The 9 Biggest Cybersecurity Myths Exposed !
In today’s high-tech era, there is hardly anyone who is not confronted with IT security in any way – it can be morning log-on to the workstation, installing a smart home appliance, or reading about the next big hack of a business.
The devastating effects that a security breach can have on an enterprise, coupled with the bright global spotlight on the issue, can give a very bad reputation to an enterprise. While most in leadership positions today recognize the elevated importance of data security risks in their organization, only few of them understand what action should be taken to address these risks.
Plus, despite the increased focus on corporate cybersecurity, there are still a number of common misconceptions and myths that seem to be difficult to remove. These are many superficial facts that, although often repeated, do not become correct. The problem is: If you follow and believe them, it quickly becomes dangerous.
Myth 1: A strong password protects access to sensitive accounts
Strong passwords are certainly an essential root for cybersecurity, especially in business. However, implementing and enforcing strong password policies is just the beginning, which needs to be complemented by other measures such as two-factor authentication and effective monitoring. In fact, one of the key components of cybersecurity prevention, which is often overlooked by businesses, is not how people access the information, but what information is actually accessible. Not only do employees need secure passwords, but companies also need to know who they can access. For example, the 2018 data risk report shows that in 41% of companies, all employees have access to at least 1,000 sensitive files – such as personal data, credit card or even medical information. In addition, many companies do not have a system for monitoring administrator access and have no idea what their users are doing with what data.
Myth 2: Hackers are not interested in SMEs
Myth is, that by looking at the coverage of cyber-attacks, one can easily conclude that these are first and foremost aimed at large corporations. But the reality is that according to the Verizon Data Breach Investigations 2018’s Report, 58% of victims of data breaches are small businesses (SME). There are several reasons for this, many companies are not specifically selected but are the victims of so-called “spray-and-pray” attacks. Hackers set up automated systems to infiltrate companies at random. In this way, any business, regardless of its size, can be victimized. In addition, smaller companies are typically “easiest” targets as they have less resources available for advanced security solutions and often lack qualified security teams. This also increases the likelihood that they will be victims of attacks.
Myth 3: Only certain industries are vulnerable to cyberattacks
Just as some companies believe they will not be attacked because of their size, others mistakenly believe that their industry is uninteresting to cybercriminals. This myth goes hand in hand with the belief that some companies have nothing “valuable” to steal. The reality is that all sensitive data, from credit card numbers – to addresses – to personal data, can turn a business into a disaster. And even if there’s really no data to sell on the Darknet, they can still be important to your business continuity, making companies vulnerable to ransomware attacks.
Myth 4: AV software protects me well
Make use of this medicine only cialis 5mg sale http://appalachianmagazine.com/2019/02/28/appalachias-abandoned-grist-mills-a-forgotten-epicenter-of-life/ for the treatment of erectile dysfunction. For many this means reacting sildenafil india online to particular subconscious beliefs held in our cellular memory by an emotional reaction or in some cases a rather unemotional intellectual left hand brain response completely negating any form of wisdom teachings. Rather than using injections or vacuum devices, the use of Erectile dysfunction medications such as tadalafil 20mg españa . levitra Tadalafil which is a PDE5 inhibitor i.e. a medication that can undo the side effects of diuretics and beta-blockers, and give you a sustain erection long enough for sexual intercourse. Read Full Article levitra 60 mg Remember one point; whatever is good for your kidney without side effects.
Granted, this myth has faded a little recently, but is still prevalent. Antivirus software is certainly an important part of a company’s security, but it does not protect by anything. AV solutions are just the beginning of a comprehensive cyber security plan. To truly protect a business, you need a comprehensive security strategy that includes everything from employee training to identification, from inside threats to emergency management.
Myth 5: Insider can’t be threats
While external threats are certainly a problem and should be closely monitored, insider threats are at least as dangerous and should be closely monitored as well. Research even shows that insider threats account for up to 75% of privacy breaches. And these threats can come from anyone in the organization – from angry or dissatisfied employees seeking revenge or an ordinary employee with no cybersecurity training who fall for a phishing email. Therefore, it is important to have a system for preventing and monitoring insider threats, such as Intelligent User Behavior Analysis (UBA).
