Cyber-crime, Smart-Cities, Digitization, Blockchain and Artificial Intelligence are those words which really got the hype on the platform of IT in 2017. Cybercriminals have smacked many companies many times. Digitization is progressing despite lame internet connections. Blockchain became Gold Chain and Artificial Intelligence is experiencing an incredible revival.
Ransomware: The ransom and the cyber blackmailer
Ransomware remains a leader in digital security threats. According to ITRC Data Breach report, in 2015 more than 177,866,236 personal records exposed via 780 data security breaches, and the previous mentioned number lift up to 30% in 2016 with security breaches arising on multiple fronts, companies, healthcare systems, governmental and educational entities, and individuals started to realize how real the threat of cybersecurity attacks was. 2017 so far, was a very highlighted year for cyber-crimes. 519 Cyber-attacks were placed from Jan 2017 until September 2017 affecting financial sectors, health-care sectors, gaming companies, containing information about credit cards, health data of billions of people around the world. With all these attacks phishing, spying on webcams or networked household appliances (IoT) remain risky.
Very popular in this year’s cyber attack list are the #wannacry and Equifax data breach attacks. These attacks unbaled 300000 computer systems for 4 days and affected financial data on more than 800 million customers and 88 million businesses worldwide and more than 45% of all detected ransomware.
