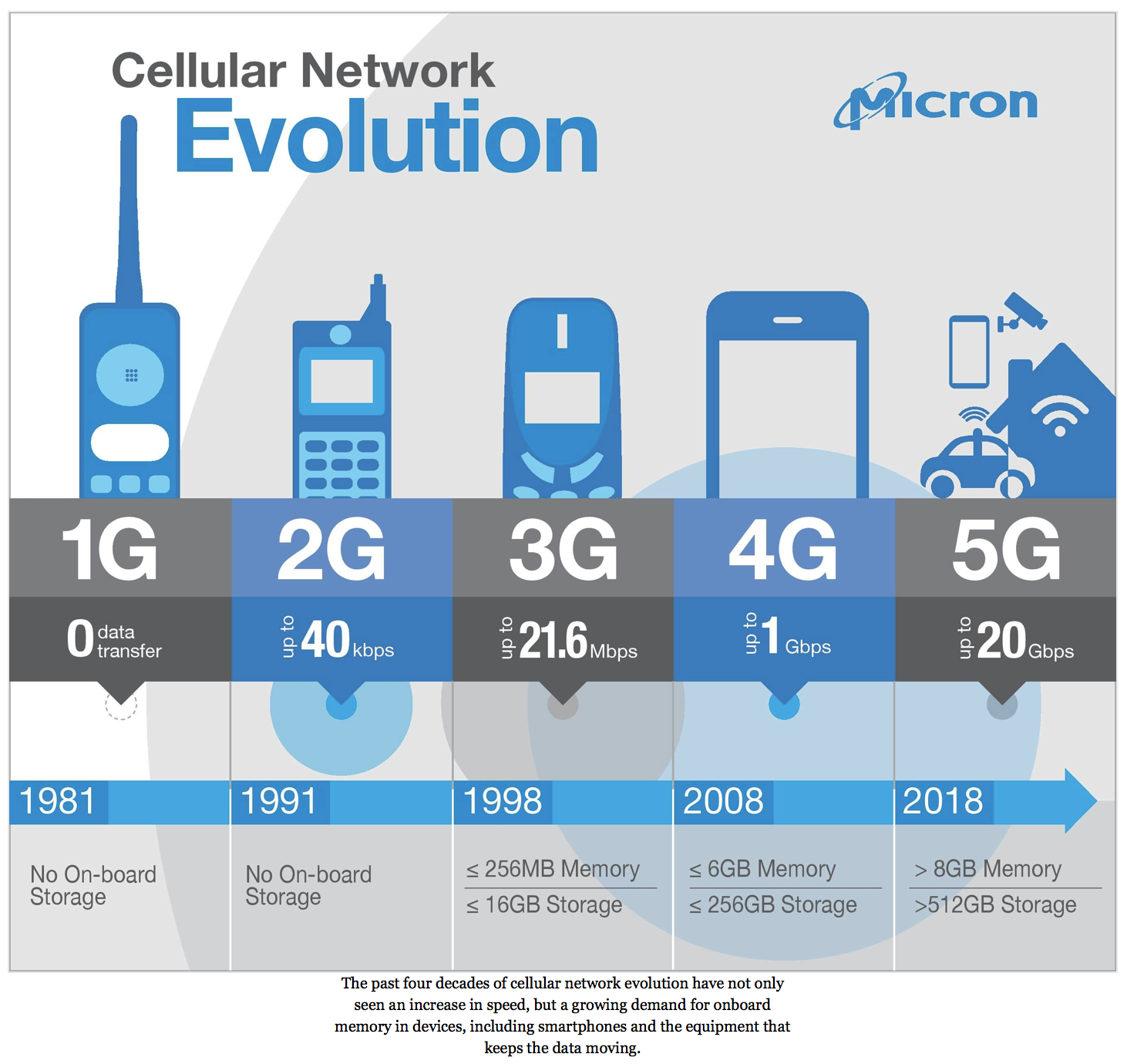
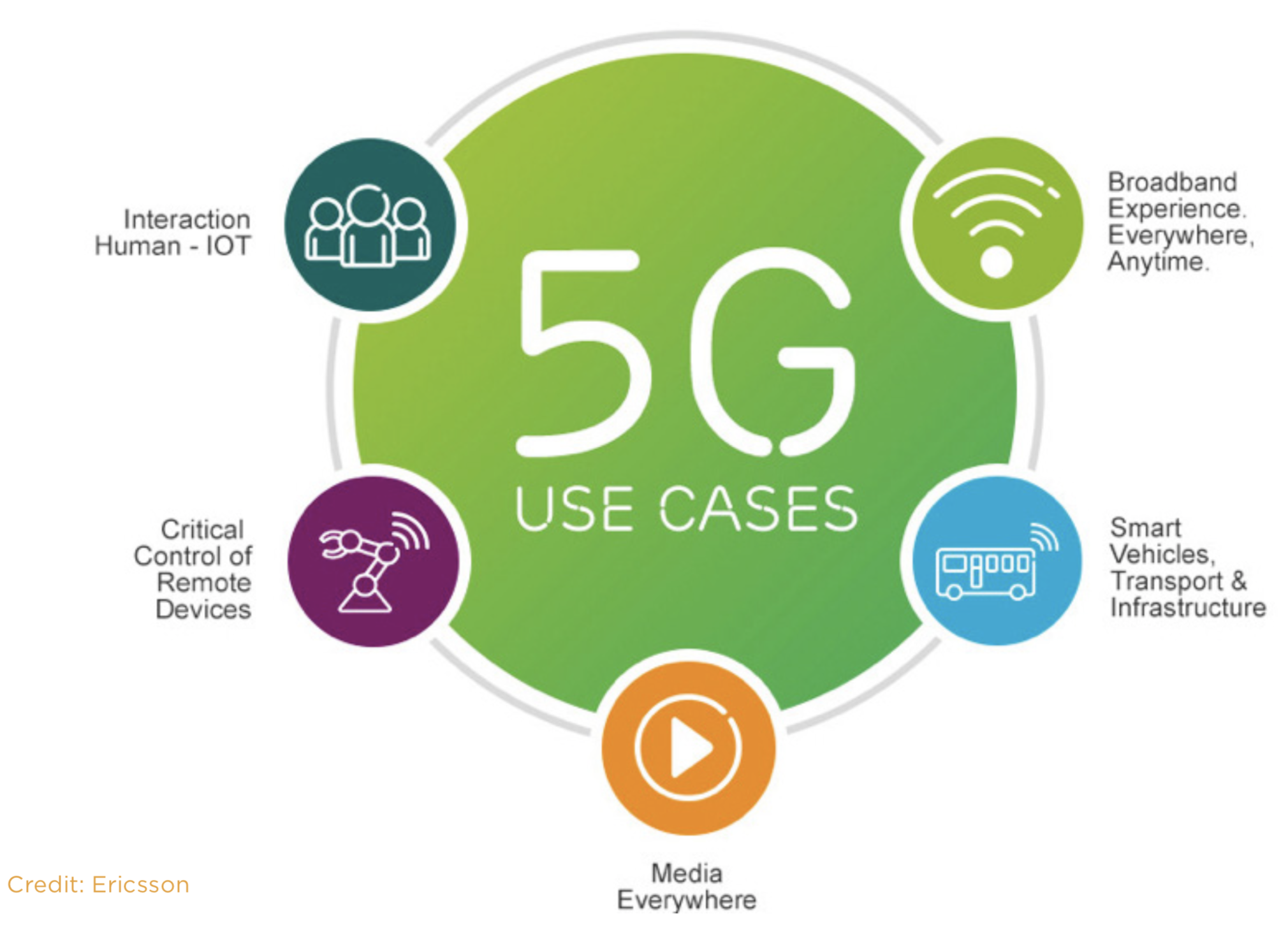
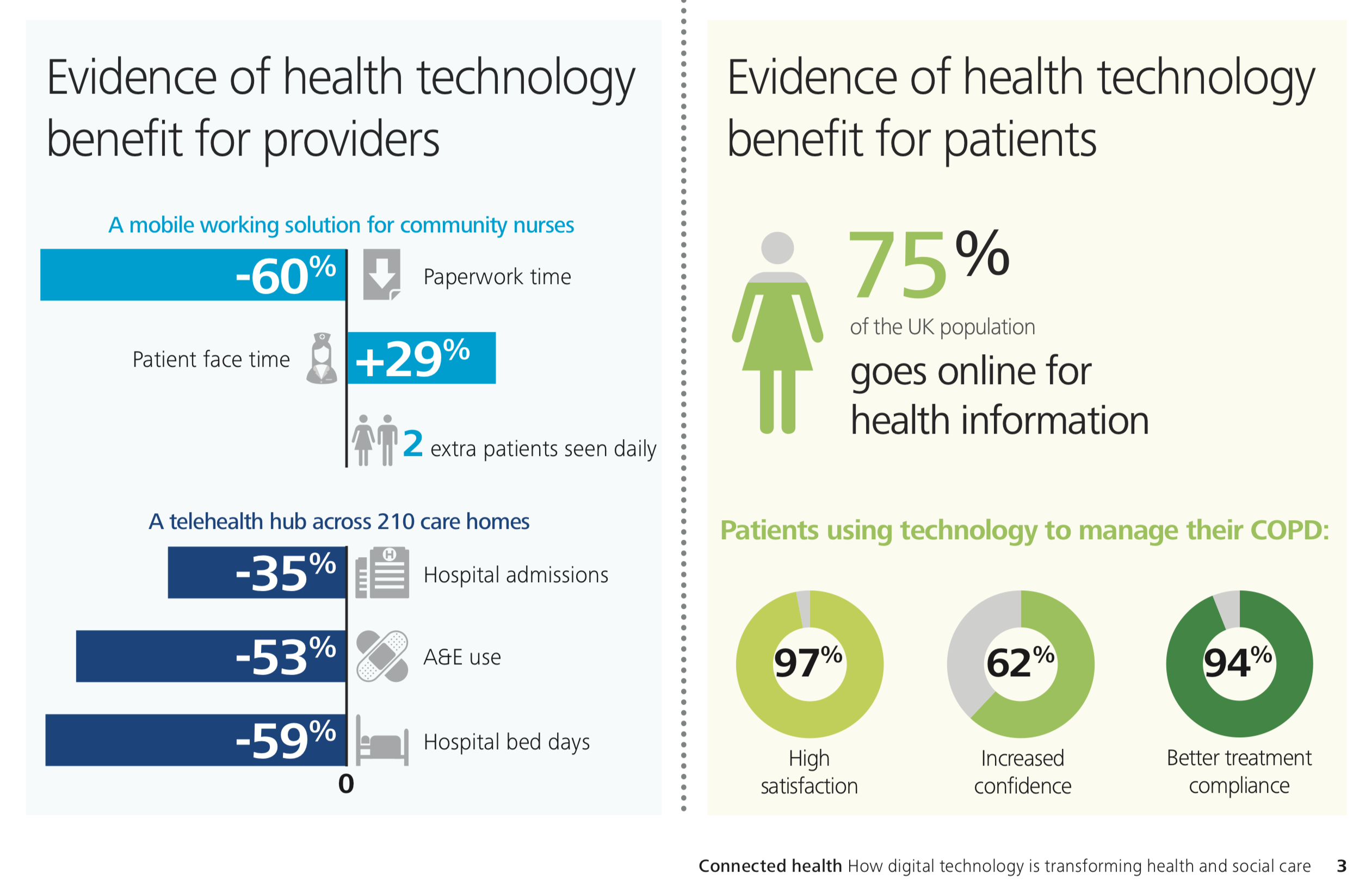
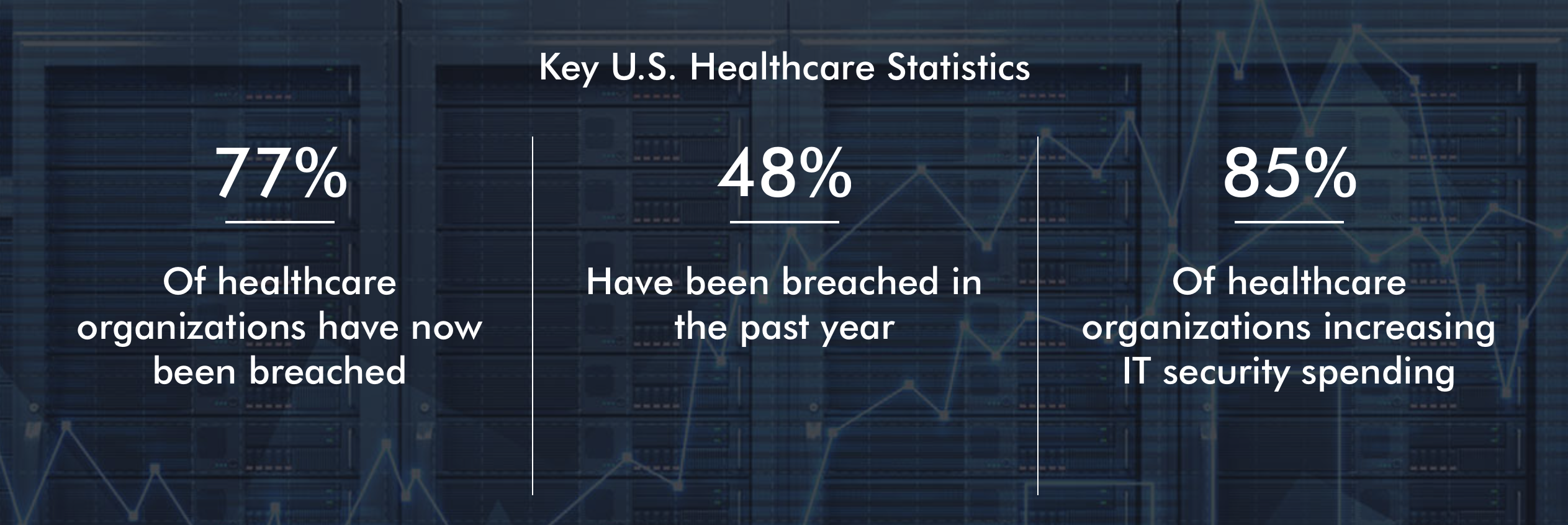
It is well known that the fourth industrial revolution opens up a multitude of new business opportunities. At the same time, however, the danger for cyber-attacks is also increasing. It’s imperative that companies prepare themselves to put them out of danger zone.
Not only should they think about security solutions directly when planning IT technology, but they should also develop a keen awareness of the corporate culture for security – which requires significant investment. According to Gartner’s