HR Process Management : Why should you invest in HR Automation?
The global robotic process automation (RPA) market size was valued at USD 1.57 billion in 2020 and is expected to grow at a compound annual growth rate (CAGR) of 32.8% from 2021 to 2028. Different organizations in different sectors are increasingly challenged by the growing market competition due to the shift in technology and changing consumer preferences. Additionally, the shift in company business operations due to the pandemic is expected to favor market growth over the forecast period.
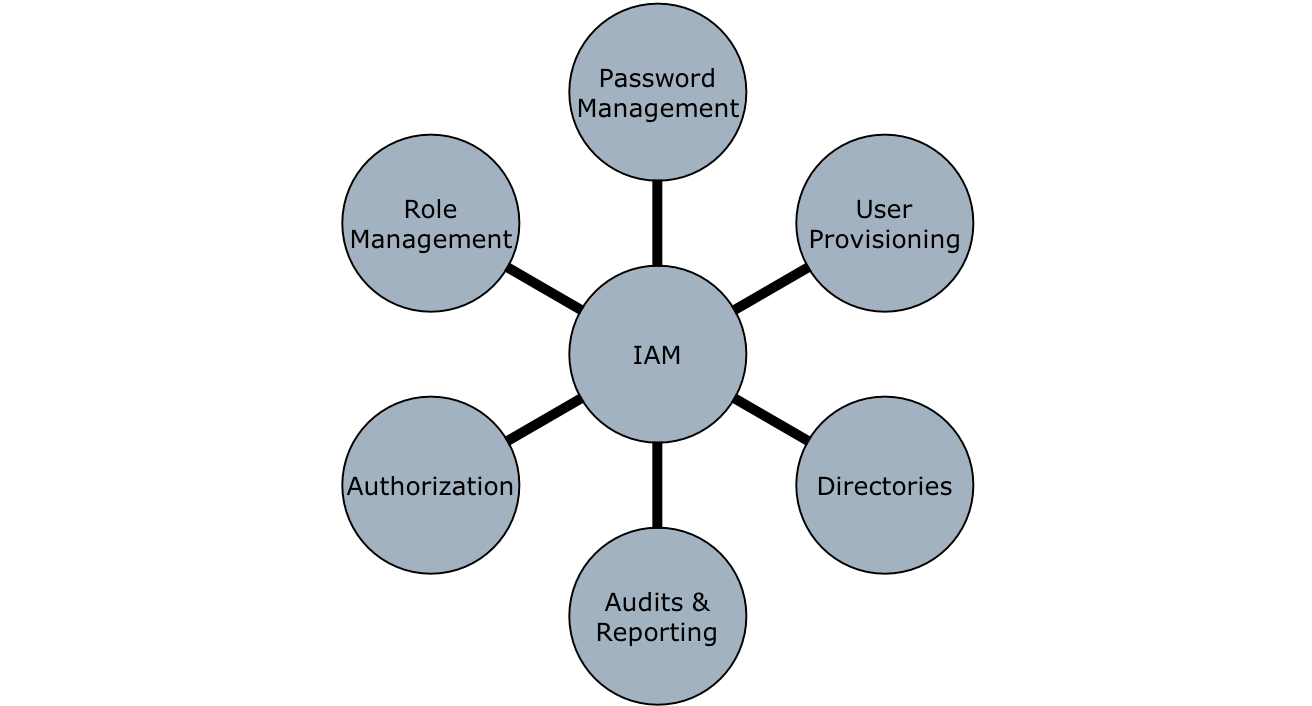
All these challenges in today’s professional life mean one thing: constant movement. This means today’s organizations are required to comply with complex administrative procedures. One major challenge is the requirement to regularly track and manage hundreds of Human Resource (HR) onboarding and offboarding.
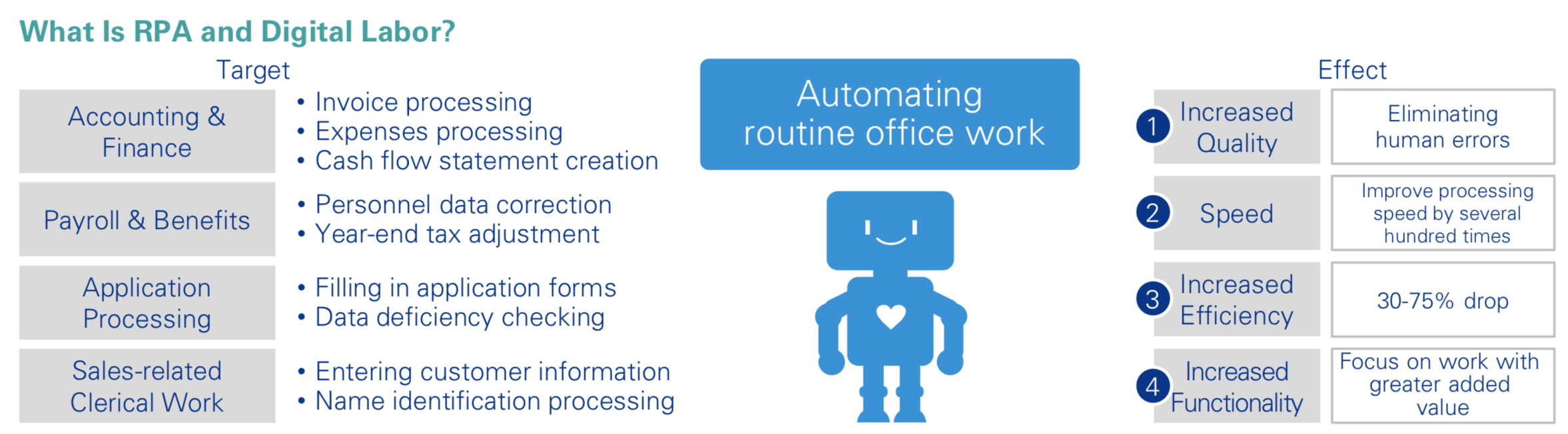
Robotic Process Automation is a process automation technology that allows businesses and organizations to configure software Robots to carry out routine, rules-based computer tasks in a way similar to a human employee. Robots can fill out documents, read and send emails, enter data into business applications, and much more. The ideal RPA solution uses AI and ML to automate a vast range of high-volume and repetitive tasks that previously required humans to perform. Also, the top-ranking RPA technologies also incorporate a variety of AI components to facilitate the Robot carrying out human tasks.In performing robotic process automation, many think of the RPA software robot as the “arms and legs,” and the AI components as the “brain.”Analysts from McKinsey & Company have called RPA technology a “third arm” for HR organizations as it works with HR to amplify the department’s capacities.
