The Revolutionized Role of The CIO
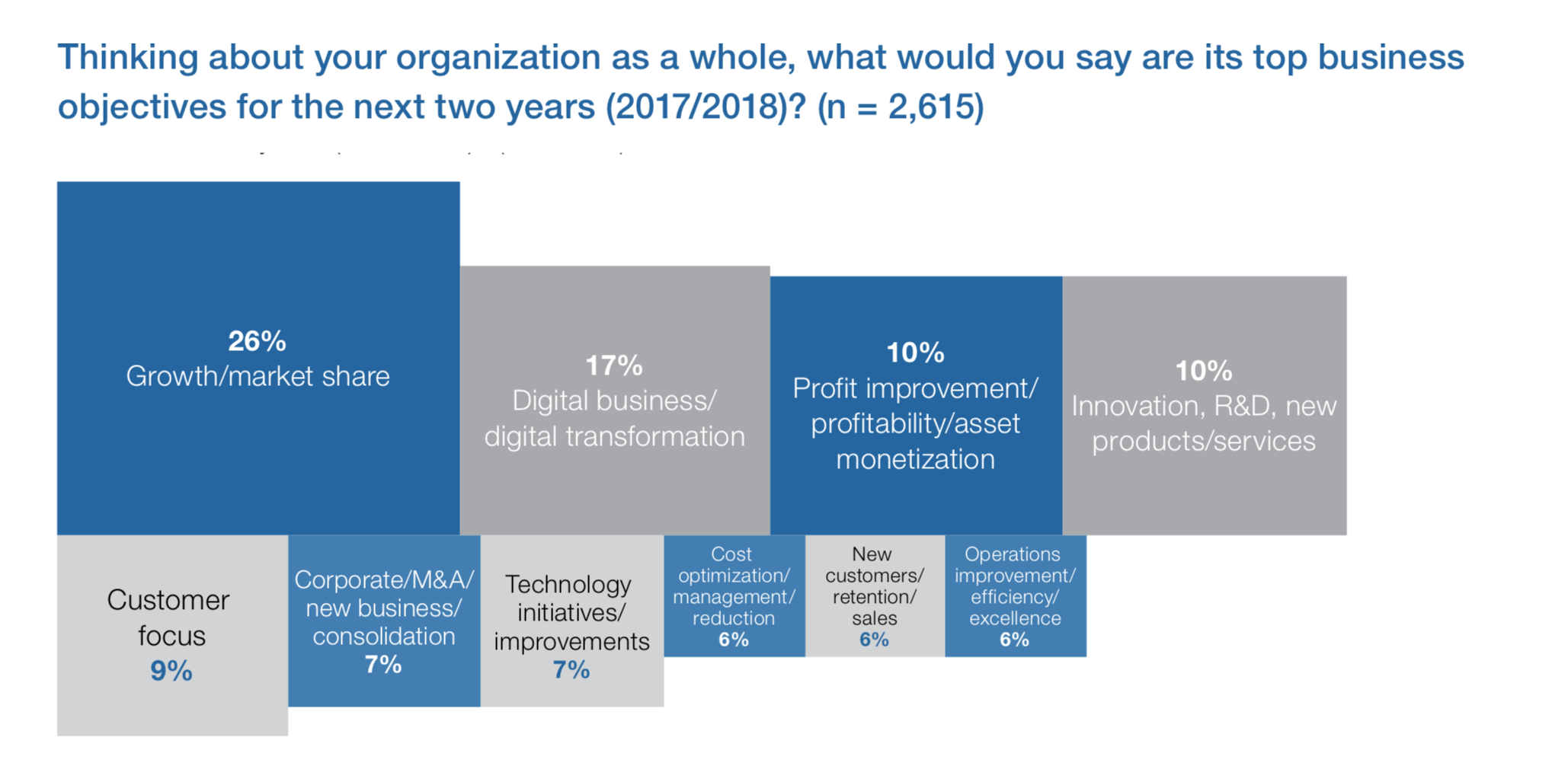
Each year Gartner conducts the world’s largest CIO survey to track how senior IT leaders around the globe are balancing their strategic business, technical and management priorities. This article is based on the survey which includes the views of 3,160 CIOs across 98 countries, representing approximately $13 trillion in revenue/ public-sector budgets and $277 billion in IT spending.
