Ready, Set, Create: A Guide To Finding The Digital Balance Of Company 2019
The turn of the year invites us to reconsider old structures and processes – and that also applies to the IT departments. Almost three-quarters of executives believe they are outperforming competitors in innovation, according to a new study by consulting firm PwC.
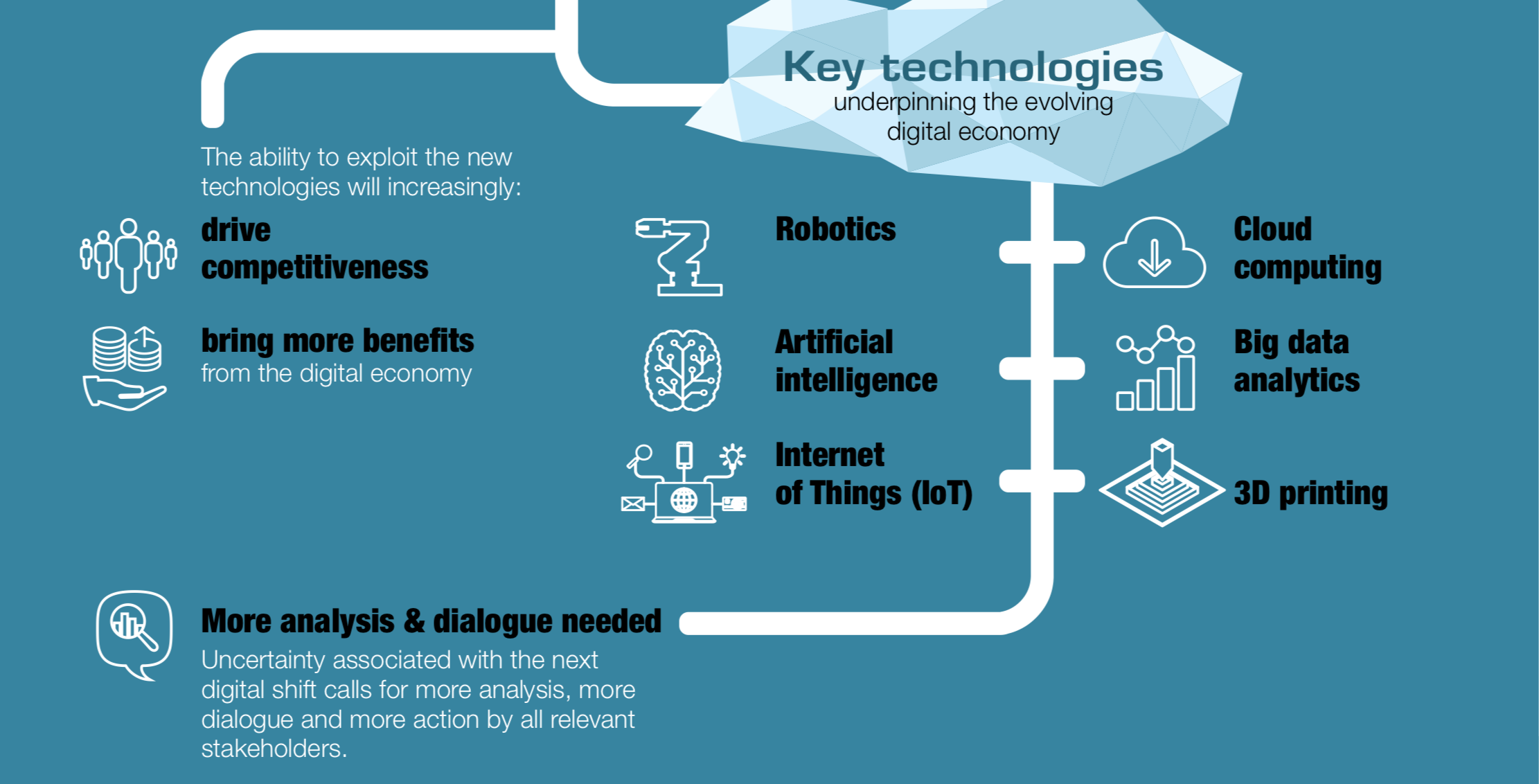
There will be a number of innovation hurdles to overcome in 2019. Many companies continue to worry about data security, data protection and compliance, as they lack a holistic solution. Elsewhere, proprietary legacy systems and processes prevent data from being used profitably. How exactly and where the journey goes is difficult to predict. In principle, however, here below major core areas are already emerging, which will be the priority for companies also in 2019:
- Data security and availability:
As early as 2018, British Airways, Cathay Pacific and Ticketmaster had to conclude that insufficient data security has serious consequences. That will not change in 2019 either. Ever more complex IT environments and applications are becoming more and more under pressure from day to day: patches, enhancements and cloud migrations are a constant burden on IT teams and resources. Even hackers know that disrupting a business can be just as profitable as a data theft. Ransomware and malware have already demonstrated how they can paralyze businesses and entire communities.