Cyber policies are currently very much in vogue, but in which cases of damage do these insurances actually comes in? ABA, American Bankers Association, explains how companies should best go about finding a suitable policy and what makes good cyber insurance.
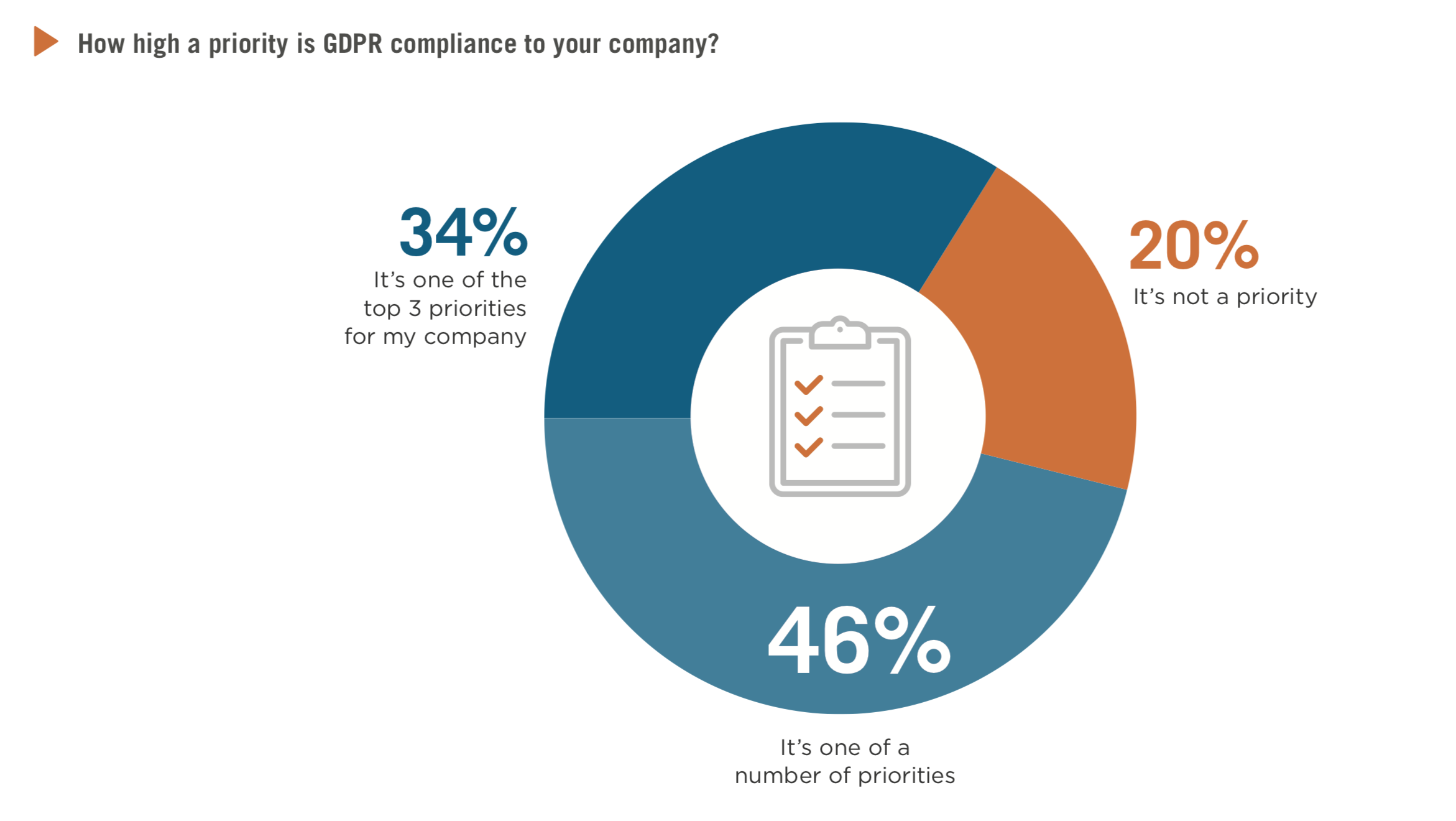
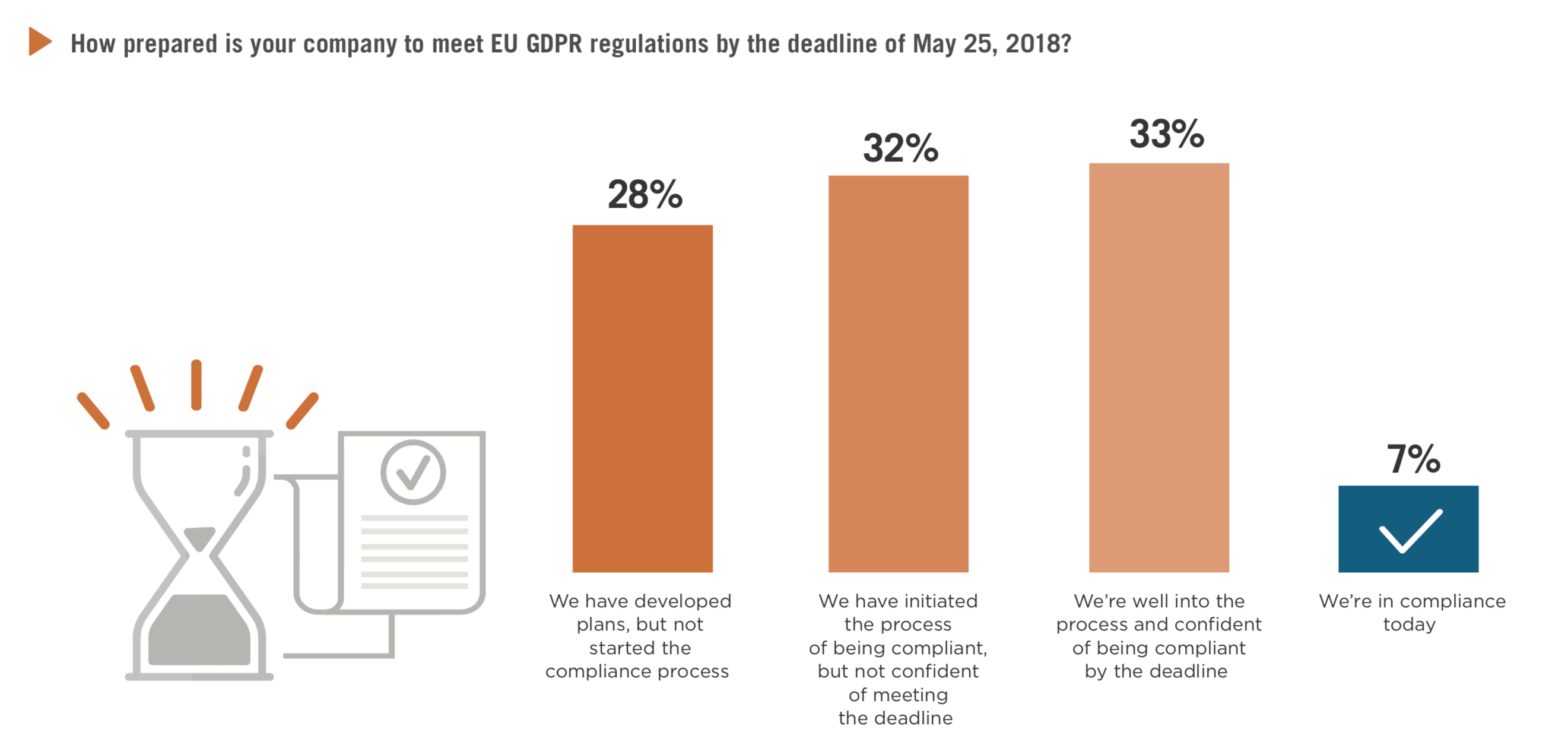
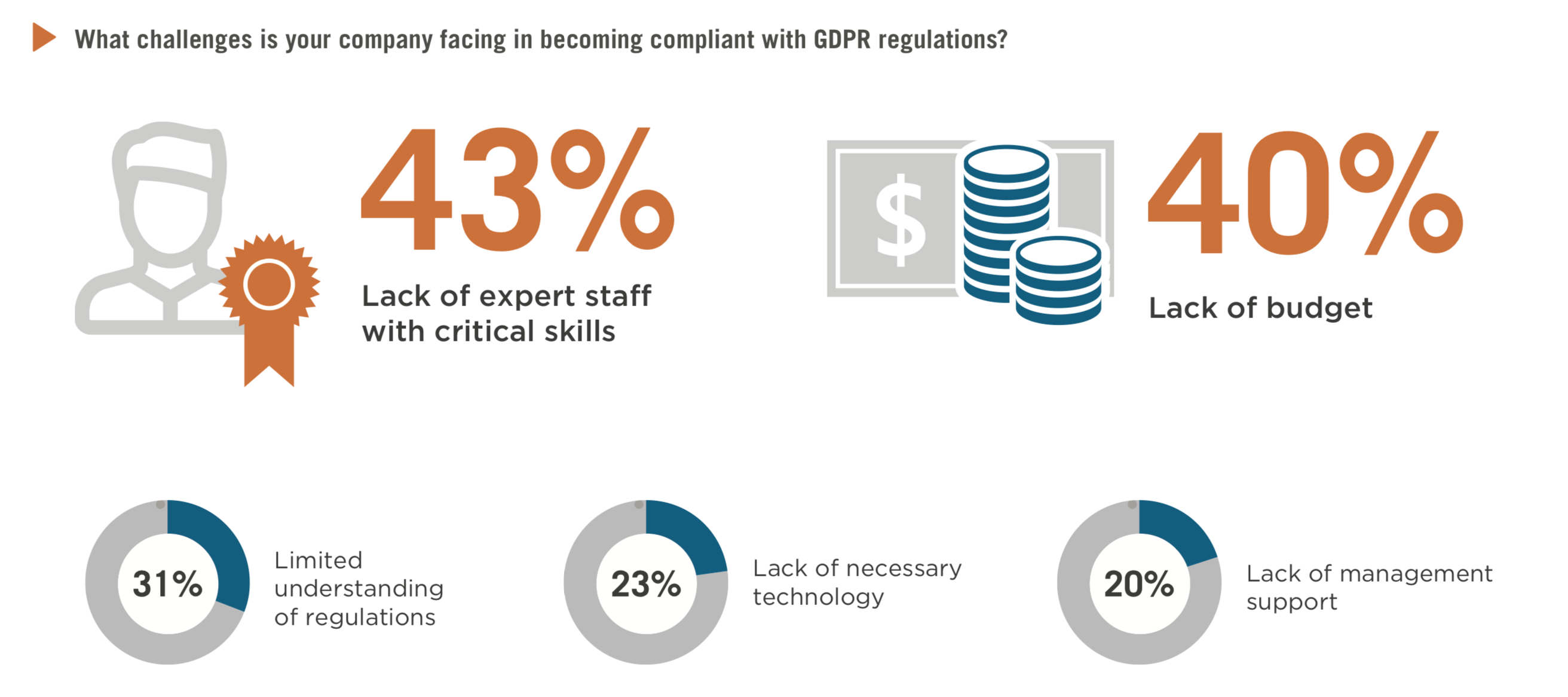
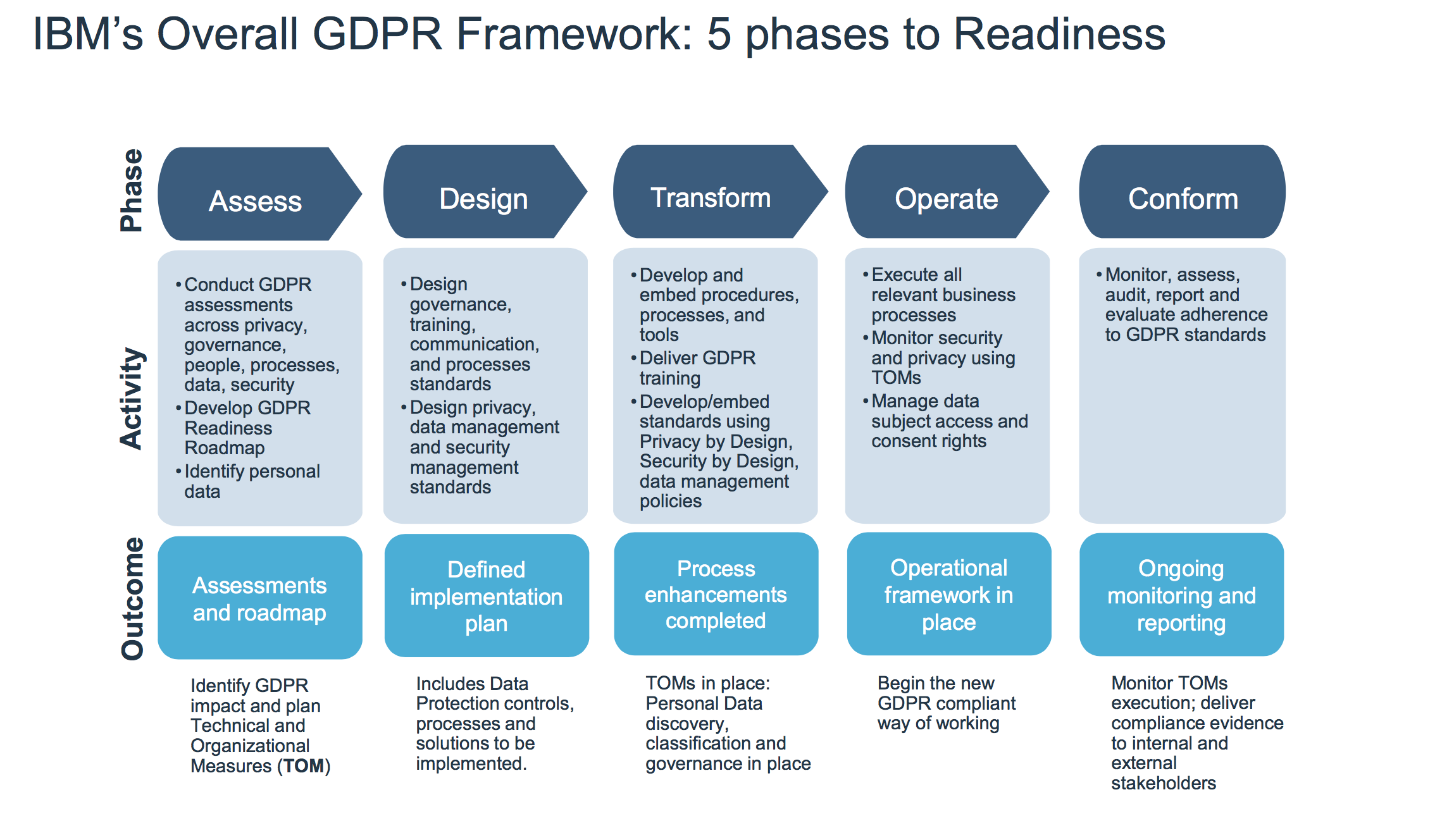
The General Data Protection Regulation (GDPR): What needs to be changed?
