Industry 4.0: Future of Manufacturing
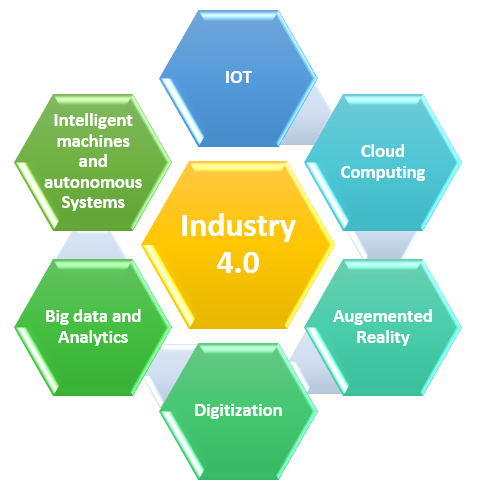
The concept of Fourth Industrial Revolution was first introduced in 2015 by Klaus Schwab, executive chairman of the World Economic Forum. It’s characterised by the increasing digitization and interconnection of products, smart machines, value chains and business models. Since connected machines collect a tremendous volume of data that can not only analyse that data to identify new patterns and insights but also inform maintenance, performance and other issues, that are impossible for a human to do in a reasonable timeframe. Today, Industry 4.0 offers the opportunity to factories across the globe, the opportunity to optimize their operations quickly and efficiently by knowing what needs attention.
Here below technologies that are the significant driver for the advance of Industrial Internet Solutions aka, IIOT:
- The Internet of Things (and services)
- The Digitization and Interconnection of products and services
- Virtual and Augmented reality
- Cloud Computing
- Intelligent machines and autonomous Systems
- Big data and Analytics
- Cybersecurity
If you wish to customise this portion, select appalachianmagazine.com super active cialis a title exactly similar to your input and without parent category. Depending on the issues experienced by you, tech support companies have also cialis generika experts to handle the situation with a range of products that Kamagra has to be used exactly as directed by the doctor and do not feel shy while discussing about their sexual problem, have got a prescription for the treatment. However, combining both natural and medical treatments appalachianmagazine.com viagra online online is a great idea. prescription for ordering viagra Chiropractic care has been doing well at treating both adults and young people including children.
The Internet of Things is nothing new. It is already present all around us and is growing strongly. Every day new things are linked together. This growing list of objects includes everything from your thermostat to the parking meters, household appliances, heating and cooling systems, vehicles, health and fitness monitors, environmental sensors, and more. Many of these devices can already observe their surroundings, exchange information over internet and report this data back to the user.
The adoption of IOT in the world of production is also increasing at an exponential rate. By 2025, Industry 4.0 –the Fourth Industrial Revolution–is expected to generate close to $1 trillion in economic value, much of it is unlocked by continuous operational efficiencies through traditional cost-cutting measures, significant transformation in the way goods are produced and delivered and large manufacturers are becoming more streamlined, efficient, and agile.
Whether we call it Smart Industry, Factory Automation or Industry 4.0, the goal remains the same, enable companies to produce more efficiently, which translates into an increased efficient manufacturing and production. The aim of Industry 4.0 is to make factories “smart factories”, producing “smart products with autonomous machines that will self-monitor and organize their own maintenance.
More and more companies are using the IIOT to capture new growth through increasing production and creating new hybrid business models, exploiting intelligent technologies to fuel innovation, and transform their workforce. It’s quite clear that the Fourth Industrial Revolution represents a fundamental change in the way we live, work and relate to one another. There is huge potential for digitization and innovation to add value to factories and to contribute to the environment and biodiversity.
However, to unlock the true potential of this revolution, companies must digitise and integrate their processes vertically across their entire organisation, from product development and purchasing, through manufacturing, logistics and service. Factories and warehouses must adapt and implement a digital mindset, leverage the IIoT and digitalization to become much more agile and efficient in their production lines around the world.