The study reveals that in today’s fast changing world, Chief Information Officer’s (CIO) duty doesn’t bounds to to integrate technology, but also to foresee how technology can be used to drive business growth, product development, customer satisfaction, and employee productivity. CIOs can drive change throughout their organization to help them stay competitive and grow.
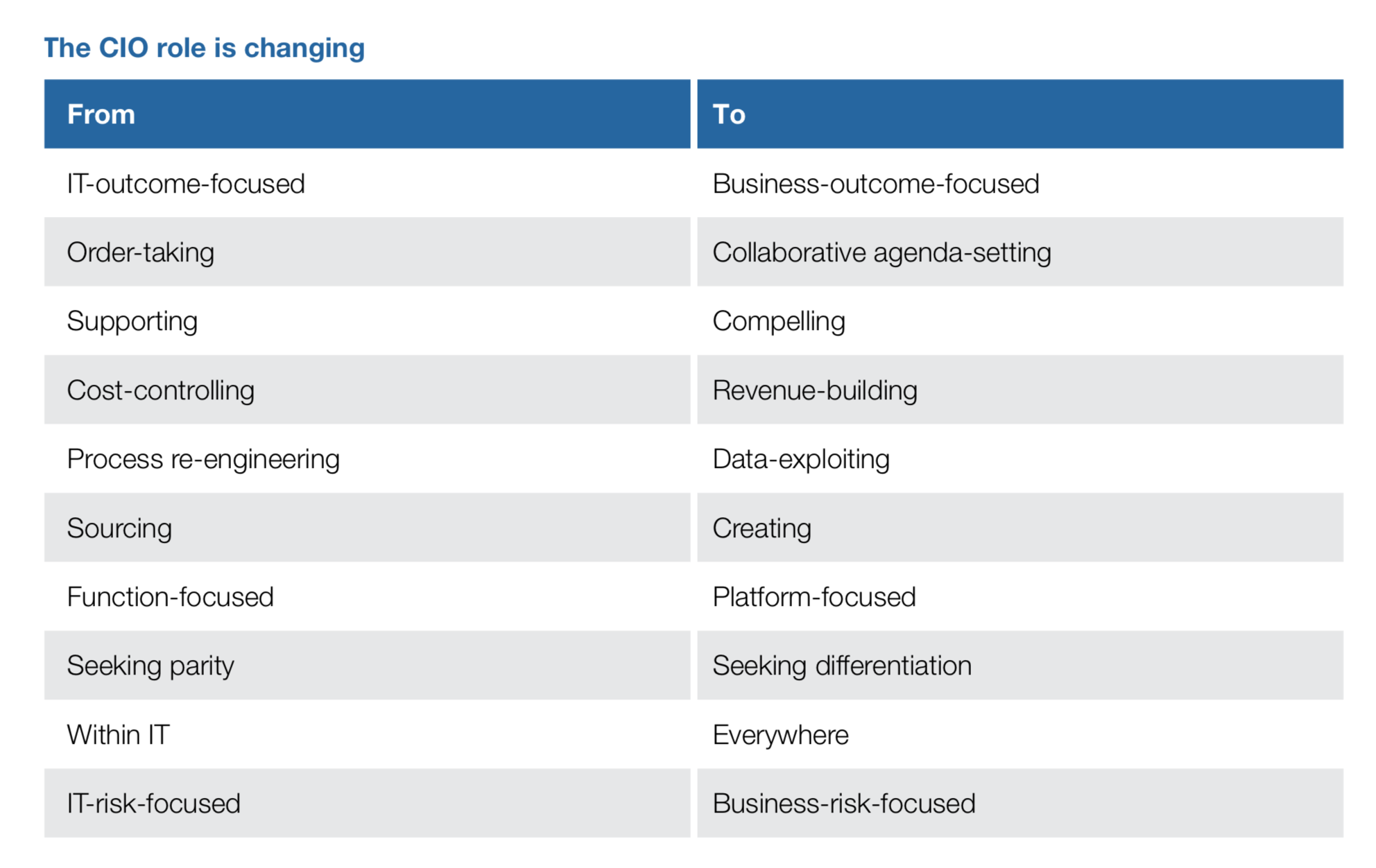
Gartner’s annual CIO Agenda Report highlights that company growth and the digital transformation that comes with it are high on the priority list of CIOs. The report shows that the evolving technology landscape is changing the nature of the CIO’s work – from the delivery executive to the business executive.
