What are the best monitoring practices for extending IT visibility?
Extending IT visibility and monitoring is crucial for maintaining the health and performance of your IT infrastructure. As businesses rely heavily on their IT infrastructure to drive productivity, streamline operations, and deliver exceptional customer experiences, they must ensure that their IT systems are running smoothly. And it’s possible to overcome this challenge by setting up effective monitoring practices for extending IT visibility.
Why is IT monitoring important?
First and foremost, IT monitoring provides businesses with unparalleled visibility into their systems and networks. By constantly analyzing the performance and health of your infrastructure, you can swiftly detect any issues or anomalies before they escalate into major problems. This proactive approach allows for quick troubleshooting and minimizes downtime.
Furthermore, effective IT monitoring enables businesses to optimize their resources. By closely tracking usage patterns and resource allocation, organizations can identify areas where efficiency can be improved or costs can be reduced. This data-driven approach empowers decision-makers to make informed choices that align with the goals of the business.
Another key benefit of IT monitoring is its ability to enhance security measures. With cyber threats growing more sophisticated by the day, constant vigilance is vital to protect sensitive data and prevent potential breaches. Monitoring tools provide real-time insights into network traffic, allowing for immediate detection of suspicious activity or unauthorized access attempts.
Last but certainly not least, IT monitoring helps businesses stay compliant with industry regulations and standards. By continuously monitoring systems for compliance requirements such as data privacy laws or cybersecurity protocols, organizations can avoid costly penalties and maintain customer trust.
Here below are some best monitoring practices to help you achieve this:
- Define Clear Objectives: Start by defining clear objectives for your monitoring efforts. Understand what you need to monitor, why you need to monitor it, and what the expected outcomes are. This will help you focus your efforts on the most critical areas.
- Comprehensive Coverage: Ensure that your monitoring covers all critical components of your IT infrastructure, including servers, networks, applications, databases, and cloud services. Gaps in coverage can lead to blind spots.
- Real-time Monitoring: Implement real-time monitoring solutions to detect issues as soon as they occur. Real-time alerts and notifications allow you to address problems promptly, minimizing downtime and user impact.
- Historical Data: Collect and store historical monitoring data. This data can be invaluable for trend analysis, capacity planning, and identifying long-term performance issues.
- Thresholds and Baselines: Set appropriate thresholds and baselines for your monitored metrics. Thresholds trigger alerts when values go beyond acceptable limits, while baselines help you understand normal performance patterns.
- Alerting and Escalation: Configure alerting mechanisms to notify the right people when issues arise. Establish clear escalation procedures to ensure that critical problems are addressed promptly by the appropriate teams.
- Visualization: Use dashboards and visualization tools to present monitoring data in a user-friendly and informative manner. This helps teams quickly grasp the state of the environment.
- Automation: Implement automation for routine tasks, such as restarting services or scaling resources based on monitoring data. Automation can help mitigate issues before they impact users.
- Scalability: Ensure that your monitoring solution can scale with your infrastructure. As your organization grows, your monitoring system should be able to handle increased data volume and complexity.
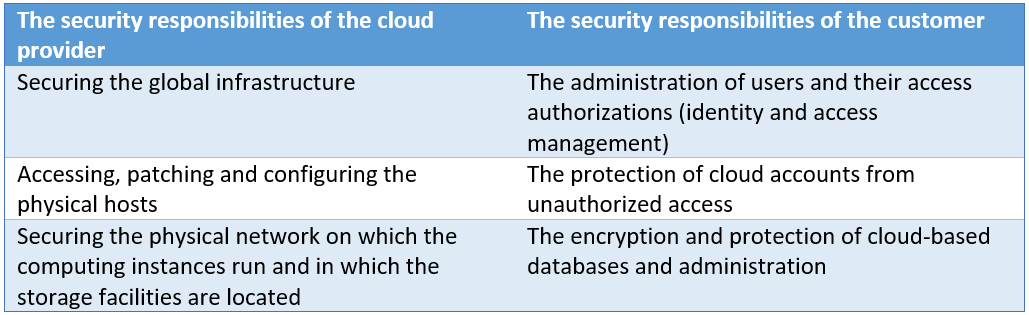
- Security Monitoring: Don’t forget about security monitoring. Monitor for suspicious activities, unauthorized access, and vulnerabilities to protect your IT environment from cyber threats.
- Regular Review and Optimization: Regularly review your monitoring setup to ensure it aligns with your objectives. Optimize your monitoring configurations as your IT landscape evolves.
- Documentation: Document your monitoring setup, including configurations, alerting procedures, and incident response plans. This documentation is valuable for onboarding new team members and maintaining consistency.
- Training and Skill Development: Invest in training for your IT and operations teams to ensure they are proficient in using monitoring tools effectively.
- Compliance and Reporting: If your organization needs to adhere to specific compliance standards, ensure that your monitoring practices align with those requirements. Generate regular reports to demonstrate compliance.
- Cloud and Hybrid Environments: If you’re operating in a cloud or hybrid environment, adapt your monitoring strategy to accommodate the dynamic nature of these setups. Cloud-native monitoring solutions can be beneficial.
By following these best monitoring practices, you can enhance IT visibility, proactively address issues, and ensure the reliability and performance of your IT infrastructure. Monitoring is an ongoing process, so regularly assess and refine your approach to meet changing business needs and technological advancements.