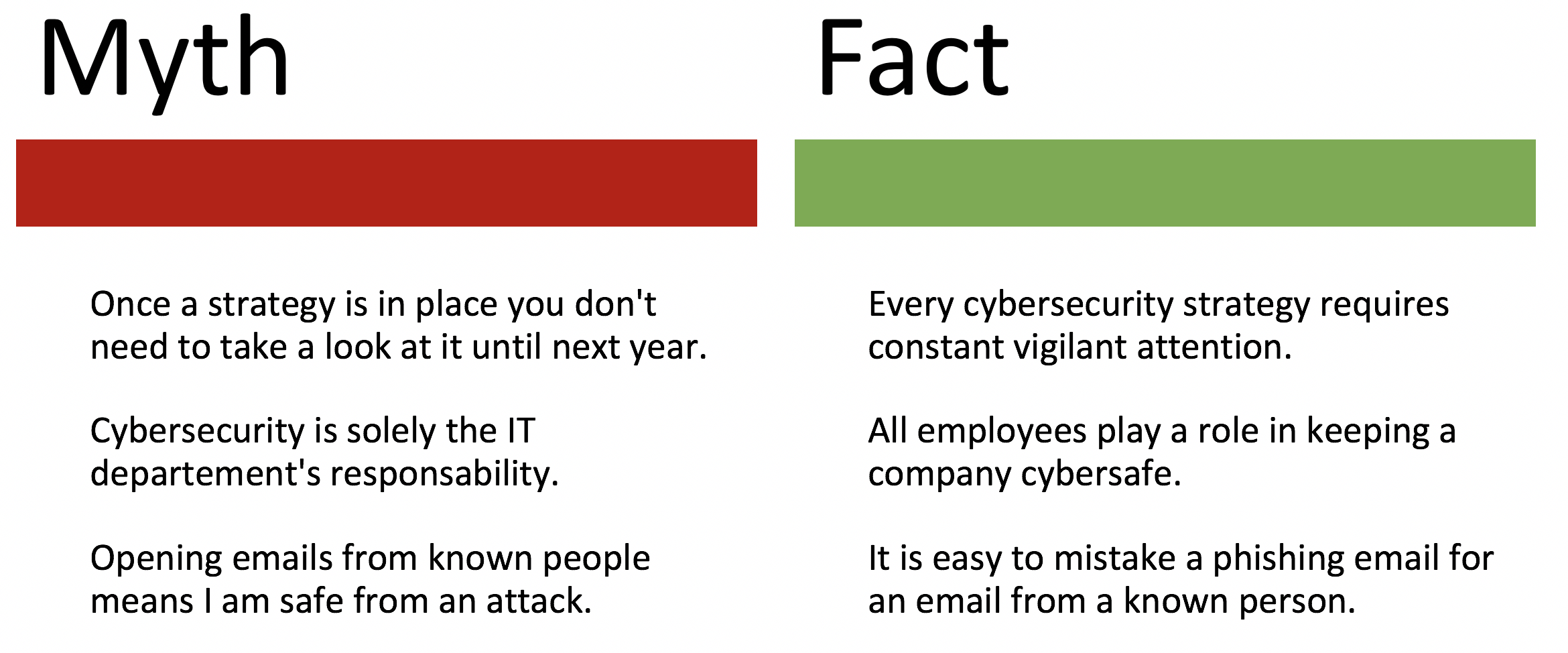

 Data breaches are a constant threat to all organizations. And the risk keeps growing: By 2016, the total number of exposed identities by data violations has increased by 23%, with a record of 100,000 incidents, of which 3,141 were confirmed data breaches. The data now is corrupted/compromised in a few minutes and their exfiltration takes only some days.
Data breaches are a constant threat to all organizations. And the risk keeps growing: By 2016, the total number of exposed identities by data violations has increased by 23%, with a record of 100,000 incidents, of which 3,141 were confirmed data breaches. The data now is corrupted/compromised in a few minutes and their exfiltration takes only some days.