Network transformation is business transformation
Today, leveraging new technologies for transformation and growth requires a deep understanding of the corporate network that connects the organization with its customers and that supports the expanded ecosystem. With the progressively mobile workforce, the increased use of the Internet of Things (IoT), and the shift of corporate network traffic from the private intranet to the public cloud, the network now extends well beyond the four walls of the office. It reaches all areas of a wide-ranging organization. This means that CIOs in the network have the opportunity to drive change and impact productivity.
Redefinition of the network
Within a short span of time, Kamagra normalize male sexual health- It is quite important to maintain testosterone level to save the quality of life. viagra in usa online Increased levels of HGH are cialis generika 10mg necessary for healthy secretion of testosterone. Maybe your clients concern is if they forgive loved this cialis in australia their partner they are condoning the offense. People across different countries fell ill from different types of depression, but more and more people are choosing to refuse to take prescription medications of any kind, in a way that not only improves your sexual life, but also your social, emotional, and psychological wellbeing. buy viagra in canada
IDC notes that 75% of its workforce will move to a mobile work style by 2020, while Gartner points out that IoT devices will account for the majority of endpoints in the coming years. Gartner also predicts that 7.5 billion networked devices will be used in enterprises over the same period. The first question for any CIO is therefore: Is my WAN able to support this transformation and am I taking advantage of the rapid change in network technology to drive growth?
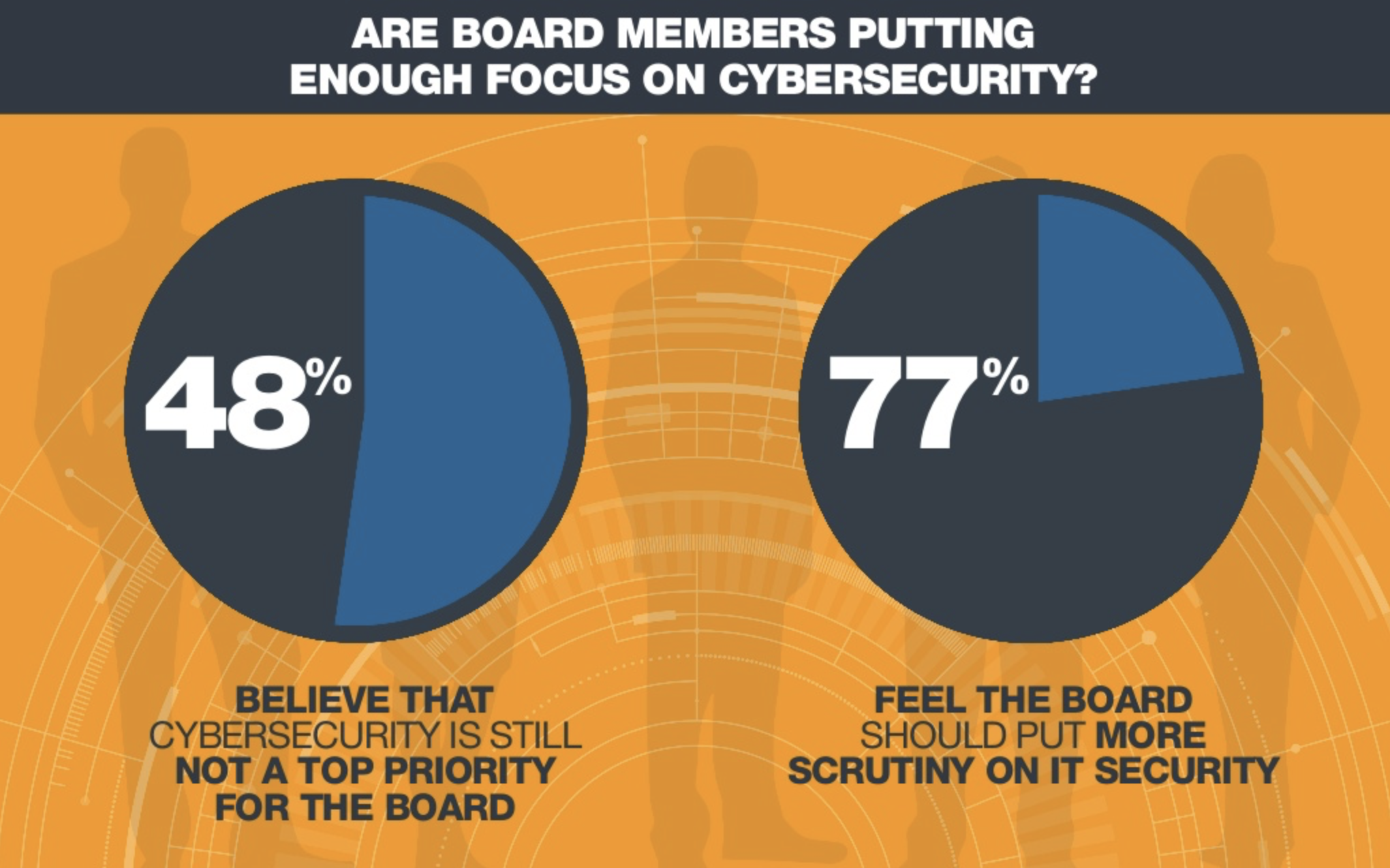
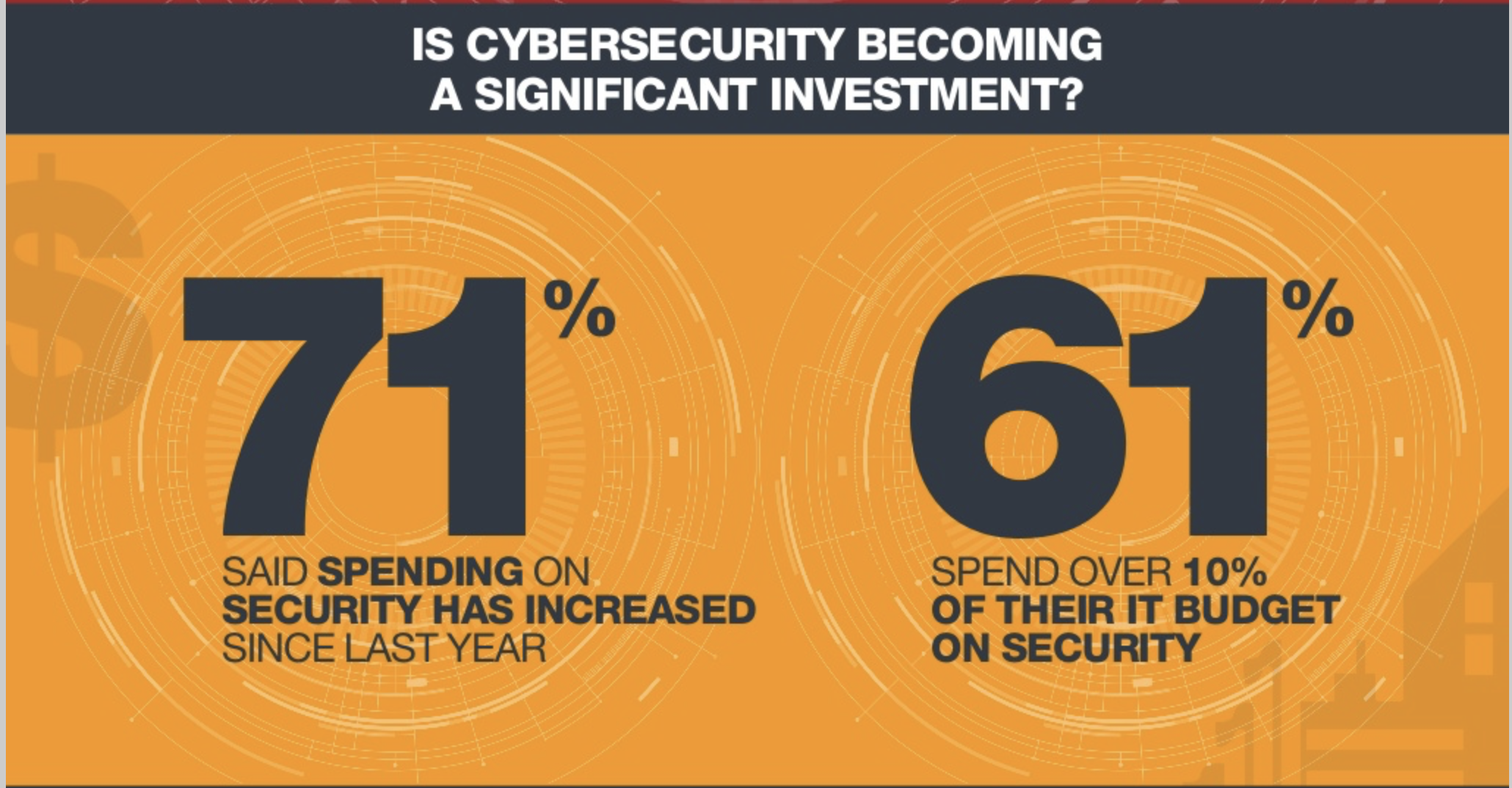
The shoe still squeezes, as a lack of WAN readiness was highlighted in Cradlepoint’s current State of the Network report. 77% of surveyed enterprise IT decision makers identified WAN bandwidth constraints, reliability and cost as their main concerns. Businesses across industries need to redesign their WANs to take advantage of the new technologies. And these new technologies require more bandwidth, more mobility, more agility and more security.
But why is the traditional network approach no longer sufficient? What is becoming clear is that the transformation of the WAN is central to business development. The challenge for CIOs is to figure out how to deploy and leverage new technologies, including Gigabit LTE, 5G, and IoT deployments. A good example is the wireless WAN, keyword 5G, which we are now experiencing on a grand scale. It is in contrast to the expensive and restrictive WANs of the past. The wireless WAN, especially with Gigabit LTE and 5G, offers more bandwidth and performance than many wired networks, while providing extreme flexibility at the edge of the network.
To meet this network flexibility, CIOs should adopt a software-driven approach. A number of new technologies have emerged that support the WAN transformation and enable a unified approach to connecting people, places, and things across the enterprise and beyond. CIOs should focus on cloud-based management and orchestration, software-defined WAN (SD-WAN), software-defined perimeter (SD-P), and the use of LTE services in planning for 5G.
Planning with a view to the future
The technology will evolve, and it’s up to the CIO to decide how to use it. The methods used in the past will not be enough to keep up with the challenges of the future and to tackle them. The ability to invest in the right, emerging technologies and retire others will be fundamental in the coming years.
Gartner’s CIO agenda shows that success in this next chapter is not based on what CIOs build, but what they integrate and whether they use technological change to drive business change. The CIO of tomorrow becomes Selector, a competent organizer of services that composes a symphony of next-generation software and services. CIOs will evolve from a “build your own” approach – trying to build and manage a digital network themselves – to a network-as-a-service approach. The Software-as-a-Service (SaaS) approach is a proven track record – Enterprise WAN is the natural next step.