Automation in Public Sector
The public sector has long been associated with slow-moving bureaucracy and outdated processes. However, with the rise of automation technology, the landscape is rapidly changing! Automation is revolutionizing the way that governments operate by streamlining processes, increasing efficiency, reducing costs, and enhancing the delivery of services to citizens. It involves the use of technology and software systems to automate repetitive tasks, streamline processes, and enable data-driven decision-making with little or no human intervention. In recent years, automation has gained popularity in the public sector as well. Government agencies are using automated systems to improve their operations and provide better services to citizens. For instance, they’re automating administrative tasks such as data entry and document processing that were previously done manually.
Service automation is also becoming popular in the public sector where AI-powered chatbots assist citizens in answering queries about government programs or services. This helps governments provide timely assistance while reducing workloads on overworked employees who would have spent hours attending to phone calls from the general public seeking answers on various issues.
Automation technology offers endless possibilities for making our lives simpler by taking care of tedious yet essential tasks so we can focus more on important things like innovation!
The role of automation in the public sector
Automation plays a crucial role in the public sector by transforming traditional processes into digitized and streamlined systems. It can be used to optimize tasks such as data entry, document processing, and communication between departments. By automating these routine tasks
, government employees can redirect their time toward more meaningful work. Here below is a short list of how automation can benefit the public sector:
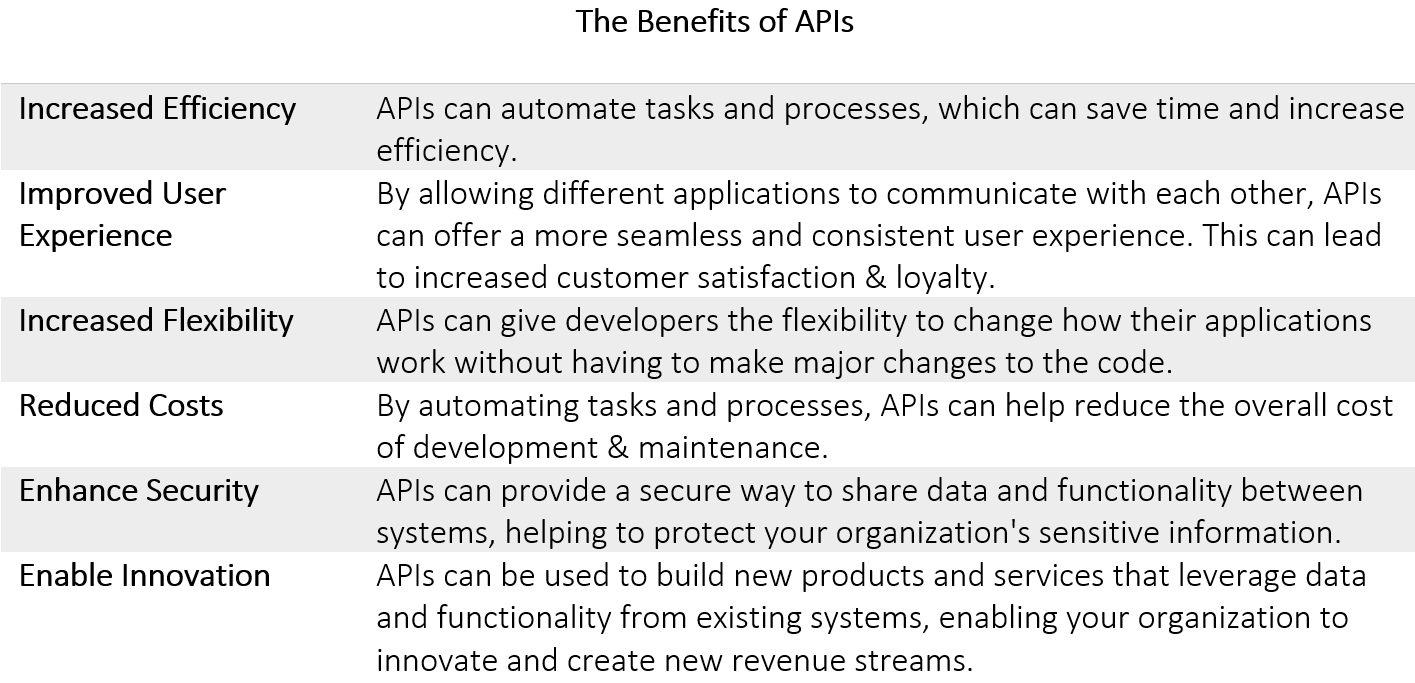
- Streamlined Processes: Automation eliminates manual, paper-based processes and replaces them with digital workflows. This streamlines operation reduces paperwork and minimizes errors. For example, automated systems can handle tasks such as processing applications, managing permits, and conducting compliance checks, resulting in faster and more accurate outcomes. Furthermore, automation helps ensure consistency in decision-making across different departments by using standardized rules and algorithms. This leads to better compliance with regulations while reducing the potential for bias or errors in judgment.
- Citizen Services: Automated systems enhance the delivery of public services to citizens. Online portals and self-service platforms allow citizens to access information, submit applications, make payments, and interact with government agencies conveniently and efficiently. This reduces the need for in-person visits and enables 24/7 access to services.
- Data Management: Automation enables efficient data collection, storage, analysis, and reporting. By automating data entry and integration processes, public sector organizations can make better use of their data assets for evidence-based decision-making, policy formulation, and program evaluation.