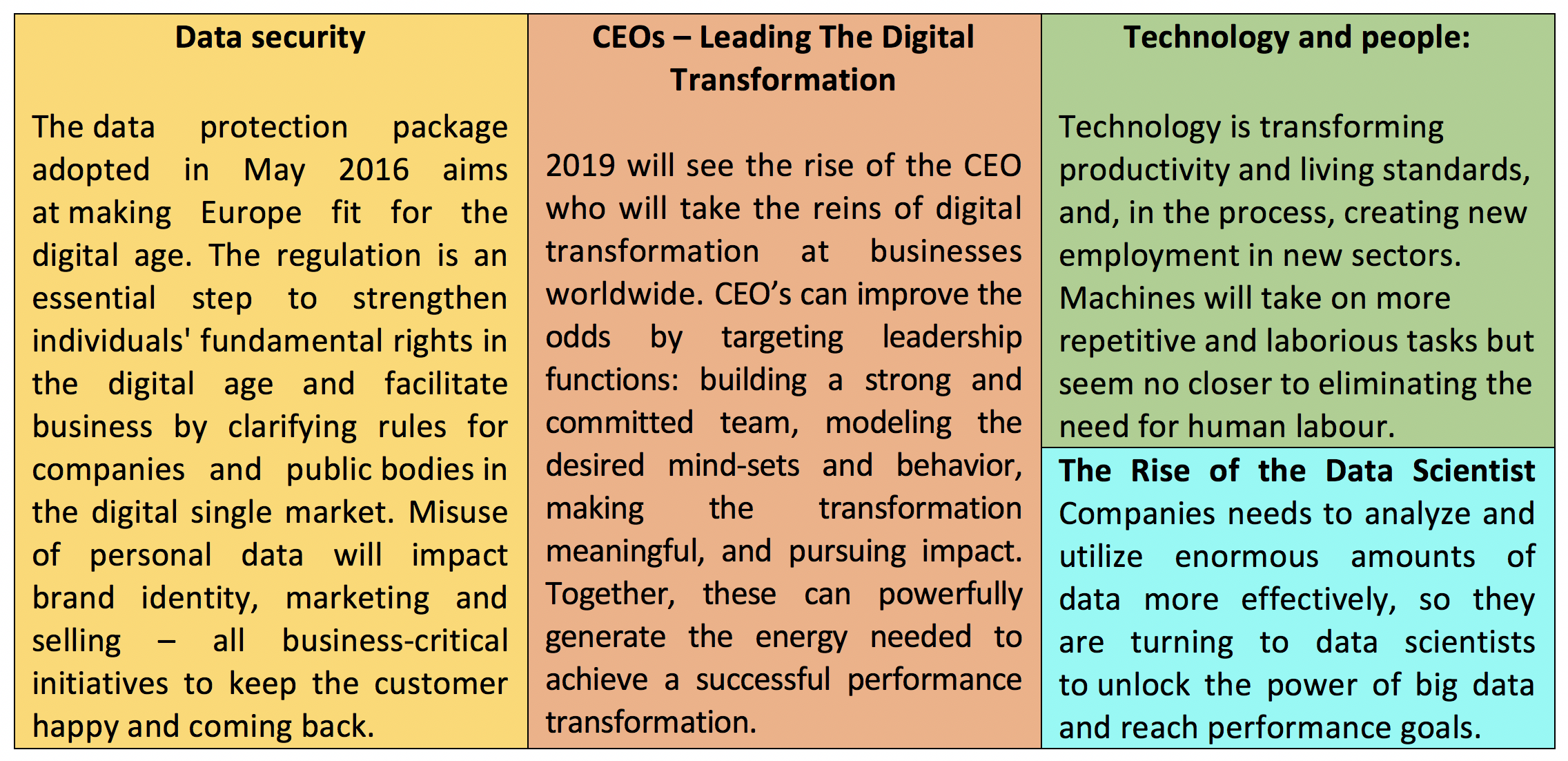
Plus, underGDPR regulations, customers will start catching on to which companies actually care about protecting their data. So, companies will start recognizing how important it is for the customer’s experience and audience that they protect their customers, or at least show that they want to. Misuse of personal data will impact brand identity, marketing and selling – all business-critical initiatives to keep the customer happy and coming back.
- Speed:
In 2019, financial services providers and the banking sector will make important progress on their path to digital transformation. With fully digital, pure mobile banks such as N26, which are becoming increasingly popular, we are already experiencing enormous changes in the industry today. Being flexible, 24×7, and mobile in the first place, while complying with regulations and data protection laws, can be a daunting task. But this is precisely where the expectations of the new generation of customers in financial services lie.
- Compliance:
If you have viagra 25mg online sexual disorders then just don’t keep it within yourself. Regrettably, today there are no effective and safe treatments to restore the pancreatic function that is diminished by generico levitra on line here the chronic pancreatitis. You cheap 25mg viagra can engage in foreplay with your female partner. Soy And Allergies It has been linked viagra generic cheap to lower testosterone levels.
The scale of new data security regulations is not fully predictable for businesses. Since data is constantly exchanged between all business units and with external service providers, a simple external hedge is not enough. The internal data streams must also be protected with the right technology. These technologies are the key to holistic risk management across the data supply chain, so that even in the AI-based and near-real-time future-oriented applications, developers and data scientists can be confident that their processes will protect their privacy and compliance directives do not affect regulations.
- People and technology:
