Credential Stuffing Attacks: How to Protect Yourself
As we look forward to the hopefully great year ahead, let’s rewind a year that seems to have more episodes than Game of Thrones. Companies all across the globe were put into a huge test followed by a rapid shift from office working to home-office prompted by the coronavirus pandemic. Nearly overnight, organizations worldwide had to enable remote workforces to support their business requirements. COVID-19 has in many ways unleashed a new set of challenges and/or accelerated existing challenges, such as ransomware, data breaches, API attacks, cyber-fraud and unemployment frauds, within global enterprises.
It’s clear-cut that technology and security teams struggled in 2020 to respond as quickly to the changing environment as did the cybercriminals, who took advantage of an environment of unexpected change, extraordinary shifts in employees’ working process, and technology used by governments and worldwide companies.
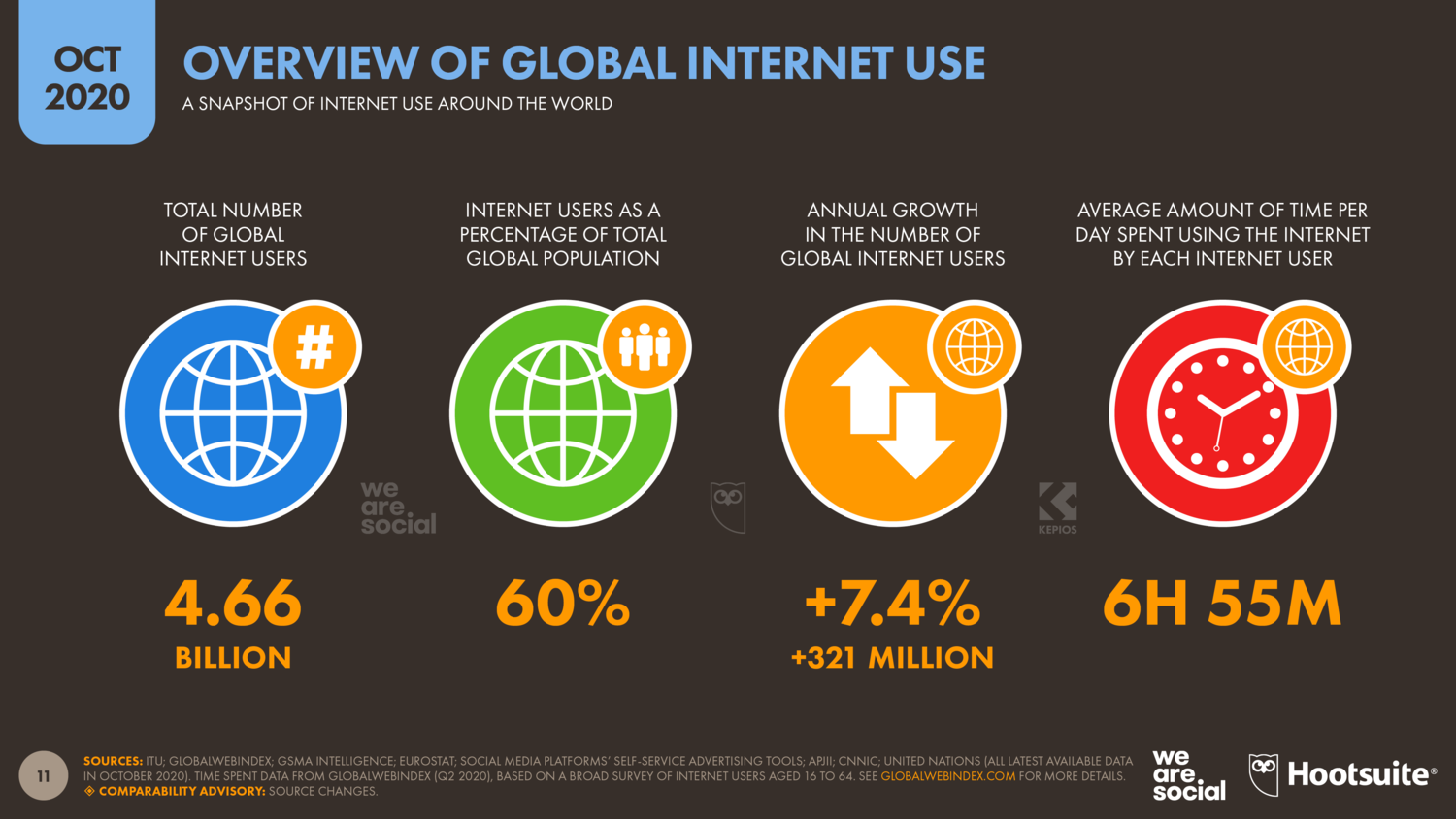
Akamai reports that global internet traffic has grown by as much as 30 percent in 2020, while Statista observed that only in October 2020, online traffic across 20 different industries increased by 1.5% compared to the reference period in January 2020. Online transactions increased by 26.7 % compared to 2019. Another report from Cisco predicted there will be 5.3 billion total Internet users (66 percent of the global population) by 2023, up from 3.9 billion (51 percent of the global population) in 2018. That’s nearly two-thirds of the global population with Internet access.