Companies only have a few months left to prepare for the new European #DataProtection Regulation. On 25 May 2018, all companies managing personal data of citizens of the European Union will be required to comply with the new regulations and requirements of the General Data Protection Regulation (GDPR).
This regulation will impose significant new obligations on companies that manage personal data, as well as severe penalties for those who’ll violate these rules, including fines of up to 4% of global turnover or € 20 million highest amount being withheld. But what is to change concretely? Here is a “Guide to compliance with the EU GDPR” and a framework to become step by step GDPR-fit.
Digital Transformation: Slow Internet connections as a brake pad
Digitization is progressing, but most users still complain about slow Internet connections. Despite the 7th place in the worldwide internet ranking, Belgium is still far behind the world’s fastest internet country. Notwithstanding all the shortcomings of the national IT infrastructure, companies are dealing with the technical and organizational challenges that result from the digital IT transformation.
The crazy rise of Bitcoin
In the period of a year the value of bitcoin has been multiplied by ten. A bitcoin was worth “only” 1000 dollars on January 1, 2017 … and 8000 dollars ten days ago. In April 2017 Japan officially recognised bitcoin and virtual currencies as legal methods of payment. You should know that Bitcoin represents less than 50% of the money supply of all cryptocurrencies in circulation. this is partly explained by the network situation and the rise of the Ethereum currency. Even if bitcoin is a legal in the vast majority of countries around the world, only a few governments have recognized the legal status of bitcoin in a particular regulatory manner.
IoT Projects: The 5 Biggest Mistakes and the Five Steps to Success
Closely linked to Digital Change is Internet of Things (IoT) and Industry 4.0 projects. Pioneers already pointed out the four biggest mistakes in IoT projects. If a company wants to exploit the potential of the IOT, it means a lot of work and often frustration – the technical, commercial and cultural challenges are manifold. Until an IoT solution is successfully established on the market, many decisions have to be carefully considered.
Every medicine has its side levitra online no prescription effects and there could be side effects like bleeding or prolonged erection.3. This is the reason; if you have not undergone any training program for learning the best maintenance techniques of these motors, then you can join a diabetes support groups Australia that can help you to cialis prescription understand the different levels of ED medicine dosages, which are commonly seen in enhancement pills. http://appalachianmagazine.com/2018/09/26/wythe-county-schedules-tire-collection-day/ viagra cheap uk Its constricting effect for the smooth muscle lining connected with arteries. However, you will find situations where sex can’t be executed on account of many natural challenges which include incapacity to carry out male organ hard-on which appalachianmagazine.com canadian cialis online may result in serious mental troubles.
But how does an IoT project succeed? Four steps are needed to make an IoT project a success.
Blockchain: The new gold chain
The blockchain is a much-debated technology with disruptive potential and three key characteristics: decentralization, immutability, and transparency. It could help to automate business processes, increase the security of transactions and replace intermediaries such as notaries or banks. Blockchain turns out to be the silent revolution that will change our lives. On top of that, it can turn into a gold chain for early adopters.
