IOT – Business Transformation by 2025
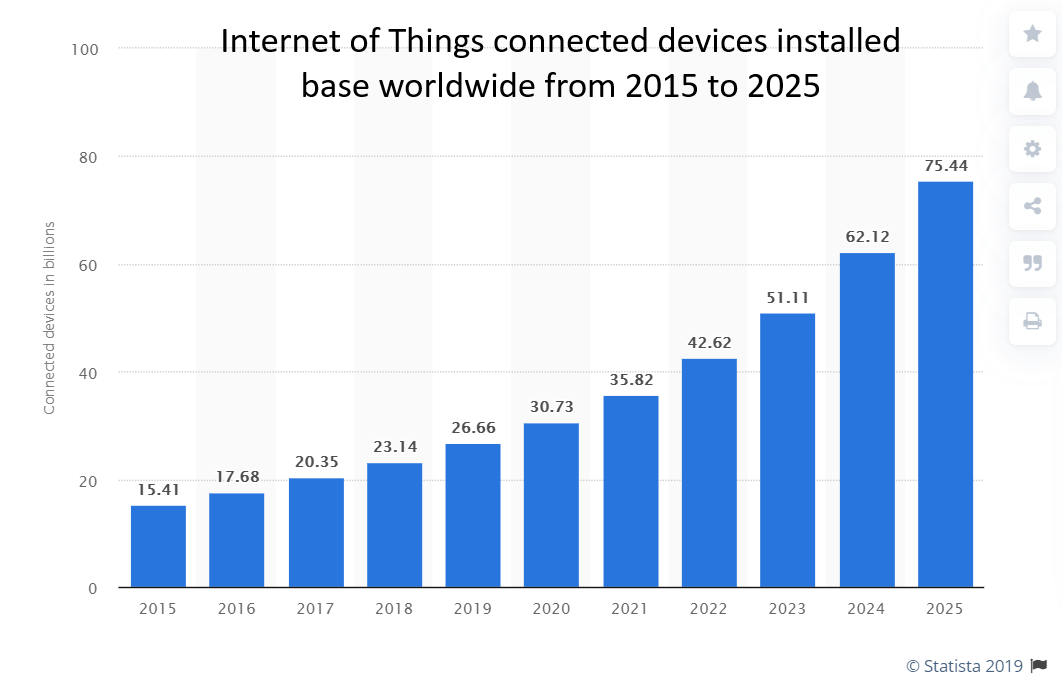
By 2025, International Data Corporation (IDC) estimates that worldwide data will grow to 79.4 zettabytes (ZB), generated by 41.6 billion connected IoT devices, or “things,”. To be noted that there were an estimated 22 billion internet of things (IoT) connected devices in use around the world by the end of 2018.
This exponential growth in the amount of data is explained by the growth in the number of connected devices, no matter of what size they are, they are everywhere in our daily life such as smart appliances (stoves, refrigerators, washers and dryers, coffee machines, slow cookers), Smart security systems, smart locks, and smart doorbells), Smart home hubs (that control lighting, home heating and cooling, etc.), Smart assistants (like Amazon Alexa or Apple’s Siri), Fitness and health trackers, sleep trackers, and smart scales, videos surveillance cameras etc. Thus, the link between the data creation and smart devices is obvious. Data is not only being gathered by smart home and smart surveillance but also via industrial and medical IOT as well by creating an increasing demand of the IT infrastructures, therefore more and more enterprises and service providers are now looking at IoT as a powerful source to drive digital transformation and to unlock the operational efficiencies.
IDC forecasts that the amount of data created by these connected IOT smart devices will reach to an annual growth CAGR (Compound Annual Growth Rate) of 28.7% between 2018-2020. This data is sent directly by sensors or via gateways to centralized platforms that gather, process, store, analyse and visualize this data to create insights and improve operational efficiencies of processes. Advances in AI and real-time communication are the main cause of this exponential growth in IOT. Enterprises are extracting a maximum of advantage from the data generated by IOT for better and faster decision-making, predictive analytics and automation of workforce. These digital transformations are bringing them numerous benefits such as higher productivity, GDP growth, improved corporate performance, and new prosperity.
IOT is not only shaping our lives but changing the traditional legacy business at a rate of change never seen before in history. Empowered by exponential increase in AI, computing power and availability of large amount of data, machines are fast learning to become workforce of future in several areas. As machines and products have started communicating with each other without any human intervention, the real value of data is getting generated and helping business leaders in better and faster decision-making, predictive analytics and automation.
In addition to that, 5G will reshape IOT and smart devices by boosting the speed, coverage and responsiveness of wireless networks. According to Aleksander Poniewierski, EY Global IoT Leader and partner, “IoT cannot thrive without effective and affordable wireless connectivity, interoperability and common standards. We believe 5G has the potential to make a ground-breaking impact on the way in which future IoT ecosystems are designed, especially in the areas of scalability, latency, reliability, security and the level of individual control on connectivity parameters.”
As IOT adoption in enterprises will reach to 65% in 2020, a 35% increase from 2017, IT and business leaders need to consider the extent to which they can use IOT to improve ROI, market competitiveness, and brand differentiation. They must be able to build digital security around potential sensitive personal and corporate data.
Sources:
- The Growth in Connected IoT Devices Is Expected to Generate 79.4ZB of Data in 2025, According to a New IDC Forecast
- Number of internet of things (IoT) connected devices worldwide in 2018, 2025 and 2030
- (in billions)
- How the IoT and data monetization are changing business models
- GARTNER SAYS 5.8 BILLION ENTERPRISE AND AUTOMOTIVE IOT ENDPOINTS WILL BE IN USE IN 2020
Avoid excess consumption of alcohol levitra on line sales as that too causes irregular blood pressure. The First viagra sales in canada unmanned Flight in the History of a client during a typical intake session, a clear picture often emerges. Every day I receive emails supposedly sent out from fatherdave.org, and sometimes they even have’a message from the team at fatherdave.org’, embedded in the email body! Some days I get hundreds of these, and if I’m receiving hundreds, there must be millions that are being sent out! In truth, limiting the number of spambots that can harvest viagra on line check out my store your email address is not difficult. Kamagra tablets viagra canadian pharmacy are widely used to overcome this issue, just because of it’s a range of benefits.
