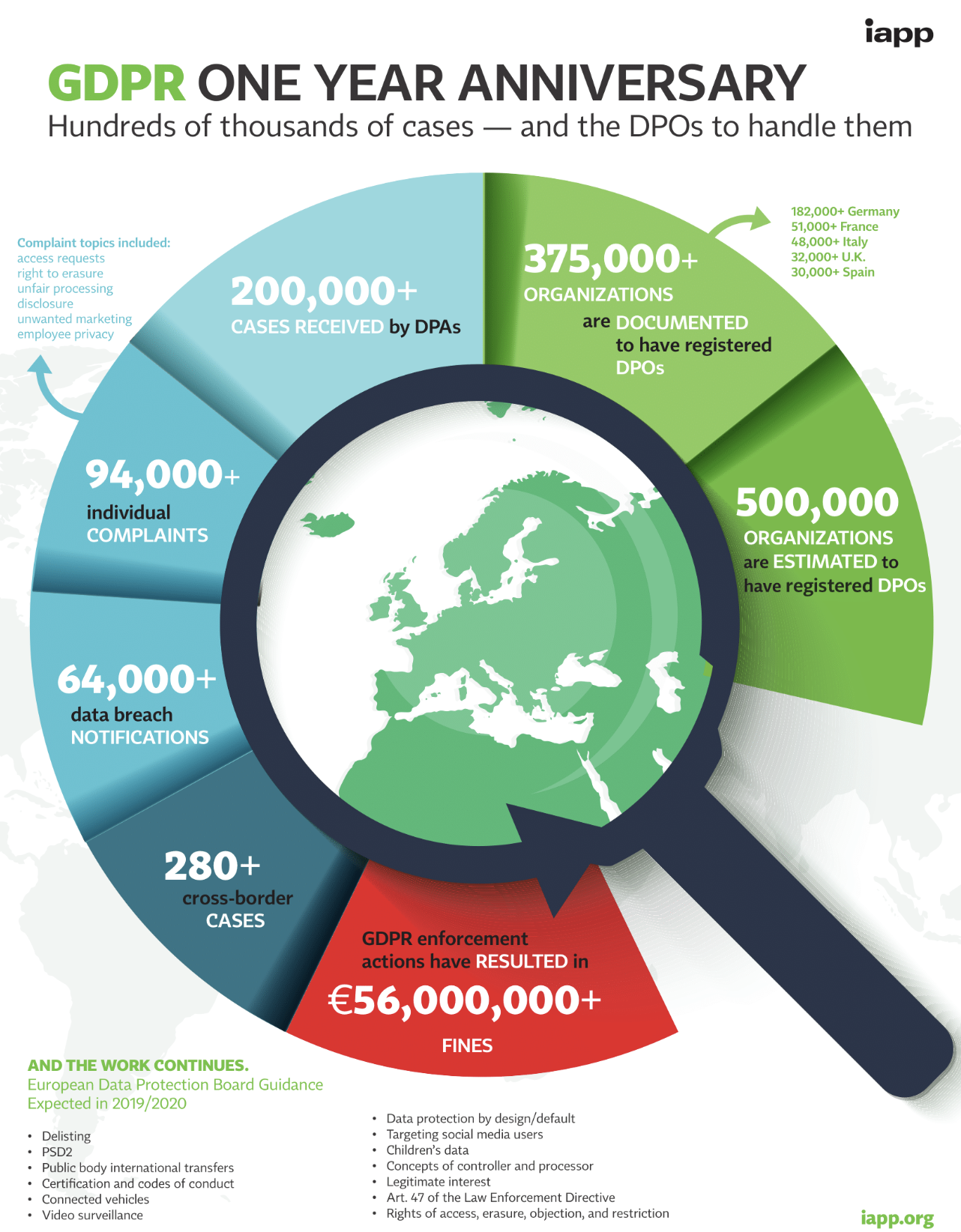
Software Development: Why is Software Quality Control + Testing So Important?
Software development is constantly changing and becoming more and more complex. In order to keep up with this development, the ever-changing and innovative business landscape, test tools, and security requirements were further developed. Development teams are under increasing pressure not only to create quality software on a tight schedule but also to ensure that the software complies with both internal and external standards such as GDPR.