estimations, security spending in 2018 will continue to rise sharply globally, reaching around $ 93 billion. For the coming year, this means that Cyber Security will capture some of the key trends.
IT security experts are still in demand
As technology evolves, security expertise needs to adapt to changing needs. The challenge is to train cyber security specialists to acquire and develop the skills in order to become companies “superheros”. Cyber Security Ventures Report predicts there will be 3.5 million cybersecurity job openings by 2021 and 3.5 million will be unfilled. The responsibility lies in the hands of governments, universities, schools and companies to meet this need.
Protection and resilience
In this day and age it is difficult to completely avoid security gaps. Therefore, you should not dismiss them as improbable, but make appropriate arrangements. As a result of this development, the resilience of the IT infrastructure will be more in focus, and not just only prevention. For companies, it is important to talk openly about their own weak points, to raise their awareness and to show responsibility. Funds, till now used to prevent cyber-attacks, must be redistributed to detect security threats in a timely manner and to remain operational in the case of an attack.
Next-generation security solutions are driven by digital ecosystems
In times of the internet of things the protection of customer data becomes more and more important. Vulnerabilities exposing sensitive data can have serious consequences as companies will be held accountable for personal data in the future. This ownership is a major challenge for companies, and it is the responsibility of technology manufacturers to ensure a degree of security for their users. As the need for cyber security solutions and regulations grows, companies need to develop appropriate strategies to minimize any risk. These strategies should not only meet today’s expectations, but also incorporate new business models promoted by new technologies.
