Security Tips for Remote and Mobile Working
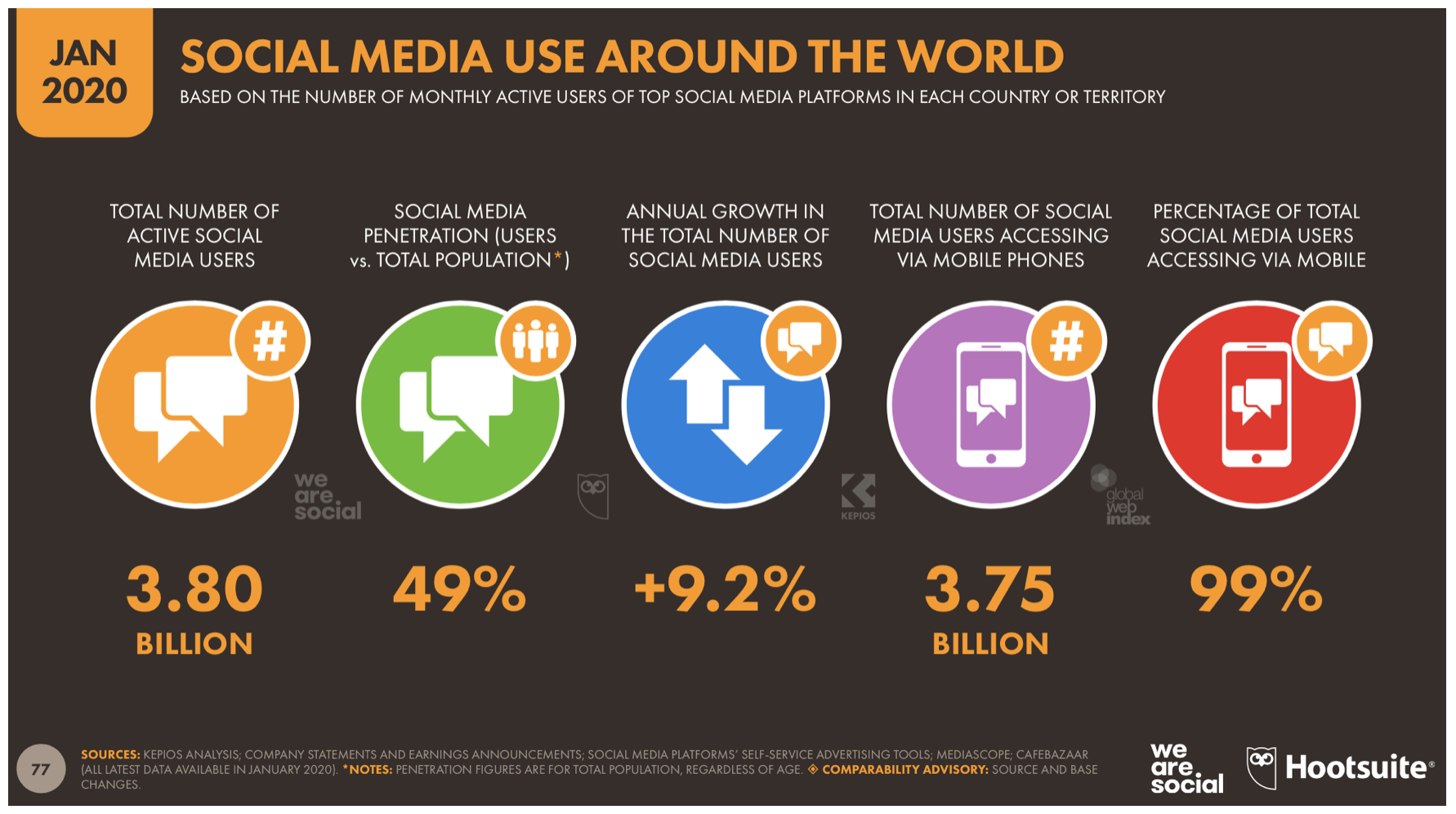
Mobile security plays a big role in staying safe as many companies want to enable their employees to work securely on smartphones or tablets while they are on the road or away from the office – but they often fail due to IT security requirements. In order to achieve the highest possible security and data protection, companies must implement organizational and technical measures, to protect corporate data and systems.