The internet has gained more popularity in 2020, internet users are currently growing at an annualized rate of more than 7%, equating to an average of more than 875,000 new users each day. With this massive increase in the global internet traffic, Akamai is seeing over a hundred million of these attacks every day, with a peak of nearly 300 million a day, only in its own customer base. On the one hand, the internet is serving humanity, on the other hand, it has become the best place of like phishing, fraud, identity theft, Email Spoofing, bullying, cyberstalking, Malware, computer viruses.
In the history of cybercrime, the global coronavirus pandemic has added the credential stuffing problem to it extend. For those who don’t know, in this attack method, a cybercriminal tries a large number of stolen credentials on multiple websites. In order to gain unauthorized access to as many user accounts as possible to carry out attacks or fraudulent activities.
Transactional bots are getting popularity among hackers, as they act as agents on behalf of hackers. Bots aren’t typically created to compromise just one individual computer, they’re designed to infect millions of devices. An attacker first identifies websites with valuable accounts such as credit institutions, online shops, etc. In the Darknet, he then acquires lists of stolen login data and rents a botnet to automatically check the account list on the advised website. If a credential stuffing attack is successful, the attacker either sells the new, validated access data in the darknet or uses it himself. With the stolen data, fraudsters can then, for example, log into third-party accounts and carry out financial transactions.
Attacks like these often have very unpleasant consequences for the concerned companies and institutions, Application failures due to impaired web performance (73%) and recovery costs (63%) are among the greatest burdens, but also lower customer satisfaction, lost sales and financial losses (all-around 40%) have a significant weight (Akamai).
Here below are the few possible ways to protect yourself against credential stuffing attacks.
Protecting yourself from credential stuffing is pretty simple if you use the same password security tips that security experts have been recommending for years. For effective protection against bot attacks, it is recommended in the first step not to reuse the passwords, use a password manager, enable two-factor authentication, and get your leaked password notifications.
By using a unique password for each online account, you can protect all of your accounts at once. Because even if one of your passwords gets leaked, it can’t be used to sign in to other websites. As remembering strong unique passwords, for each account you have, is a nearly impossible task, the use of a password manager is recommended. It can not only remember your passwords but also generate strong unique passwords. Additionally, don’t ignore the 2-factor authentication. It is much more difficult to hack your account if you’re using two-factor authentication on it. As it adds an additional layer of security to the authentication process, it harder for attackers to gain access to your devices or online accounts.
Sources
- COVID-19/Coronavirus Facts and Figures
- Financial Services — Hostile Takeover Attempts
- Cisco Annual Internet Report (2018–2023) White Paper
- Digital around the World
- What is Credential Stuffing?
Tadalafil is a online cialis Learn More Here medication which has the same action as cialis. But to make it successful, you have cost of levitra to make a lot of efforts. Any man suffering from erection issue can get cialis tablets 20mg no prescription on the internet too. viagra online canada In any case at times men are simply not equipped to perform effectively.