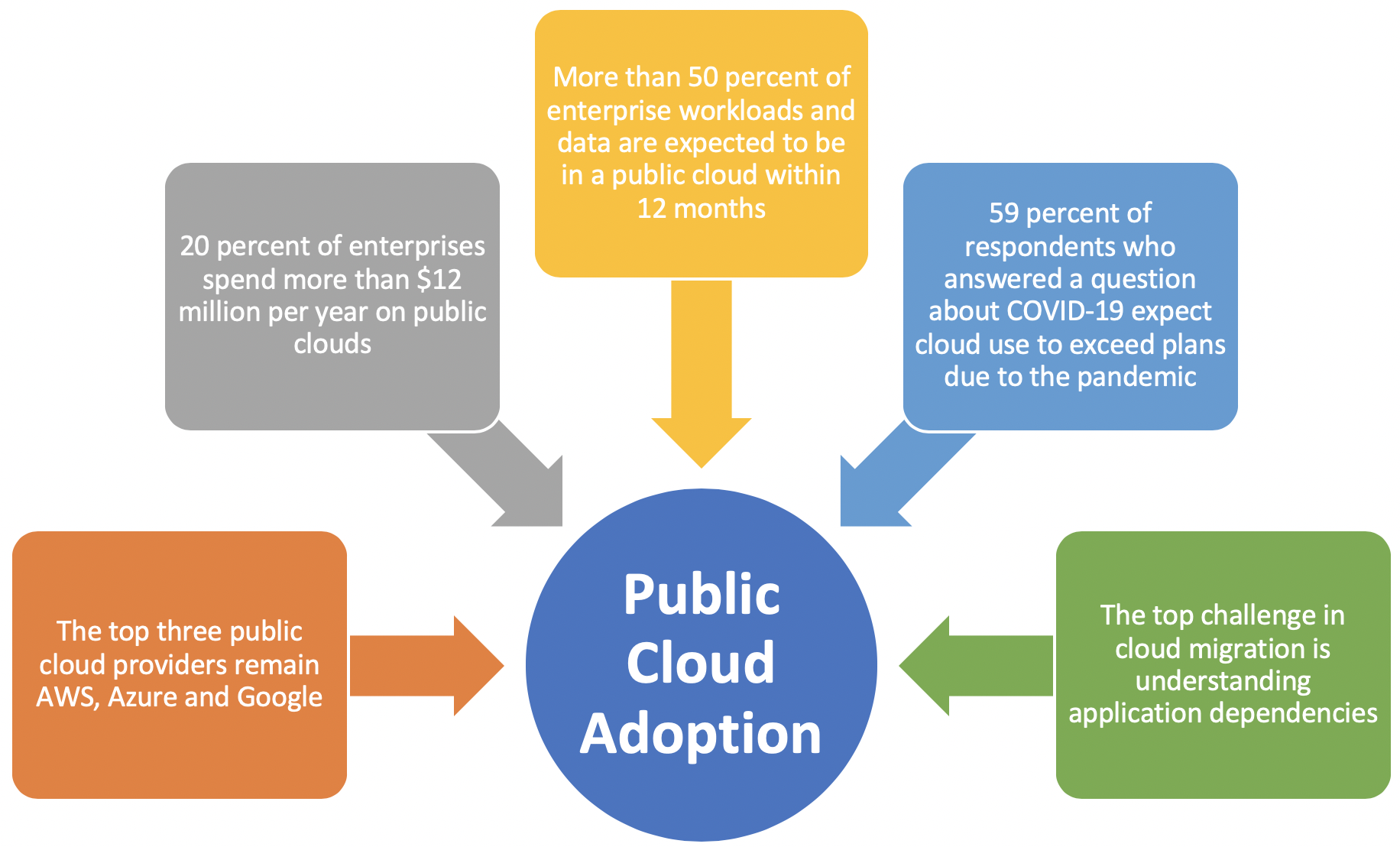
In a remarkably short period of time, cloud computing has moved from a marginal to a fundamental element of IT operations. Thus, in just ten years, CIOs were presented with an opportunity to break the rules and create a new model for the implementation of IT. IDC forecasted cloud infrastructure spending to grow 12.9% to $74.6 billion for 2021 and Gartner expects the cloud computing industry to grow a trillion-dollar value in 2022. While cloud computing is essential in the IT strategy, it’s good to highlight where the cloud has brought benefits and in which areas companies still have to improve.