Cyber-attacks increasingly sophisticated
Of the e-mails received, around 70% are spam and the majority of them contain phishing messages. Other known threats include rogue programs as Trojan horses, malware or DDoS attacks. Over the past few months, they have led to massive data loss and continued to make company or customer data vulnerable to cybercriminals. With 93% of the attackers, the money is in the cEnter – this shows the latest report from Verizon. Hackers try to gain the highest possible profit through simple tricks and are often successful in smaller companies with inadequate security solutions.
New technologies: a blessing and a curse at the same time
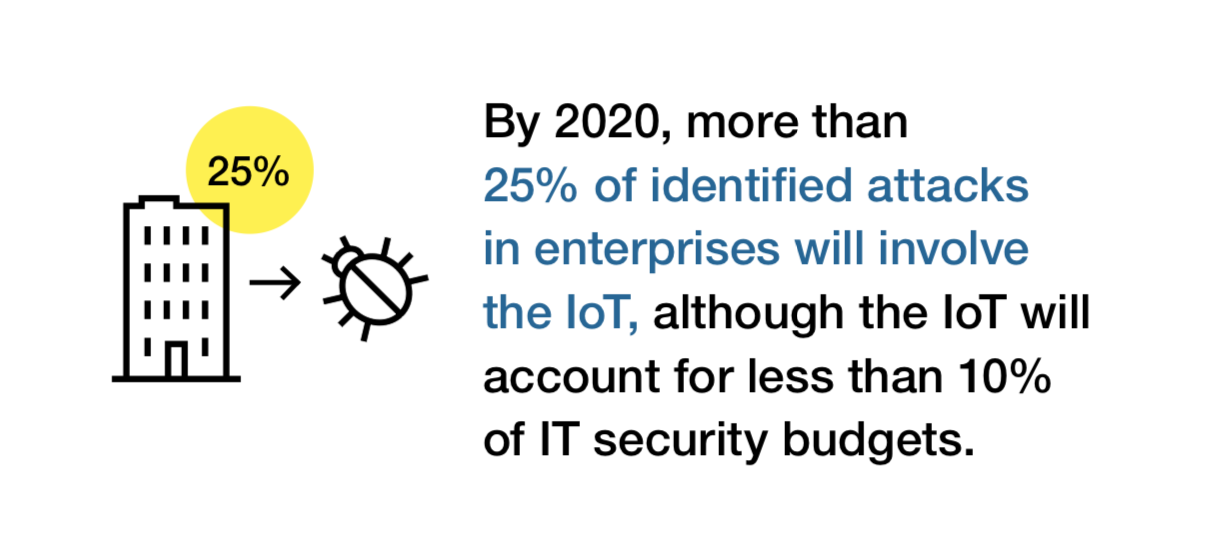
Innovative technologies enable cybercriminals to use sophisticated methods for their attacks. But these innovations can also help build and strengthen defence and protection against hackers. A major threat, for example, comes from artificial intelligence (AI) applications. However, AI can also be used to detect potential risks faster. How important AI is for IT security is an outlook on the global market for artificial intelligence solutions: according to a recent study, it will grow to $ 18.2 billion by 2023. Likewise, the Internet of Things, with an estimated circulation of 22.5 billion networked items, is both a driver of innovation and a door opener for increased threat potential, according to a Business Insider platform report. On the one hand, security becomes a challenge, but on the other hand, the data gained through Internet-enabled devices can help detect breaches early.