- Cost Savings: One of the most important roles of automation in the public sector is to increase efficiency and reduce costs. With automated processes, a reduction in costs associated with manual labor, repetitive tasks, and administrative overhead is achieved. By automating routine processes, there is less chance for human error and delays, leading to faster turnaround times for government services. Thus public sector organizations can allocate resources more effectively, optimize staff productivity, and redirect human efforts towards higher-value activities.
- Compliance and Regulation: Automated systems help enforce compliance with regulations and streamline auditing processes. For example, financial management systems can automate accounting procedures, generate real-time reports, and ensure adherence to financial regulations and standards.
Automation allows governments to focus on providing higher-quality services that meet citizens’ needs while saving time and money. As we continue towards an increasingly digital age, it is becoming more apparent that adopting automation will lead us toward a future where public sectors are optimized through service automation.
Trends in the public sector:
- Robotic Process Automation (RPA): RPA involves the use of software robots or bots to automate repetitive, rule-based tasks. It is being widely implemented in the public sector to automate administrative processes, such as data entry, form filling, and document verification.
- Artificial Intelligence (AI) in Chatbots: Chatbots powered by AI technologies are being employed by government agencies to provide instant responses to citizen queries, assist with online services, and offer personalized assistance. AI enables chatbots to understand natural language, analyze data, and provide accurate and timely information.
- Data Analytics and Predictive Modeling: Governments are leveraging automation to analyze vast amounts of data and extract meaningful insights. By using predictive modeling techniques, they can anticipate trends, identify patterns, and make informed decisions. This helps in areas like resource allocation, public safety, and urban planning.
- Intelligent Document Processing (IDP): IDP combines AI, machine learning, and optical character recognition (OCR) technologies to automatically extract information from unstructured documents. Public sector organizations use IDP to automate tasks like invoice processing, contract management, and records management.
- Workflow and Case Management Automation: Automation is applied to streamline workflow and case management processes in various public sector domains, including permit applications, license renewals, benefits administration, and legal proceedings. Automated systems track and manage cases, assign tasks, and provide real-time status updates.
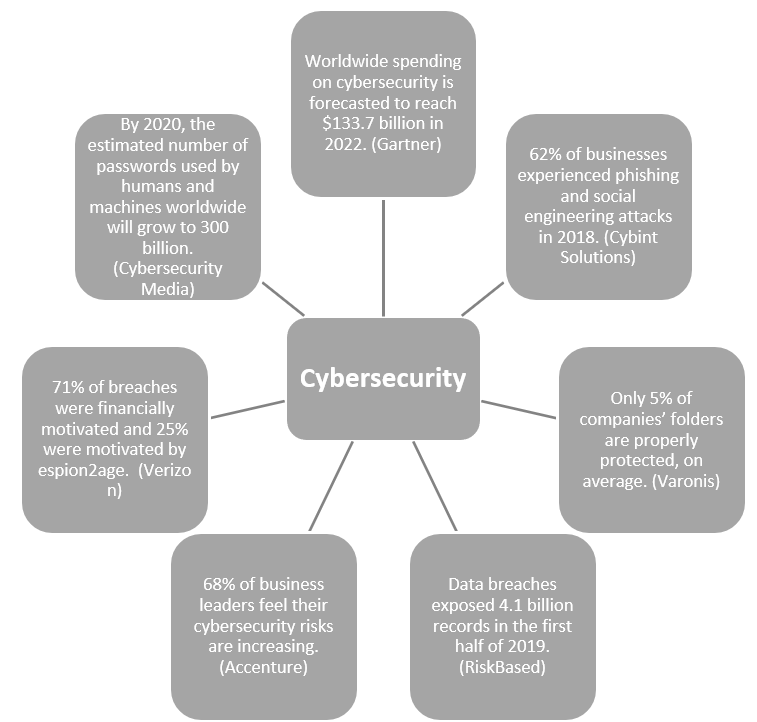
- Cybersecurity Automation: With the rise in cyber threats, automation plays a crucial role in strengthening cybersecurity measures in the public sector. Automated tools can detect and respond to security incidents, analyze network traffic for anomalies, and patch vulnerabilities across systems.
- Smart City Automation: Governments are embracing automation to build smarter cities. Automated systems are utilized for traffic management, parking systems, waste management, energy consumption monitoring, and other urban services. This enhances efficiency, reduces costs, and improves the quality of life for citizens.
- Digital Service Delivery: Public sector organizations are increasingly digitizing their services and automating the delivery of online services. This includes processes like online payment systems, electronic document submission, and appointment scheduling, making it more convenient for citizens to access government services.
- Citizen Engagement Automation: Automation technologies are leveraged to engage citizens more effectively. Chatbots and virtual assistants can guide citizens through government websites, assist with applications, and provide information on services and policies. Automated systems also facilitate feedback collection and sentiment analysis.
- Internet of Things (IoT) Automation: IoT devices and sensors are used to automate various public sector operations, such as monitoring air quality, managing infrastructure, and optimizing resource usage. IoT automation enhances data collection, analysis, and decision-making processes.
These are just a few examples of automation trends in the public sector. As we move towards an increasingly digital world where technology continues to advance, new automation solutions are likely to emerge, further transforming the way governments operate and serve their citizens. By embracing automation technologies today, governments can build more resilient institutions that are better equipped to handle future challenges efficiently while providing top-class services for their citizens.