Best Practices to Implement Cloud-Based Endpoint Management
In today’s fast-paced digital landscape, businesses are constantly striving for efficiency and productivity. One crucial aspect of achieving this is effectively managing endpoints – all the devices and systems that connect to your network. But with the rise of cloud technology, a new game-changer has emerged: cloud-based endpoint management.

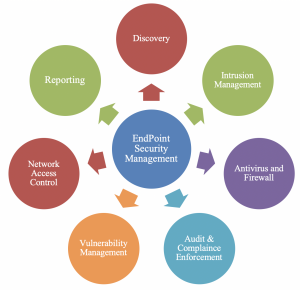
Implementing cloud-based endpoint management involves the use of cloud services to manage and secure devices like computers, smartphones, and tablets within an organization. Here are some best practices to consider when implementing cloud-based endpoint management:
- Define Clear Objectives: Clearly define your goals and objectives for implementing cloud-based endpoint management. Whether it’s improving security, enhancing device monitoring, or streamlining software updates, having a clear vision will guide your implementation strategy.
- Choose the Right Cloud Platform: Select a cloud platform that aligns with your organization’s needs and preferences. Popular choices include Microsoft Azure, Amazon Web Services (AWS), Google Cloud Platform, and others. Consider factors like security, scalability, and integration capabilities.
- Centralized Management: Use a centralized console to manage all endpoints. This enables you to monitor device health, enforce policies, and deploy updates from a single location, simplifying administration and reducing operational complexity.
- Security First: Security should be a top priority. Implement strong authentication mechanisms, role-based access controls, and encryption for data at rest and in transit. Regularly update security patches and monitor endpoints for any vulnerabilities or breaches.
- Automated Patch Management: Implement automated patch management to ensure that all endpoints are up-to-date with the latest security patches and software updates. This helps protect against known vulnerabilities and minimizes the risk of cyberattacks.
- Policy Enforcement: Set and enforce security policies for endpoints. This could include password requirements, firewall settings, antivirus software installation, and more. Automation can help ensure consistent policy enforcement.
- Device Inventory and Monitoring: Maintain an up-to-date inventory of all managed endpoints. Use monitoring tools to track device health, performance, and security status. This helps identify and address issues proactively.
- Remote Management: Enable remote management capabilities to troubleshoot and resolve issues without physical access to the devices. Remote tools can help save time and reduce downtime for end users.
- User Education: Educate end users about the benefits and features of cloud-based endpoint management. Provide training on security practices and how to interact with the management platform to ensure proper usage.
- Backup and Recovery: Implement regular data backups for endpoints to safeguard against data loss due to hardware failures or other issues. Ensure that recovery processes are well-defined and regularly tested.
- Scalability and Flexibility: Design your cloud-based endpoint management solution to be scalable and adaptable to your organization’s growth. As your device count increases, the system should be able to accommodate the additional load seamlessly.
- Regular Testing and Updates: Regularly test the endpoint management solution and its components. Ensure that updates and changes to the cloud platform and management tools are thoroughly tested in a controlled environment before deployment.
- Compliance and Regulation: Ensure that your cloud-based endpoint management practices comply with relevant industry regulations and data protection laws, such as GDPR, HIPAA, etc., depending on your industry and geographic location.
- Vendor Support and Community: If you’re using third-party tools or services, ensure that the vendor provides strong support and has an active community. This can be helpful when troubleshooting issues or seeking guidance.
- Continuous Improvement: Regularly review and refine your cloud-based endpoint management strategy. Incorporate feedback from users and IT staff to enhance efficiency, security, and user experience over time.
By following these best practices, you can implement an effective and secure cloud-based endpoint management solution that enhances device security, reduces operational complexities, and improves overall organizational efficiency.
The main goal of endpoint management is of course improving operational efficiency by streamlining device maintenance processes, such as regular updates, policy enforcement, and troubleshooting; and enhancing cybersecurity posture by implementing robust protection measures against malware attacks, data breaches, and other potential threats. As technology continues evolving at a rapid pace, having effective cloud-based endpoint management strategies becomes even more crucial for businesses aiming for seamless productivity, greater cost savings, and heightened data security. Contact us for your digital projects, together, we can build future-proof solutions that offer real value to your business and customers.