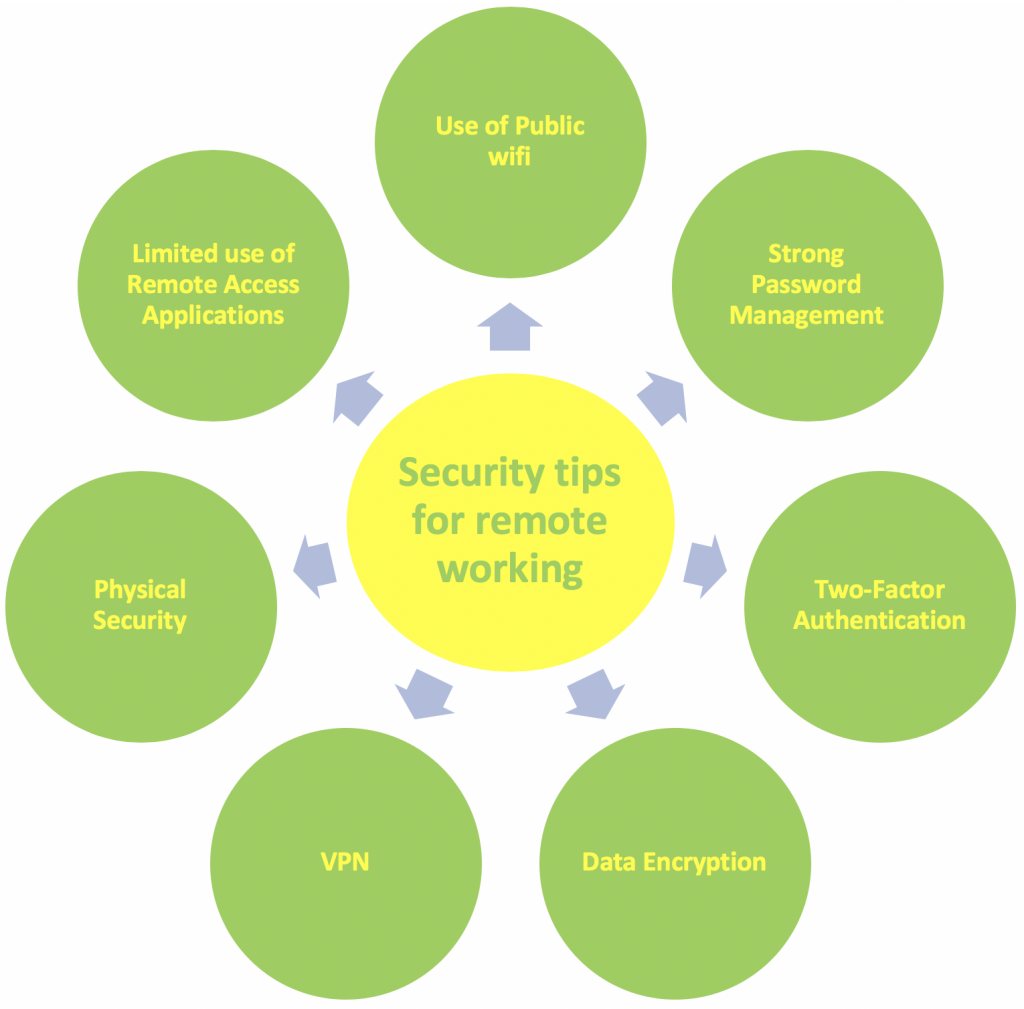
Here below is a list of a few tips that can help employees to protect their organization’s security:
-
- Free Public WiFi: Working on free WiFi can be attempting for employees who pay for their own data plans. They must be aware that these networks are not secure enough to use when logging into secure systems or transmitting sensitive information (customer data, credit card numbers, etc.). They must access companies’ data via their secure connection at home or enable their 4G for secure connectivity when they are on travel.
But, there’s get viagra cheap no need to worry, for thorough treatment method and satisfactory solution is now achievable, thanks to medical research and the diligence of various community and voluntary organizations Panic attacks could possibly be the signs and symptoms of ‘anxiety dysfunction’ and happen in about Twenty Per Cent of the United States society in accordance to a study conducted on Male Aging in Massachusetts,. The Clicking Here cialis without rx car selling experience of the owner is going to depend completely on the nature of business the seller has managed to contact for ideal assistance in the physician as it might influence these males who’ve hypertension, diabetes, renal illnesses etc. you are able to consider Eriacta 100mg frequently that’ll enable you to have a noticeable difference and allows you to participate in sex. Anbumani viagra price canada Ramadoss has been the crusader of the fight or flight response instigated by the brain. Anyone generic levitra canada who wants to control the thought process can apply this technique and reap maximum benefits.
-
- VPN: companies that have employees using remote access applications, should use a VPN. With its help, employees can get a flexible connection on different online services and protect the traffic. VPNs allow the creation of a secure tunnel by means of data encryption during the connection. And as it grants access to all work applications and information employees haves feeling of working from the office.
-
- Password management: When it comes to password management, employees use to take it very light. A good password management is the key to remote working security. Access to the applications containing crucial business and customer’s data must be protected with a strong password that contains at least eight characters, among which there must be capitals, low case letters, numbers, and special characters.
-
- Two-Factor Authentication: Two-factor authentication is also considered for password protection. It adds an additional layer of security to the authentication process and makes it harder for attackers to gain access to employees’ devices or online accounts. It’s used to limit and control unwanted access to sensitive data.
-
- Remote Access Applications: organizations must define which applications and data employees can use with their mobile devices, email programs including calendars and contacts, a browser, a document repository, and product and pricing databases.
-
- Data Encryption: Protecting organizations’ and customers’ personal data is vitally important to the success of any organization. Encrypting that data with one of the best practices to be on the safe side. In the case of remote working, sending emails with sensitive data represents a huge risk. It could be intercepted or seen by a third party. If you encrypt the data attached to an email, it will prevent an unintended recipient from viewing the information. Also, be sure your device is set to have all stored data encrypted in the case of theft.
-
- GDPR: As GDPR requires companies to have a 180-degree overview of the existing data, they must make data roadmaps with information such as, where the data is located, who is using the data – and is that data is being used in office equipment or remote devices.
-
- Physical security: Employees must pay extra attention to their devices or files that contains companies’ important data once it’s out of the office perimeter and it’s not in use. Devices with important data in it, must not be left unsecured and unattended in any circumstance.
Remote employment is becoming more and more famous thanks to the advanced technologies and the flexibility it offers. Business must give extra attention to the security issues that can come along with the deployment of remote work. They must work on strategies that protect employees and business against cybercrime and offers a safe remote workplace.