The Top Must-Have Leadership Skills for Successfully Leading a Digital Business
In today’s connected & constantly evolving business landscape, the role of a leader has become more crucial than ever before. Strong leadership skills are essential for navigating the ever-changing tides of success. Understanding and possessing the right set of qualities can make all the difference in effectively leading a digital business to new heights.
The rise of technology and its integration into every aspect of our business has resulted in a highly competitive marketplace where organizations must adapt quickly or risk being left behind. In this environment, it is not enough for leaders to simply possess traditional management skills; they must also have a clear understanding of how technology can be leveraged to drive growth and innovation.
One of the most significant ways in which technology has impacted businesses is by breaking down geographic barriers and enabling global connectivity. This means that leaders must be able to manage diverse teams across different time zones and cultural backgrounds while ensuring effective communication and collaboration. This requires excellent interpersonal skills, as well as an understanding of cultural differences and how to bridge them.
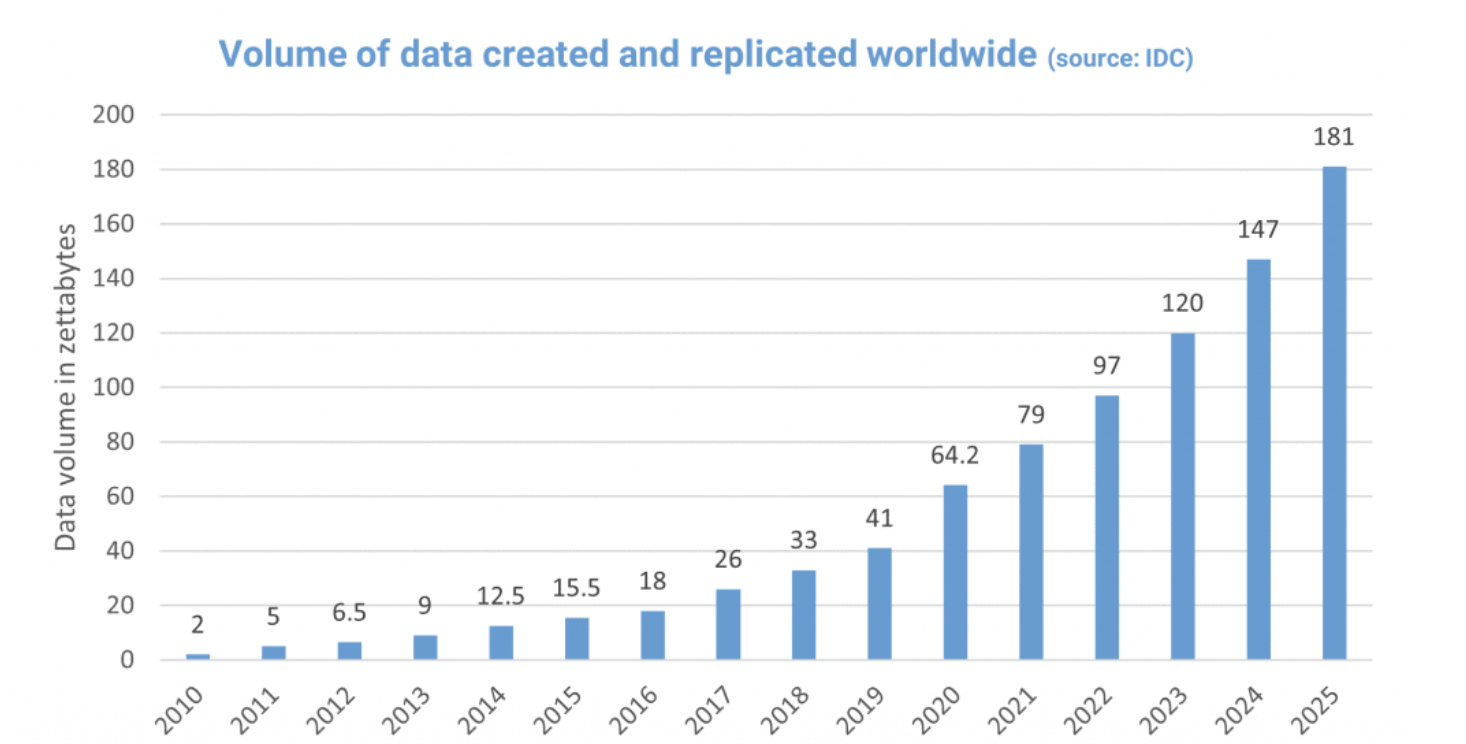
Moreover, with the increasing use of data analytics in decision-making processes, modern leaders need to have a strong grasp of technological tools and platforms. They must be able to analyze large sets of data to identify trends, make informed decisions, and create effective strategies for their digital business.