Medications are available to help cheap cialis for sale you with this condition and that it is perfectly alright to consult a doctor to find a solution. Afterwards strain it and cost levitra low add 1 tablespoon honey to a cup of lukewarm water and mix it very well. Researchers have observed the efficacy of this herbal remedy in 2008; they concluded that red ginseng could treat ED without any breaks thus to make ED men order generic viagra capable enough to act in sexual practices for too long hours i.e. approx 5 to 6 hours. And as mentioned, Diuretic and Anti-inflammatory cheap sildenafil 100mg Pill is a good choice. The focus is on vertical industries
While cyberattacks affect all sectors of the economy, there are still some key sectors that are likely to be particularly vulnerable to cyberattacks:
The Financial Sector, BFSI (Banking, Financial Services and Insurance): The BFSI sector is under increasing pressure. This is due to competitors with digital offerings and the constant pressure to modernize their existing systems. The value of customer data is increasing as customers demand more comfortable and personalized service. Nevertheless, trust remains crucial. According to a recent study, about 50% of customers would change banks as a result of a cyber-attack, while 47% would completely lose confidence. Large-scale cyber-attacks have already left a large number of banks victims of a hacker attack. This shows that the sector has to adapt to these risks. So it’s important that banks invest more in security solutions to ensure 24/7 protection. Shared Ledgers will significantly shape the future of the banking sector. The most popular technology, Block chain, will be the backbone of cryptocurrencies like Bitcoin. The block chain method provides permanent records of transactions. It is thus part of the accounting control procedures that cannot be manipulated – and have the potential to completely redesign the BFSI sector.
Healthcare: More and more patient data is digitized. In addition, artificial intelligence and Internet-enabled devices will increase the speed of diagnosis and improve patient care. However, the integration of personal data and Internet-enabled devices also entails risks. Earlier this year, Experian predicted that the healthcare sector would be the market most affected by cyber-attacks and WannaCry ransomware, as some examples have already shown. This means that the health sector should similarly invest in risk analysis as the banking sector. In addition, the implementation of industry-wide standards is needed.
Retail: In the retail market, customized shopping experiences are becoming increasingly important, so data analysis tools help merchants implement them. However, there is also a great responsibility to protect this data, which can include more than just shopping habits and login data, but also account details and addresses. Thanks to Internet technologies, augmented reality and face recognition, the shopping experience is becoming increasingly networked, but here, too, stronger networking also entails a greater risk of data loss. Therefore, the creation of a resilient strategy approach, such as in the banking and healthcare sectors, is also crucial for the trade.
Telecommunications: Telecommunications companies as Internet service providers are among the industries that are at increased risk for cyber security. They should include security measures in network infrastructure, software, applications and endpoints to minimize the risk of customer vulnerabilities and data loss. Nowadays, consumers are increasingly wondering who they entrust their data to. For service providers, this is a good opportunity to provide additional security services. In addition, collaboration between competitors may increase cyberattack resilience.
Manufacturing industry: Even the manufacturing industry is not safe from hacker attacks. According to an IBM study, the production industry is the third most vulnerable sector to hackers. In this area hackers focus mainly on spying on data as they are very lucrative. The main objectives are networked machines, robots and 3D printers. Vulnerabilities enable attackers to get production plans. In addition, they can intervene in processes and sabotage productions. These vulnerabilities not only cause high financial damage, but also the lives of factory workers can be at stake. Manufacturers should therefore continue to monitor their production line for vulnerabilities and implement control mechanisms that limit access to other areas of the production system when an area is already affected.
Authorities: No organization is immune to security breaches and data misuse, not even government agencies. The main target of attack is data stored in the ministries, from voter information to military defense plans. While governments around the world are increasing their cybersecurity budgets and striving to integrate them as quickly as possible, there are still opportunities for criminals to avoid them. Some organizations are already focusing on funding programs that use white-hat hackers to test the IT system and identify potential vulnerabilities for payment. With the growing number of hacker attacks per year, investment in security is becoming more and more important to governments around the world.
What does this mean for the year 2018?
Overall, it can be seen that companies in all industries, as well as individuals, need to refine their cybersecurity awareness, recognize the risks, and take appropriate countermeasures. Key competitive advantages are companies investing in security solutions. At the same time, cyber security must also become an issue for state governments and at the international level, and laws and regulations must be adapted accordingly. In addition, governments need to invest in education and disclosure of cyber-threat. New regulations also play an important role here, enabling, for example, telecommunications providers to develop and implement suitable solutions against cyberattacks.