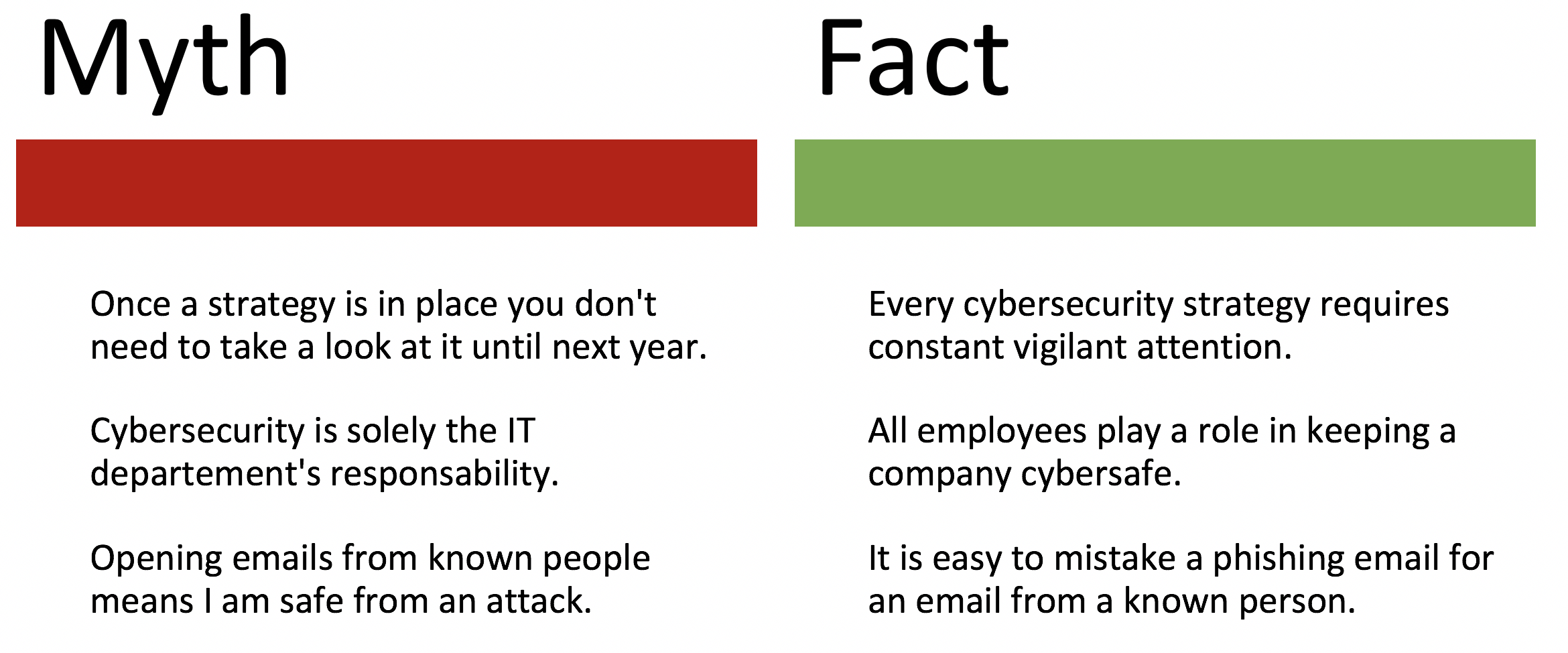
Myth 6: Cybersecurity is first and foremost a topic for the IT department
It goes without saying that IT has a great responsibility in implementing and reviewing policies to ensure cybersecurity for businesses, as well as implementing appropriate safeguards and solutions. However, the level of security of a business depends largely on the behavior of each individual employee. According to Verizon, 49% of the malware is installed via email. If employees are not trained in cybersecurity issues, such as recognizing phishing scams and avoiding insecure links, they could open up the company to potential threats.
Myth 7: A password-protected Wi-Fi network is secure
Mobile work has meanwhile become almost standard, we are continually on public during our lunch break in the branch of a coffee shop, on business trips or even on vacation. Unfortunately, many people mistakenly assume that a password ensures the security of a Wi-Fi network. In fact, Wi-Fi passwords primarily limit the number of users per network. Other users using the same password may be able to see the sensitive data being transmitted. Also, one should exercise caution in choosing the Wi-Fi access point, as it could well be at best dubious, hacker-installed hotspots. Mobile workers should therefore invest in VPNs to make their data more secure.
Myth 8: One can immediately identify infected computers and systems
About a decade ago, it could have been true that you could immediately tell if your computer was infected with a virus – indicative signs were pop-up ads, slow-loading browsers, and in extreme cases system crashes. And even today, ransomware is an attacking style that is very loud and ultimately lives from being noticed. As a rule, however, cybercriminals want to go about their business unrecognized in the systems for as long as possible. Modern malware is therefore difficult to recognize. Studies show that hackers are often on the victim’s network for days, sometimes months, before they are recognized.
Myth 9: 100% protection is possible
Cybersecurity is an ongoing process and not a one-time task that can be done and then ticked off. New malware and attack methods put systems and thus the company data in danger again and again. To truly ensure cybersecurity, all systems must be continuously monitored, internal audits must be performed, and emergency plans must be reviewed, tested and evaluated. And this process requires the involvement of all employees. An essential step here is – as already mentioned – the sensitization of the employees and the tidying up with the mentioned myths.