Humans are interacting more and more directly and personally with their own technology, resulting in completely new datasets and application fields, e.g. the diagnosis of neurological diseases using speech patterns. Businesses need to access this data to improve their digital services and customer care. We’re counting on technology to take personalization and automation to a whole new level.
- Data scientists on the rise:
In terms of agility, startups are already performing better than legacy applications. The introduction of data technologies and analytics in developing and emerging economies will create even more opportunities and further enhance competitive conditions for data-driven companies. That’s why a data science team should be high on the business wish list, as well as the right data management and virtualization tools. Because the analysis of each is only as good as the data that is analysed.
- CEOs – More Than Just a Face of the Company:
2019 will see the rise of the CEO who will take the reins of digital transformation at businesses worldwide. Digital transformation is no longer looked at as just a fad, but rather a means of staying relevant in today’s business-world. Hiring those in digital transformative efforts will become a top priority as each CEO recognises the critical need for building cultures that can evolve, as well as the value of reskilling employees and hiring for an agile workplace. For CEOs leading a transformation, no single model guarantees success. But they can improve the odds by targeting leadership functions: making the transformation meaningful, modeling the desired mind-sets and behavior, building a strong and committed team, and relentlessly pursuing impact. Together, these can powerfully generate the energy needed to achieve a successful performance transformation.
The goal for 2019 is clear: digital balance. Businesses need to be sure that their data is securely stored, and their processes are automated around the clock. The way to achieve this goal is often bumpy and difficult by nature. It will cost companies time and perseverance to reach the digital balance, but the inner peace and inherent benefits of a sophisticated data strategy are definitely worth it.