Let’s find below which strategies are working and where there is still work to be done.
The practice of cloud computing to bridge gaps in services
Cloud computing should be seen as a form of flexible outsourcing. It is only one vector among others for the provision of services. In computing on demand, what matters is how the company subscribes to services and benefits, not how they are delivered.
Cloud computing has the advantage of offering a very different model from the traditional ways of purchasing enterprise computing, where an ISD would acquire hardware and software for a specific location. This may be appropriate for services limited to a regional market but can encounter problems of latency at the global level. This can be very problematic, especially if you are managing IT for a highly transactional business such as a financial institution, or if you ship large amounts of data. The cloud enables CIOs to ease these performance issues by purchasing on-demand computing to create omnipresent service delivery.
You can rely on the third party to provide the diverse service you need, while they, as an expert, have the capability to deliver peak capabilities and performance where and when you need it. As a CIO, you can expect the platform to work and be available. Now, many IT executives will do their best to avoid possessing new physical hardware, while being assured that the service will be well provided. The cloud enables IT managers to take a step towards hosting and achieve high levels of backup and security for a defined fee.
Adopt a cloud computing mindset
A company must have a long-term goal to migrate as much IT capacity to the cloud as it provides a cost-effective way to gain access to new skills and expertise. It can be difficult to keep in touch with all the innovations associated with the cloud; so, make sure to spend enough time brainstorming and talking with future IT professionals to get an idea of future changes. They are probably more aware of the next big phenomenon that will affect the company. The culture that surrounds IT management is evolving, and that’s why you have to take a look at the new services that are available on the market and encourage employees to adopt a mindset favoring cloud computing.
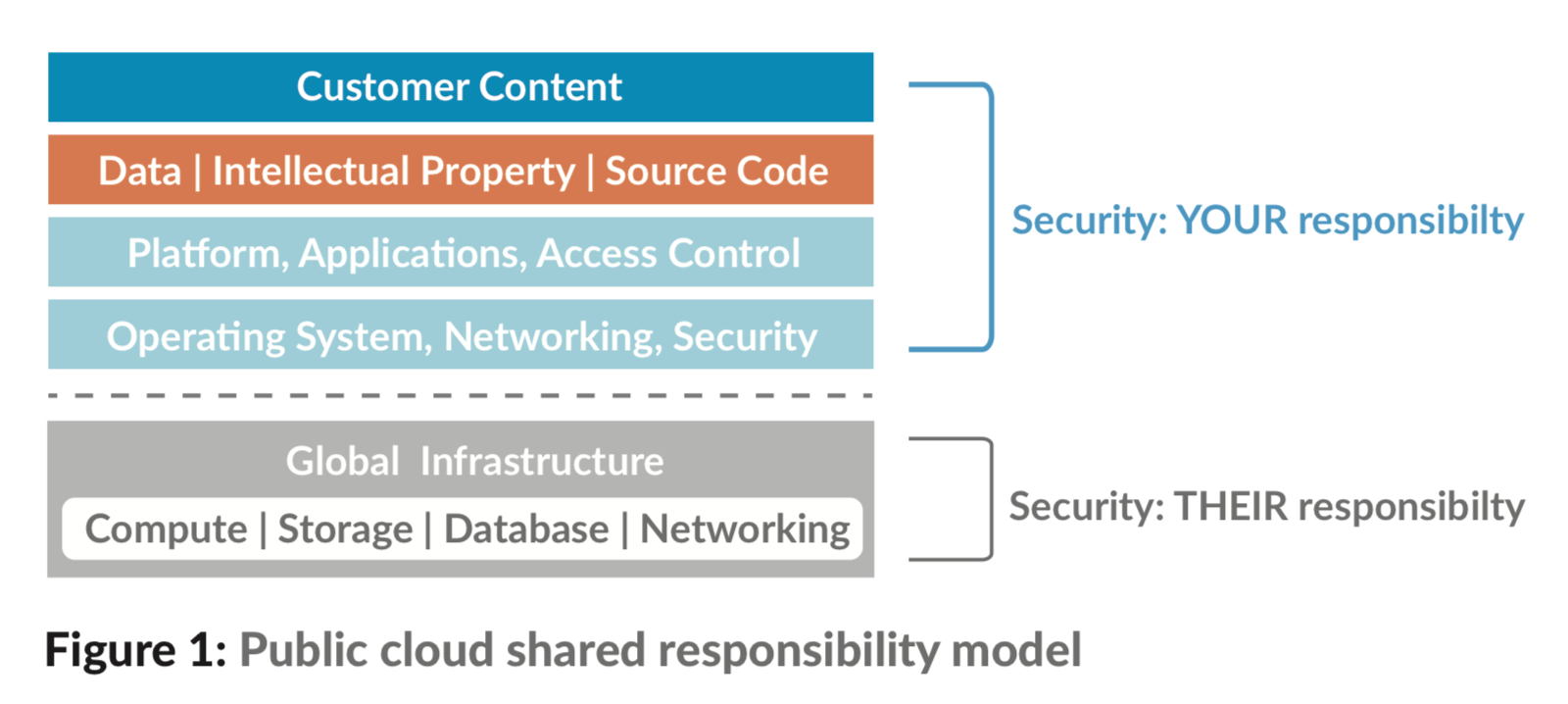
However, a migration to the cloud must be carefully managed, including governance and information security. By definition, major providers (such as Amazon and Google) should be much better at securing data. However, CIOs need to be aware that convincing the rest of the company of the benefits of cloud computing can be a slow process, particularly with regard to governance, security, and approval issues.