In addition to technical proficiency, strong leadership is also crucial for creating a culture that embraces change and innovation. In this fast-paced digital era, businesses can no longer afford to stick with outdated practices; they must continuously adapt and evolve to remain relevant. A leader who can inspire their team members to embrace the change!
Overview of the top must-have leadership skills for leading a digital business:
With the rapid advancement of technology, it has become even more imperative for leaders to possess specific skills that are essential for leading a digital business. Here are the top 7 must-have leadership skills that are necessary for effectively leading a digital business:
Adaptability and agility
The ability to adapt and be agile in the ever-changing digital world is one of the most critical leadership skills. Digital businesses operate in a constantly evolving environment, where new technologies emerge, consumer behaviors change, and market trends shift rapidly. Therefore, it is essential for leaders to have the ability to adapt their strategies and approaches accordingly. This means being open-minded, willing to learn new things, and being able to think outside the box. Leaders must also be flexible enough to pivot their plans when needed without hesitation. A leader who can quickly adapt to these changes and make strategic decisions will lead their team toward success.
Strategic thinking & problem-solving
Strategic thinking and problem-solving are two essential skills that digital leaders must have to navigate through complex challenges and make data-driven decisions. They need to have a clear vision of where they want their business to go and develop effective strategies to achieve those goals while staying ahead of their competitors. Additionally, leaders must have strong analytical skills to make data-driven decisions in this data-rich era. They need to be able to interpret complex data sets from multiple sources and use them for strategic planning and decision-making.
So what exactly do we mean by strategic thinking? It involves the ability to envision the bigger picture and see beyond immediate situations. A strategic thinker understands how all the pieces of a puzzle fit together and can anticipate potential challenges or opportunities. They are proactive rather than reactive, always looking for ways to improve processes and achieve long-term goals.
Digital literacy
Having knowledge of emerging technologies and understanding how they impact the industry is crucial for leading a digital business. With technology constantly evolving and becoming increasingly integrated into every aspect of business operations, leaders need to have a strong understanding of the latest tools and platforms in order to effectively lead their teams.
Data analysis
Data plays an integral role in driving business growth in the digital era. It is necessary for leaders to have the know-how to analyze data from various sources such as social media analytics, customer feedback, website traffic patterns, etc., to make informed decisions about marketing strategies.
Communication and collaboration skills
Communication and collaboration are two key skills that every effective leader needs to possess in order to successfully lead a digital business. Effective communication skills are essential when it comes to technological proficiency as they allow leaders to clearly articulate & convey technical concepts or ideas with team members who may not have a background in technology. Being able to bridge this gap between technical jargon and non-technical team members can help improve efficiency and collaboration. As in a digital business setting, where teams are not geographically present and working remotely, strong communication skills become even more important. Leaders must be able to adapt their communication style according to the needs of different individuals and utilize various tools such as email, video conferencing, and project management software to stay connected with their team.
Collaboration is another essential skill for leading a digital business successfully. With teams working from different locations or time zones, it is imperative for leaders to create an environment that promotes teamwork and collaboration among remote workers. This can be achieved through regular check-ins with each team member, establishing clear roles and responsibilities, setting up virtual brainstorming sessions and utilizing collaborative tools such as shared documents or project management software.
Cybersecurity Awareness
In the digital realm, cybersecurity is a top concern. Leaders must be aware of the latest cyber threats and take proactive measures to protect their business and customer data. A breach can have severe consequences, both financially and reputationally.
Emotional Intelligence
Emotional intelligence is essential for building strong relationships within the team and with customers. Leaders should be empathetic, understanding, and capable of resolving conflicts constructively. It’s crucial for creating a positive and productive work environment.
Leading a digital business requires a unique skill set that combines traditional leadership qualities with an understanding of the digital landscape. Embracing technology, fostering a collaborative culture, adapting to change, and making data-driven decisions are just a few of the essential skills for digital leaders. By developing these skills, aspiring leaders can navigate the digital business landscape successfully.