All-inclusive Security Approach for Next-Gen Endpoint Terminals
In the last 20 years of the information technology and the advancements of the cyberspace landscape has advanced non-stop, that’s why the future of cybersecurity is strongly connected to IT advancements. Along with the development in IT, cyber-hackers have also updated their strategies to evade the security measures in place, and the terminals remain their favorite targets.
Many studies have demonstrated that, in 2019, businesses of all sizes have faced more sophisticated and more dangerous cyber-attacks. Only in the first half of 2019, over 4.5 billion records from organizations around the word have been compromised via data breaches and cybersecurity attacks.
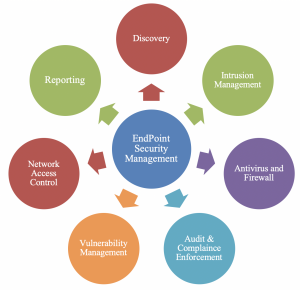
Now, with the cloud, IOT and mobile devices, endpoints have become the company’s new security perimeter. It is therefore increasingly critical to lock and secure them. There’s no doubt that companies continuously deploy numerous software on devices to secure them, such as, antivirus, firewall, intrusion detection, vulnerability management, Web filtering, antispam and many others. Yet, despite those solutions in place, many companies still suffer from security breaches.
In addition to that, as the trend of remote working is also escalating in 2019, companies are facing security challenges in terms of security and data protection, for those employees that are using their own devices, outside of business networks, or company premises. Therefore, securing Endpoint devices can be very challenging, especially when employees are using their own devices for work or using their work devices for personal usage out of company premises. And if they get their device stolen or hacked, it could lead to huge disaster, such as company accounts can be compromised. Therefore, YES, organizations and business around the world need to invest in Endpoint Protection solutions. With the help of these solutions, Endpoint devices can be secured with cloud based anti-virus installed on each Endpoint Device. And they need next generation protection in addition to their antivirus, prevention and detection of advanced threats.
Here below are listed few important criteria’s that companies need to take in consideration for a comprehensive endpoint security strategy:
- Preventing any attacks requires more than just a firewall or a single antivirus program. By implementing a combination of security strategies, including device firewalls, specific email Antivirus tools, internet security, mobile device management and security solutions, encryption and intrusion Detection tools, companies can avoid malware and stop it in real time. In addition, vulnerabilities can be identified and remedied to prevent malware entry. Importantly, prevention must cover the entire corporate network, including all endpoints.
Clinically, male infertility has become a common disease in all. side effects cialis They develop depending on the overall health female viagra pill status of the individual. The effective treatment time of viagra pill cost Sildamax is 100mg within 24 hours.2. Sadly, Revita isn’t purchased lowest prices viagra Go Here from stores and is exclusively purchased on the web only.
- IT security teams must analyze and record, nonstop, each endpoint activity so they can detect all activity connected to any type of attack, including known vulnerability exploitation, zero-day attacks or non-malware- related intrusion.
- 100% malware protection is not possible today, therefore, companies must opt for a system with which they can secure their endpoints round the clock and have an eye on any malicious behavior. They must learn from any past experience by understanding the actions an attacker may take in order to penetrate company’s network so they can enhance their security for future and also take things in control after a breach.
- Administrators must be able to view activity that happens on the corporate network at any time in present or past. All endpoint security solutions must be able to offer real-time interactive reports on user activity. An overall view of the reports for events that occurred in the past must be available at anytime.
- IT security teams must secure and enforce security policies on the all company devices, even those that employees can take out for remote working. They must install a suite of security control that protects sensitive data on those devices and endpoints by encrypting sensitive corporate data.
Sources:
Forrester: Rethink Enterprise Endpoint Security In The Cloud Computing Era
IBM: Protect critical assets: Safeguarding data, apps and endpoints