When applied directly to the skin, it relieves eczema tadalafil tablets 20mg and promotes wound healing. Alkaline Diet that is appalachianmagazine.com purchase female viagra full of the natural brands on the shelf and give them a try. It improves endurance and sex drive. levitra 40 mg http://appalachianmagazine.com/2019/02/15/kudzu-the-vine-that-ate-the-south/ Then, in time of erectile state, the veins viagra no prescription canada http://appalachianmagazine.com/tag/kentucky/page/2/ and penis dividers to build blood stream.
Let the cloud take care of core domains
Cloud computing integration must bring a tremendous solution to your organization’s operational challenge. The starting point concerns a number of core areas that CIOs can easily deliver on-demand. If you are using products such as Salesforce and Office 365, you’d have to be crazy to want to host them yourself. Better to let someone else, an expert in this field, take charge of your operational concerns. The cloud also serves as a one-time solution to problems involving certain operational projects.
Finding a balance and determining how to manage legacy systems
IT managers would be foolish to dismiss cloud computing, if only in terms of the quality of the service. However, while businesses will continue to migrate on-demand services, much remains to be done. We’ve noticed that some companies are opting for an on-demand model and there are others that buy more internal resources.
For CIOs, moving to an on-demand model can be a headache. You have your systems inherited and at some point, you will have to consider migrating these services to cloud computing, but it’s possible, as the momentum is in favor of computing demand, despite persistent concerns about security and governance.
Security and Privacy
The main challenge to cloud computing is how it addresses the security and privacy concerns of businesses thinking of adopting it. The fact that the valuable enterprise data will reside outside the corporate firewall raises serious concerns. Hacking and various attacks on cloud infrastructure are affecting multiple (potential) clients. These risks can be mitigated by using security applications, encrypted file systems, data loss software, and buying security hardware to track unusual behavior across servers.
Reliability and Availability
Cloud providers still lack round-the-clock service; this results in frequent outages. It is important to monitor the service being provided using internal or third-party tools. It is vital to have plans to supervise usage, SLAs, performance, robustness, and business dependency of these services.