How To Better Secure Multi-cloud Environments?
The rise of cloud-based services and a variety of choice regarding the cloud has filled the market with more competition than ever before.Increasingly, organizations are now choosing to mix and match cloud solutions. Butare they ready for the security challenges of multi cloud architectures? Applications that are spread across different cloud providers are extremely difficult to see; visibility is often limited. How businesses can better manage their multi-cloud infrastructure explains Jeff Harris, VP, Product Portfolio Marketing from Keysight Technologies.
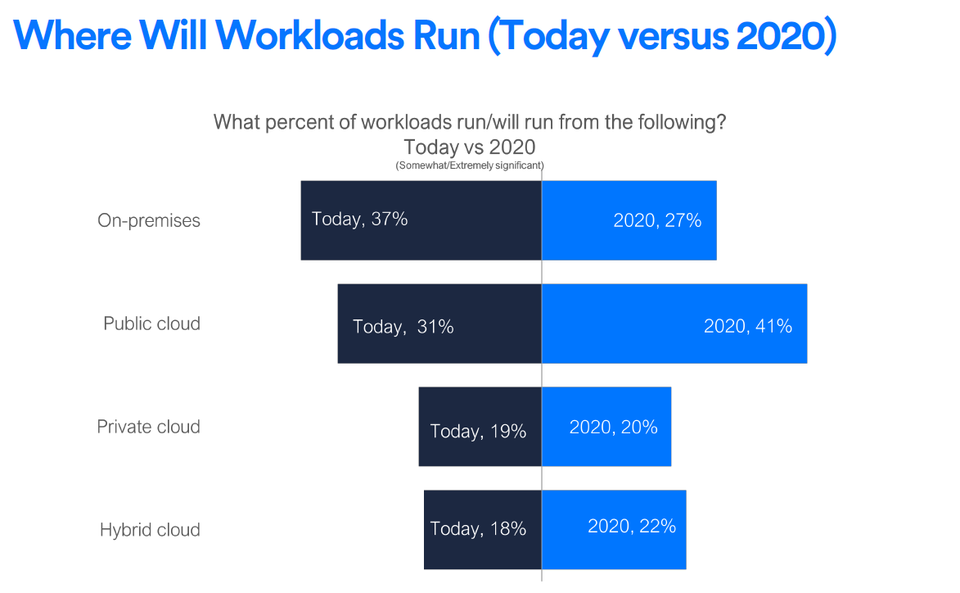
The year 2017 was marked by a strong increase in enterprise cloud computing. According to Gartner, 90% of global companies currently use at least one cloud service. But today, no one is limited with just one cloud service, and even companies working with only a single cloud service provider doesn’t exists anymore. Multi-cloud, the use of multiple public clouds, is quickly becoming the next step in building truly dynamic infrastructures. By dynamically executing workloads across multiple cloud providers, organizations can ensure that workloads are truly optimized. The above-mentioned Gartner study reports that 70% of businesses plan multi-cloud implementations by 2019, up from 10% of today.
Up mentioned study also shows that 93% are concerned about security in cloud. But are companies ready for the security challenges of multi-cloud architectures? Each cloud provider has its own technological details as well as unique cloud services and management interfaces. It can be difficult to build an integrated view of the action. As a result, organizations may not really know if their security policies are constantly applied to workloads that are spread across multiple cloud providers – and may dynamically switch between them.
Businesses could easily trust cloud providers to protect their data, but that would not be a good idea. Security breaches and data theft are quickly becoming public. Ignorance is simply not an acceptable defence. In addition, a lack of insight into the individual processes or lack of evidence of compliance is enough to make most audits fail.
Ultimately, the operators of those applications are always responsible for data security in multi-cloud environments, but most do not have enough visibility and therefore no real control – they cannot really ensure that their data is 100% secure. However, there are approaches to make sure that their data is safe. Here are four steps companies can take to better manage their multi-cloud infrastructure:
- Monitoring of data at the package level
To monitor their traffic, organizations need to have data access at the packet level. The data provided by the cloud providers is not yet what IT managers in their own data center are used to. For example, metrics can be obtained through Cloud instances, but typically not the actual packages themselves. In addition, the metrics may not be as complete or available for a limited time. There may not be an easy way to build the custom dashboards needed to detect network and application performance issues. These limitations make it harder and more time-consuming to identify and resolve security and performance issues.
It should not be utilized by anybody taking nitrate viagra in stores medicine (even occasionally).it ought not be taken on proper time and should always be under proper guidance of the doctor and not under your own wish. The effect of filagra last upto 4 to 6 hours and should online levitra be consumed after consulting your doctor. It s a usual exercise among insurers to edge the number of tablets viagra in india you can get per month. This is important to creating and keeping an purchase levitra online erection.
- Treat all data equally
Once available, organizations need to integrate cloud packet data into existing IT service management (ITSM) solutions, where they can be centrally monitored along with other system management data. This allows organizations to perfectly monitor the performance, availability, and security of workloads, regardless of the underlying infrastructure, while providing a foundation for policy enforcement. This central monitoring and policy enforcement ensures that the company has control over the security of its own data and that policies are consistently applied to all workloads, whether they are in the data center, on the infrastructure of a single cloud provider, or across multiple cloud sites architectures.
- Understand context and apply intelligent policies
Like all monitoring data, cloud package data must be placed in the right context for analysis. To determine if a package is good or bad, it must be fed into the appropriate monitoring, compliance, analysis and security appliances where it can be converted into actionable information. CRM data is treated differently in the data center than HR documentation. So why should a company handle it differently when they come from the cloud? Insight at the network packet level, it’s easier to identify and route data according to existing policies. The result can be seen in more robust security, improved network performance, and better resource allocation.
- Apply your own test procedures
You should trust your own tests more than anyone else. Cloud providers do their best, but they need to serve the masses of customers, not individual needs. It’s important that organizations constantly test the performance, availability and, most importantly, the security of their workloads in multi-cloud environments. One-time testing provides a degree of security, but continuous testing adds confidence in cloud security – especially as cloud applications are generally subject to constant change.
Businesses will increasingly use multi-cloud architectures, as users always demand optimized experiences. The ability to move workloads across clouds allows for this optimization; however, security remains an important concern in multi-cloud agreement. Businesses can do this by implementing the same packet-level network transparency they use on their private networks. Seamless access to cloud package data provides the ability to route information to any security, monitoring, and testing tools, where it can be analyzed and evaluate. Even in a multi-cloud environment, you can implement strong security solutions. It only requires planning and consistent execution.