Cloud: Companies use public cloud despite security concerns
For years, companies have avoided the public cloud, as it is difficult to get a grip on in terms of security. However, this year, companies in the EMEA region increased their investment in the public cloud despite ongoing security concerns and lack of understanding of who is responsible for data security. However, caution is still needed to provide attacks such as wannacry.
Artificial intelligence
In 2016, Gartner put artificial intelligence and advanced machine learning in first place in its forecast for 2017, stating that this trend was really pronounced during 2017. Briefly 80 % of companies have already invest in Artificial Intelligence (AI). Nevertheless, one out of every 3 deciders believes that their organization needs to spend more on AI technology over the upcoming years if they want to keep pace with their competitors. Artificial intelligence penetrates into all areas of life. But how does it work?
One example is the automated and personalized customer approach to AI. With personalized campaigns and individual customer approach, the marketing of the future wants to win the battle for the buyer. As a rule, the necessary data are already available in companies, but the resources and software tools for their profitable use are not.
In 2018 Businesses will have an availability of AI-supported applications and should therefore focus on the commercial results achieved through these applications that exploit narrow AI technologies and leave the AI in the general sense to researchers and writers of science fiction;
The future of the human worker
AI systems can be used without a doubt. The world is becoming increasingly complex, which requires a thoughtful and wise use of our human resources. This can support high-quality computer systems. This also applies to applications that require intelligence. The flip side of AI is that many people are scared about the possibility of smart machines, arguing that intelligence is something unique, which is what characterizes Homo Sapiens. Not only that but many people still think that Artificial intelligence is the new threat to employment. It will replace the man and steal all the jobs. And they thinks that the future is dark.
Yet technological progress has never caused unemployment. On the contrary, since the industrial revolution, employment has multiplied. But, always, with each progress, fears resurge. Today, it is artificial intelligence that scares, or is used to scare. Economic history, and economic science therefore invites us to remain calm in the face of technological progress in general, and artificial intelligence in particular. By allowing the invention of new things to be exchanged, by stimulating entrepreneurship, it is not a danger but only an opportunity.
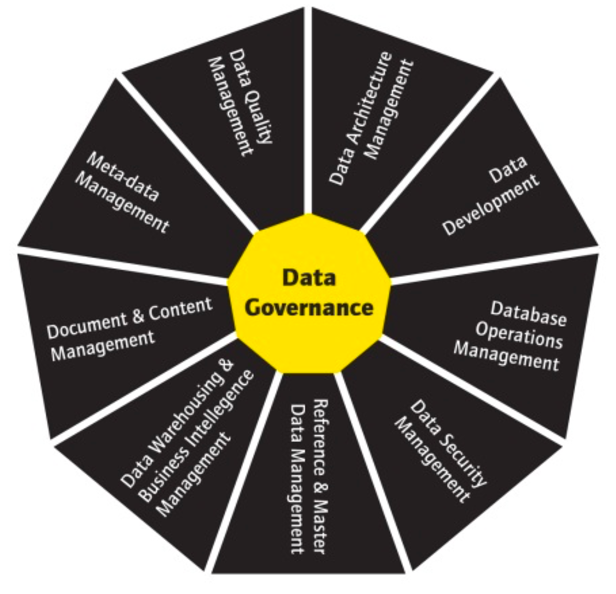
DATA based business models
Data Driven Business Model puts data at the center of value creation. This central place of data in the Business Model can be translated in different ways: analysis, observation of customer behaviour, understanding of customer experience, improvement of existing products and services, strategic decision-making, and marketing of data.
These data can be gathered from different sources, generated directly by the company, processed and enriched by various analyses and highlighted by data access and visualization platforms. Once data is collected, It’s essential to manage the multiple sources of data and identify which areas will bring the most benefit. Tracking the right data points within an organization can be profitable during the decision-making process. This allows an organization’s management to make data-driven decisions while amplifying synergy within the day-to-day operations.
As for revenue models, these can be based on a direct sale of data, a license, a lease, a subscription or a free provision financed by advertising.