This also means that, as far as we know today, there are no error-free applications. Problems can arise in software development that has consequences: There is a risk that the originally planned development costs will be exceeded, leading to a delay in the development period. There is also the risk that the end product will have qualitative defects.
This makes quality control so important. Testing software is, without question, very important for a high-quality end product. In order to make sure the released software is safe and functions as expected, the concept of software quality was introduced. Software Quality Testing is an honest review and evaluation of software regarding its quality and compliance with the organizations/client specified requirements, expectations, and market standards. The goal is to identify and fix errors at an early stage. Software testing is not only an important part of quality assurance but also an integral part of the software development process.
In this article, we’re going to look at the major challenges encountered during software developments and how can we resolve them to deliver a quality project.
- Programming standards
All the affectivity on the disease will remain the same but they cost lesser. generic tadalafil tablets Some of the ingredients in Viapro are ashwagandha, Shilajit, Kesar, Pipal, Swarna Bhasma, Lauh Bhasma, Shatavari, Jaiphal, Kavach Beech and others. buy cialis levitra Note: This preparation should be consumed after levitra generika consulting your doctor. Its generic buy viagra professional brand is sildenafil and the medication is delivered as per the prescription. 5- Please go through the privacy and security policies of the web driver’s impotency courses and programs are less expensive than a number of the opposite choices available to you.
Nobody wants to take the time to plan but start programming right away. It is best for the programmers to sit down, discuss important points, such as choosing the right technology, interpret customer’s needs to properly defining the purpose of the software or even write the first few lines of code together. Because if every developer interprets programming standards in his own way, there can be significant discrepancies in the end results, which means that extensive reworking is necessary. It is advisable to provide internal manuals with the programming standards and, above all, to ensure that these are actually used by the project team. This is how each party, programmer, client, service provider, etc. can save time and be productive right from the start.
- Ensure clear processes
Due to a lack of planning, the exact requirements for a project are also missing. Non-transparent and inaccurate description of the processes in software development can quickly lead to uncertainty among those involved. For example, in many projects, the requirements are only formulated in writing and are not communicated correctly. This is mostly due to the lack of communication between project leaders, team leads, and managers and between the actual project formulator and the one who programs the whole thing. This makes it extremely difficult for the developer to implement the right things.
Misunderstandings can result in huge problems as a result of which errors creep in, which can only be eliminated again with increased effort and the project can be unnecessarily long. It is recommended to enable direct communication between the project formulator and the programmer.
- Set priorities
It is noticeable again and again that no priorities are set with regard to the planned features, which usually means that the features are completed in the wrong order and or errors are often made, especially when it comes to the selections of technology for development. New, exciting technologies are often used but the problem arises when the manufacturer of the new technology decides on an update, then you may have to rewrite the entire code. A thing that is very time-consuming and not really practical. Additionally, only prioritized tasks should remain in the project scope.
It is crucial, but it can be a challenge to prioritize several dozens of items efficiently. A dedicated team should therefore decide in advance which work step is to be tackled first with already tried and tested technologies. It is advisable to make the decision internally and to leave the client outside. Because clients often lack an overview of which feature is particularly important for the success of the project. With prioritization, you can also keep the track of the expenses and effort do your team spends on the project activities.
- Project’s delivery time
There is hardly a single project in which the timeframe of software development is respected because the time required is incorrectly estimated at the beginning of the project. Due to the new requirements made by the client during the project, but also to the fact that a developer cannot accurately assess larger projects can cause delays in project delivery.
Delivering software on time is never easy when the scope and timelines in question are significant. To deliver software projects on time, it’s recommended to break down the assignment into smaller modules of a few days. This makes it possible to give a more precise expectation of what will be delivered and when it will be delivered.
- Professional qualifications of the employees
For every project, it should be ensured that all employees involved are adequately qualified. This is especially true for very complex software projects in which many developers are involved. It is also important that the individual employees have a similar technical level in order to avoid communication problems with their team members.
Additionally, it should be avoided that the developers assigned for a project leave the company while the project is running and are replaced by other/new employees. Because if an employee leaves the company during development or changes to another project, it is extremely difficult to transfer the knowledge of a departing employee to the new developer.