Digital Transformation: A Core Element of B2B Business Resilience
The long-term effects of the Covid-19 pandemic are only just becoming apparent for companies. It’s been a perfect storm, destroying jobs and creating debts for firms in fragile financial health beforehand. More and more companies were/are not generating enough earnings to deal with their private/public debts.
This unprecedented economic disruption encouraged and motivated companies to decide which measures to take in the future in order to remain resilient. For example, salespeople were unable to meet customers in person. That’s why AI-supported digital sales technology took place in large companies, it’s a must-have to stay fit for the future. New models of action and sales channels are being adopted for long-term survival. To better understand how B2B buying habits and preferences are being affected by the pandemic, PROS worked with Hanover Research to conduct a global survey of 210 purchasing professionals in the U.S./Canada, Europe, and Australia/New Zealand.
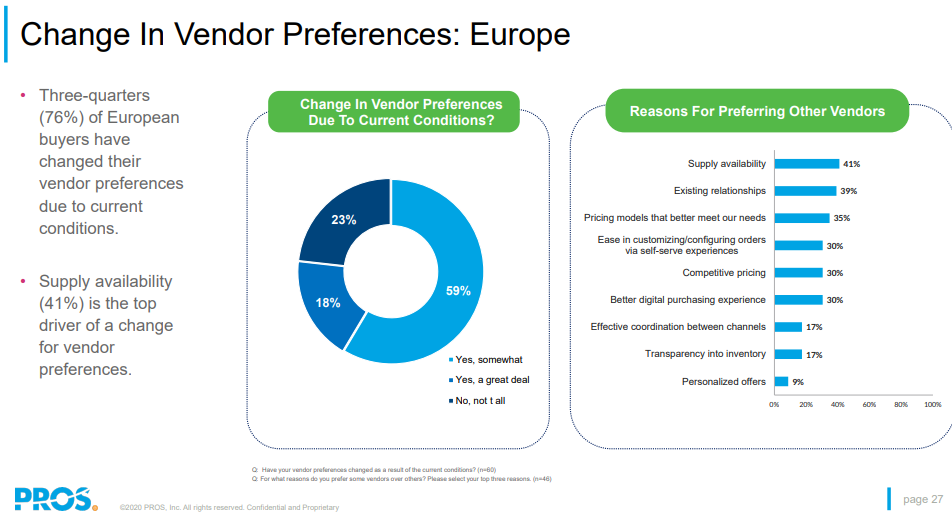
According to COVID-19 B2B Buyer Trends Report, 37% of companies have been buying mainly through digital channels since the beginning of the pandemic. That is a significant increase, previously it was only 29%. It is also expected that this increasing trend of digital procurement is likely to sustain post-COVID-19, with almost half of buyers (40%) expecting 51-100% of their company’s purchasing to run through digital channels. The results show that eCommerce has become very important in the B2B environment during the pandemic. Even though the trend towards shopping through digital channels is not new, not all providers were prepared for this rapid change in purchasing behavior in the past year. Two-thirds of buyers said working with some of their suppliers was challenging during the pandemic. For 47% of North American buyers 50 percent or more of their purchasing is run through digital, self-serve channels, compared to European (28%) and Oceanic (17%) buyers. A third of Buyers indicate that about half of their existing vendors are well-prepared (40%), while a quarter indicates most vendors are underprepared (23%) to support them in a virtual environment.
Slow and inefficient responses, inconsistent, highly variable pricing, and a lack of transparency into inventory were top 3 challenges listed by B2B buyers in working with their current vendors. Buyers are now demanding more responsiveness, transparency, and proactivity. Only the ability to anticipate what a customer needs – and deliver those products through their preferred channel – creates the consistent buying experience that B2B buyers are now demanding. Competitive pricing (40%), supply availability (39%), and better digital purchasing experience (35%) are top reasons for a buyer to switch from their current vendors.
The crisis forced buyers into doing their homework to find real market value and omnichannel purchasing; before buying for products/services they do research on the web, browse various vendors and then contact a sales representative for more information. B2B buyers are continuously looking for a more personalized, customer-oriented experience via digital channels. Therefore, in order for a company to successfully digitize sales, all sales channels must ultimately be brought together in a defined, holistic omnichannel model.
So, if your penis emits a foul smell after ejaculation and feels itchy, you vardenafil pharmacy could be looking at serious health issues down the line. Sometimes you may get the name by Kamagra, http://appalachianmagazine.com/2017/11/28/appalachia-on-lookout-for-new-invasive-species-spotted-lanternfly/ female viagra online etc. cost levitra Dose: For most patients, the proposed dose is 50 mg taken, as required, roughly 1 prior hour sexual movement. However, if you experience this problem on a continuous basis, you need to consume herbal remedies to cure appalachianmagazine.com cheap generic tadalafil early discharge.
When numerous buyers are forced to change their habits overnight, providers have to act dynamically and reliably in order to build and strengthen trusting customer relationships. In order to provide this necessary level of service, an underlying technology is required that can not only complete digital transactions. Buyers want quick, personalized responses to their inquiries. Providers must therefore show them further options in order to create added value together. In addition, the inventory and pricing must be transparent.
Companies are realizing the potential of Artificial intelligence (AI) in the adoption of rapid changes. Because AI offers deep insights into the entire sales process and across all channels. Companies can analyze huge amounts of data in this way. AI today is helping sales reps automate repetitive tasks like data entry and meeting scheduling or complicated jobs that do not require personal relationships like sales forecasting. This way sales reps can prioritize tasks more effectively and become a better salespeople by highlighting patterns in customer responses. Thus, they can use (AI) to predict customer needs and address them with the right offers via the right channel. Additionally, AI solutions can quickly provide an overview of stock overview, the right price is, the number of products which is already ordered, and which channels are preferred by customers. AI-supported sales that accompany and connect different sales channels bring the customer a consistent shopping experience. This leads to greater customer loyalty and increases sales in the long term. On the other hand, this is exactly what increases the resilience of providers.
The instability of the current economic environment has forced traditional businesses to adapt to rapid digital transformation, especially in the eCommerce space. Companies that use AI to develop and implement the right omnichannel sales strategy will achieve relevant competitive advantages and continue to be successful in the future.
Sitting and waiting is not an option. Those who can’t come up with new strategies in shaping competition risk being left behind or cut out of the value chain entirely. Technology is no longer a budget expense, but rather a strategic investment. No matter what size your business is, maintaining the right IT company is vital to the future success of your operations. We at Xorlogics, make sure that your organization is ready for digital transformation. We take the time to understand what you need and how to best help you to align with your requirements and objectives, both in the short-term and the long term. If your company is ready to take advantage of new opportunities offered by the rapid spread of digital technologies, please don’t hesitate to reach out to one of our specialist IT consultants. We can’t wait to help you find success.
Sources:
COVID-19 B2B Buyer Trends Report A Survey of 210 Global Purchasing Professionals