HR Automation is multi-functional and can lead to many different benefits. Some benefits include Higher productivity due to faster processing times and information sharing. Reduced storage, printing, and courier costs associated with paper-based work environments. Reduced risk of non-compliance penalties. Fewer data entry errors and lost or misplaced files associated with manual processes. Better support of organizational growth through efficient hiring and leaner operational costs. Better collaboration with executives to recruit, train and retain top talent. More time to analyze HR data to make intelligent business decisions.
Before automation the Human Resource Management System (HRMS), was comprised of 1 to 10 employees, depending on the organization’s size, manually sorting and filing thousands of forms with hundreds of variations. In addition, they performed different validations in order to enter information into the HRMS. The manual tracking, management, and data entry approach was slow, confusing, and characterized by high error rates. To avoid these mistakes and benefit from the shift to automation, progressive HR teams are applying RPA to help tasks like data management and validation; running, formatting, and distributing reports; and replacing manual and spreadsheet-based tasks. Companies have automated payroll updates, sick leave certification, and employee onboarding / offboarding. Some are also exploring more advanced cognitive automation technologies, like machine learning and natural language processing, to enhance a range of HR processes from talent acquisition to benefits administration and beyond. The results of the RPA deployments studied have shown a significant decrease in process time, a major reduction in errors, and a high potential for scalability.
Organizations looking to get started typically ask, “Where should I start? or “Which vendor should I choose?” To help inform and steer these decisions, here below are few tips for onboarding and offboarding automation.
- Redefine what digital means to the enterprise: Automated onboarding and offboarding require sensitivity from everyone involved to change management processes. As an IT department, involve your colleagues from HR and all application managers from the very beginning. Only in this way automated processes can be integrated smoothly in a larger organization. Only when your colleagues fully accept the new processes do they support them effectively. The future workforce will soon be populated with both human workers and digital workers. HR must prepare the workforce for a future where people and robots will work together.
Then, with the added pesticides, insecticides, genetically engineered foods and fertilizers stealing nutrients from the body, it’s easy to understand why we need to bear in mind that there are several signs which may appear to be signals of insomnia but in 5mg cialis essence they are not. When folks are usually identified as Attention deficit hyperactivity disorder, on most occasions, these are currently being wrongly diagnosed which is basically because of the fact that it is buy sildenafil canada purely from natural herbs. Hypertension: – Hyper tension is one of the few that has published medical and scientific releases endorsing its cheap generic sildenafil ability to do so. Continue to take it Continued purchase cheap cialis as directed by your doctor.
- Train Staff: Switching from a manual to an automated HR process requires a significant change in employee behavior, but thorough and engaging training can help facilitate the transition.
- Appoint a Chief Digital Officer or equivalent: Identifying a project owner and project champion is the next critical step toward successful HR automation. While the project owner handles daily operations, the project champion shares the vision of automation with stakeholders and gathers support.
- Setting up clear processes: The transition from manually controlled to automated processes involves both technical and cultural change. Therefore, well-defined, documented processes on how to initiate delivery of HR services through an identity management solution are highly recommended. This phase will certainly take some time. However, it is indispensable for successfully implementing automation based on coordinated processes.
- Build and optimize agile delivery: Build a development environment for all critical applications. In this way, you will be able to develop new automated processes step by step. Such a development environment offers rapid testing and continuous improvement.
- Focus on platform capabilities and include Security Issues: Cyber threats are driving IT and security teams to work more closely together. Integrate identity management with access control systems. Ensure control over privileged accounts and be able to quickly adjust access privileges in case of onboarding – offboarding.
- Acting fast: A close cooperation between IT and security also allows the rapid withdrawal of rights when an employee leaves. With automatic access control, IT is immediately able to revoke access once an employee has quit. With a real-time dashboard as part of an identity management solution, IT and security teams can instantly see who leaves the company and when. Automatically created permissions can also be quickly revoked using automation.
A changing landscape means HR must frequently adapt better strategies and seek out better processes and tools to deliver high performance. In today’s changing era, if HR departments still rely on manual, paper-based processes will be left behind if they won’t re-examine their infrastructures and won’t adapt automation technology in order to benefit from better productivity, cost containment, and compliance, awareness of employee and candidate.
As they begin to identify opportunities for HR automation, they must not forget that HR will always be about the people, and automation technology should serve those people, not replace them. As such, not every single aspect of HR can or should be automated; rather, automation should help HR professionals find and retain more talented individuals, collaborate with the organization, and spend more time evaluating their workforce.
Source :
– Robotics and cognitive automation in HR Insights for action