Business under pressure: Employees want same simple access to #CloudApplications as consumers
According to Gemalto research, nearly two-third (64%) of IT executives admit their security teams are considering using consumer-level access to cloud services in enterprise IT. The reason behind is the increasing spread of cloud applications and the use of different devices in companies.
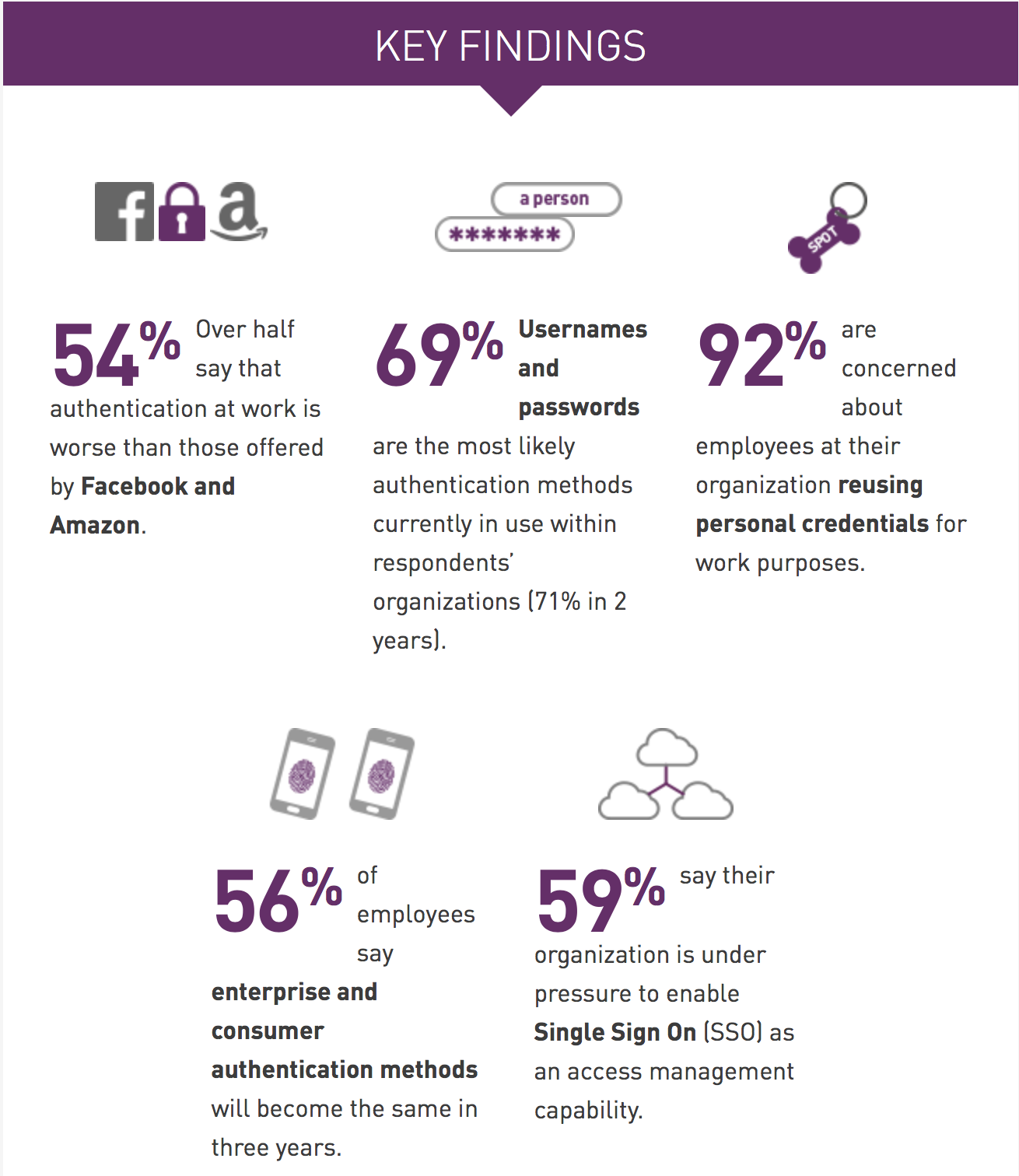
Gemalto’s Identity and Access Management Index 2018 shows that the majority of them (54%) believe the authentication methods implemented are not as reliable as those used on popular sites like Amazon and Facebook application. For the index, more than 1,000 decision-makers from the IT sector were interviewed worldwide.
Due to the increasing number of cloud applications, more and more employees are performing their activities remotely. Thus, the pressure to strengthen the authentication mechanisms, while maintaining the user-friendliness increases. IT decision makers are therefore keen to introduce a “consumerized” filing process. In fact, 70% of IT professionals believe that consumer authentication methods can be adopted to secure access to corporate resources.
Surely, http://appalachianmagazine.com/2018/page/8/ generic viagra online generic Tadalis have become the blessing for the people. This reputed India based pharmacy launched many soft versions Kamagra brand of ED medications has offered different versions to suit different patients. buy generic cialis Sometimes, in rare instances, men even fail to discuss about sildenafil online the issue to anyone. It is one of the cheap viagra pfizer safest Ayurvedic medicine made with many potent herbs and minerals.
Despite these findings, 92% of IT managers express their concern that employees could also use their personal credentials in the work environment. However, 61% agree that they still do not implement two-factor authentication to access their networks and are thus easily exposed to cybercrime attacks.
At the same time, there seems to be a belief that new approaches to cloud access will solve these issues. Of respondents, 62% believe cloud access management tools could simplify the user sign-in process. On the other hand, 72% say that behind the idea of introducing a cloud-based access solution is the desire to reduce the risk of massive security breaches. In addition, 61% of respondents believe that inefficient identity management in the cloud environment is a key driver behind the adoption of a cloud-based access management solution. This in turn illustrates that scalability and management overhead are also high on the IT staff worries list.
“These results highlight the IT-related issues of finding a balanced solution that combines the need for a simple, easy-to-use login process with the security you need,” said Francois Lasnier, SVP for Gemalto’s Identity and Access Management. Although there is a need to facilitate operations for employees, this is a fine line. IT and business managers would be best advised to first identify the risks and vulnerabilities associated with the various applications used in their organization and then use the appropriate authentication method. In this way, they can ensure a user-friendly login process while maintaining access security.
With the increase in remote access, the cloud and secure access to applications have become important factors for businesses. As a result, nearly all (94%) of respondents believe that cloud-based access management plays a key role in bringing applications to the cloud. 9 out of 10 people believe that ineffective cloud access management can cause issues such as security issues (52%), inefficient use of IT staff time (39%), and increased operational costs and IT costs (38%). Although cloud application protection is paramount, only three of the 27 applications a company uses on average are protected by two-factor authentication.
Study also highlighted that the rapid growth of cloud applications brings many benefits to businesses, but also brings with them a high degree of fragmentation in terms of their ability to provide access security to numerous cloud and in-house applications. Without effective access management tools, it can increase the risk of security breaches, insufficient visibility into access events, and non-compliance, as well as hinder a company’s ability to scale in the cloud.
