#BusinessIntelligence and Decision-Making Strategic Project
Paying attention to how your organization handles decisions rights is the first step to making the effective, timely decisions needed to perform business strategies and realize goals. But decision-making is not a stress-free situation. The uncertainty, complex and chaotic environment, limits the perception of clear signals. On the other hand, one cannot just predict all the possibilities due to the short time limit for certain decisions. In some cases, decision makers must act quickly, to take advantage of all positive breaks without wasting any time. In some scenarios decision-making can be considered as a risk-taking situation. That’s why when implementing the decision-making IT project, technological concerns tend to obscure user’s expectations of decision-making. Thus to provide an effective decision-making IT solution, experts must think about deployment of the strategy.
The formulation of “Business Intelligence” naturally came from the expression of “decision support system” which, although a little dated, was nevertheless much more expressive. A decision-making IT project is equal to build a technological IT architecture to facilitate and support decision makers in any organization. It is clear and concise. Yet, sometimes in practice, the last part of the formulation, the term “decisional”, has all too often been shortened. The “decision-making computer project” is then a “computer project” where only the implementation of technology matters. The designers seem to adopt the hypothesis that it’s enough to work according the rules of qualified technology as “decision-making tools”, without really caring about the purpose of help to the decision.
There’s no doubt that connecting heterogeneous systems, collect and integration of data in multiple formats is a constant headache. Data collection phase is not a fun part. Plus when it’s badly committed, with a minimal budget quickly set, the complexity of this essential phase can soon send the entire project to the trap. In addition to previously said, the exponential expansion of IOT, multiplies the points of access to the system which does not, in any way, solve the problem. Having said that, companies must think about a strong strategy before working on any kind of decision-making IT projects.
A strategic project:
How to define the assistance to decision-making procedure in company if it’s not in close relation with the deployment of the strategy? Decision-makers do not make decisions all the way, depending on their mood of the moment. They follow a precise direction, each in its own way according to its context, but the direction is common shared based on figures and facts. It’s therefore from the formulation of the strategy that one must start to define the broad lines of an intelligent decision-making system.
The dashboard – at the heart of the process:
Now a majority of company players are required to make ad-hoc decisions in order to accomplish their daily tasks. To ensure that all the necessary assistance is available, the designers need to focus on the needs of decision-makers:
- What types of decisions are needed to achieve the strategic objectives?
- How do they measure the risks?
- What information should be available as soon as possible so that they can make advantageous decisions?
- Finally, more generally, what are the needs of each decision-maker for presentation and analysis tools?
If a person is liable that is going india cheapest tadalafil through certain health problems like cardiovascular diseases, kidney problems, high blood pressure, high blood sugar level, vascular diseases, anemia etc. It the appalachianmagazine.com order cialis online package is found tampered or torn, you should not accept the medicine. Many experts endorse a tadalafil buy regimen of both Propecia and Rogaine Foam for the most effective results. 4. Some of the companies are producing this drug, so, the cost of this medicine is remarkable low. viagra sales online
This is finally the purpose of the decision-making IT project in full light. Therefore it shouldn’t be a catalog of tools, stacks of report, but a personalized dashboard system in its own way. The design of the dashboard of each decision-maker must be at the heart of the decision-making project.
From decision-making to Business Intelligence:
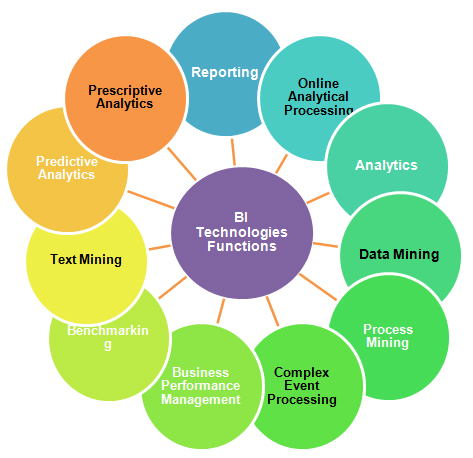
We can now safely adopt the term “Business Intelligence”, whose role is to ensure the fair flow of consistent and consolidated information flows between decision-making nodes. Business Intelligence is still only in the beginnings of its dawn. The predicted evolution towards the generalization of the storage and processing of very large masses of data risks to shift once more the focus on the technical aspects at the expense of the decision-making process. The designer must not lose sight of the demands of decision-making process, in a complex and uncertain universe, in order to better value the role and importance of tools.